Credential Providers
A los desarrolladores y a los equipos de seguridad les encanta lo fácil que es eliminar las credenciales incrustadas en el código en una amplia gama de aplicaciones mediante integraciones listas para usar.

Credential Providers
Permita que las aplicaciones accedan de forma segura a los secretos que necesitan
Administre, rote y proteja los secretos utilizados por las aplicaciones comerciales (COTS), RPA, Java, .Net, scripts de automatización y otras identidades no humanas.

“La extensibilidad de CyberArk Secrets Manager ha supuesto una gran ventaja para nosotros. Las integraciones listas para usar con software de terceros han simplificado la forma de integrar de manera segura estas aplicaciones con el resto de nuestra cartera, lo cual es fantástico».
Responsable de seguridad de la información de un destacado hospital de Estados Unidos
CyberArk Marketplace
Navegue por nuestro Marketplace en línea para encontrar integraciones.
Visite Marketplace
















Recupere de forma segura las credenciales en tiempo de ejecución
Evite la exposición de credenciales incrustadas en el código en aplicaciones estáticas de misión crítica.
Proteja el acceso a las credenciales
Las contraseñas almacenadas en CyberArk Digital Vault se pueden recuperar en Credential Provider y, a continuación, se puede acceder a ellas mediante aplicaciones remotas autorizadas.
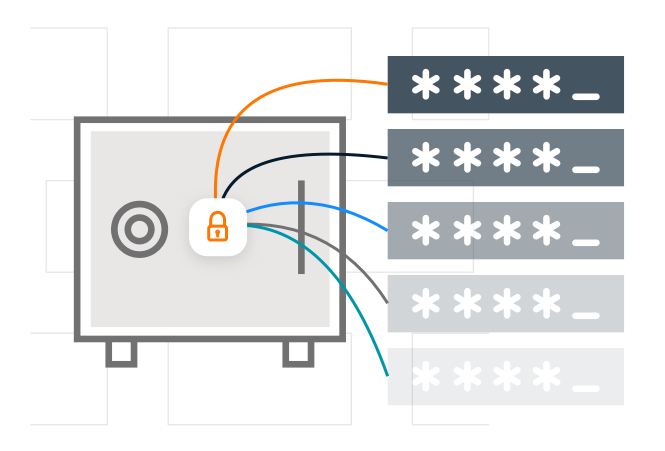
Acceso controlado
El mínimo privilegio permite a cada aplicación recibir la contraseña específica que ha solicitado y nada más.
Autenticación sólida
Utiliza las características nativas de las cargas de trabajo de las aplicaciones para aplicar una autenticación sólida a las aplicaciones y eliminar el «secreto cero».

Alta fiabilidad
Las credenciales almacenadas en caché localmente garantizan una alta disponibilidad, la continuidad del negocio y el máximo rendimiento para las aplicaciones de misión crítica de la empresa.

Auditorías completas
Los registros de auditoría rastrean el acceso a las contraseñas, lo que proporciona una completa supervisión y rendición de cuentas de cada contraseña solicitada por cada aplicación.

Una Seguridad de la Identidad que le conoce pero que no le detiene
Descubra todas las formas en las que CyberArk le ofrece tranquilidad para avanzar sin miedo.
Explorar
recursos
relacionados
Céntrese en dirigir su negocio, no en reaccionar a las amenazas
Solicitar demostración
Evite que las aplicaciones de misión crítica expongan las credenciales incrustadas en el código
Simplifique la protección de las aplicaciones con la más amplia gama de integraciones listas para usar
Manténgase un paso por delante de las auditorías y el cumplimiento

Regístrese para una demostración personalizada
CyberArk Has Patent Rights Relating To This Technology – https://www.cyberark.com/patents



