Privileged Access
Breaches Are Inevitable. Damage Is Not.
Enforce least privilege
Apply least privilege security controls. Protect privileged access across all identities, infrastructure and apps, from the endpoint to the cloud.
Defend against attacks
Protect against the leading cause of breaches — compromised identities and credentials.
Enable the digital business
Deliver digital experiences that balance security and a frictionless experience.
Satisfy audit and compliance
A unified solution to address identity-oriented audit and compliance requirements.
Stop attackers in their tracks
CyberArk Privileged Access Management solutions address a wide range of use cases to secure privileged credentials and secrets wherever they exist: on-premises, in the cloud, and anywhere in between.
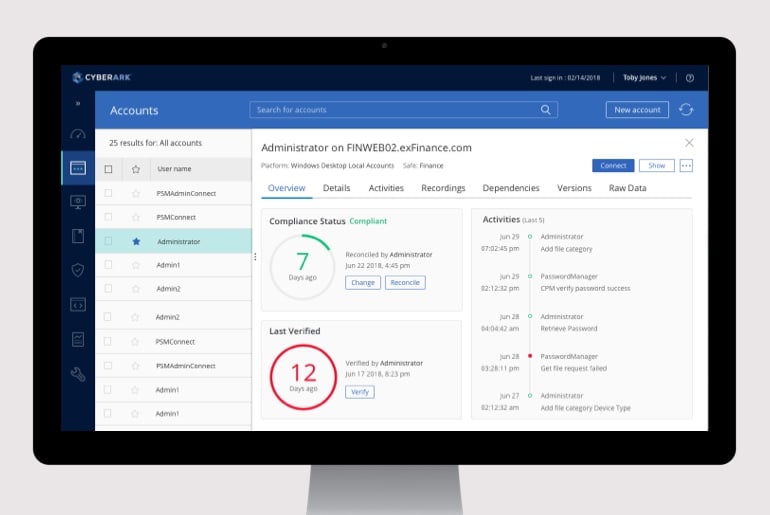
Privileged Access Manager
Continuously discover and manage privileged accounts and credentials, isolate and monitor privileged sessions and remediate risky activities across environments.
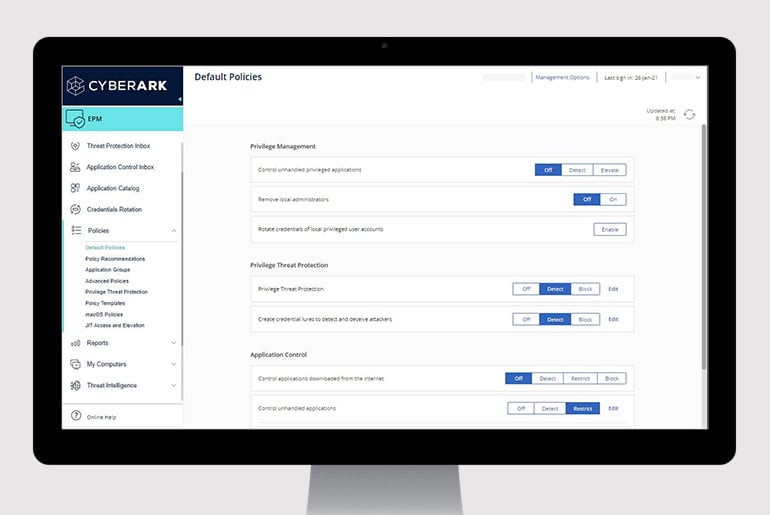
Endpoint Privilege Manager
Enforce least privilege, control applications and prevent credential theft on Windows and Mac desktops and Windows servers to contain attacks.

Vendor Privileged Access Manager
Enable secure remote vendor access to the most sensitive IT assets managed by CyberArk, without the need for VPNs, agents or passwords.
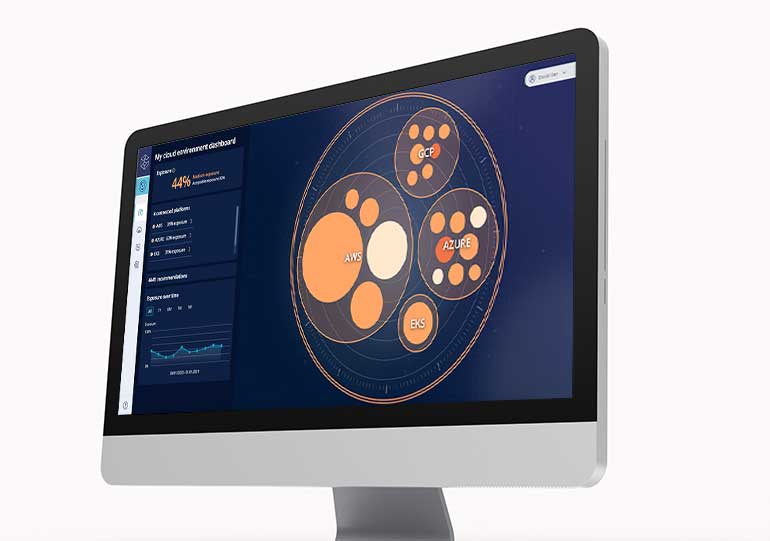
Cloud Entitlements Manager
Improve visibility through continuous, AI-powered detection and remediation of hidden, misconfigured and unused permissions across cloud environments.
Secure from all angles
Here’s just a few more ways we can help you move fearlessly forward in a digital world.
Drive operational efficiencies
Reduce complexity and burden on IT while improving protection of the business.
Secure your distributed workforce
Enable users access across any device, anywhere at just the right time.
Stop ransomware
Prevent lateral movement with 100% success against more than 3 million forms of ransomware.
Identity security centered on
intelligent privilege controls

CyberArk named a Leader in the 2023 Gartner® Magic Quadrant™ for Privileged Access Management – again.
Request a demo
Manage privileged accounts and credentials
Enforce least privilege at the endpoint
Remove excessive cloud permissions
Enable secure remote vendor access















