Secure Cloud Access
멀티클라우드 환경에 대한 액세스를 보호하고, 위험을 줄이며, 네이티브 사용자 경험을 유지합니다.
Secure Cloud Access
클라우드 자산 전반에서 지속적으로 액세스 보호
멀티클라우드 환경 전반에 걸쳐 제로 스탠딩 권한으로 클라우드 콘솔 및 서비스에 대한 안전한 네이티브 액세스 제공
일관성
하나의 플랫폼에서 멀티클라우드 액세스 정책을 적용합니다.
네이티브
네이티브 액세스로 활용도를 높입니다.
실용적
필요할 때 권한을 상승시키는 최소 권한을 구현하여 위험을 줄입니다.
클라우드 액세스 제어에 대한 전체적인 접근 방식
생산성에 영향을 미치지 않으면서 멀티 클라우드 자산에 제로 스탠딩 권한 구현
클라우드에 네이티브 액세스
에이전트가 없다면 문제도 일어나지 않습니다. 멀티 클라우드 콘솔에 대한 네이티브 액세스만 보호
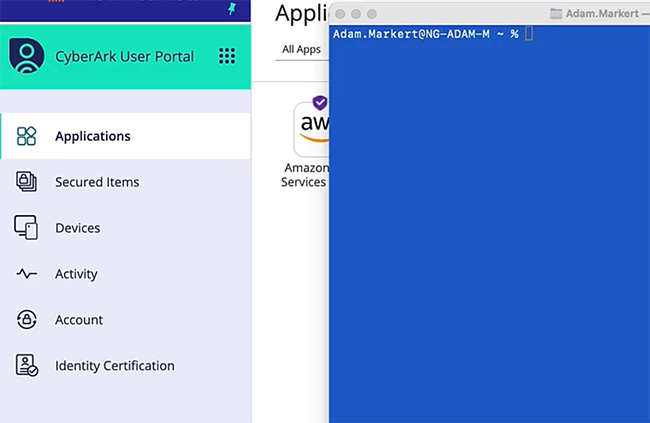
전역 규모로 액세스 정책 정의
중앙 집중식 보안 정책을 설정하여 사용자가 클라우드 콘솔에 액세스하는 방법 정의
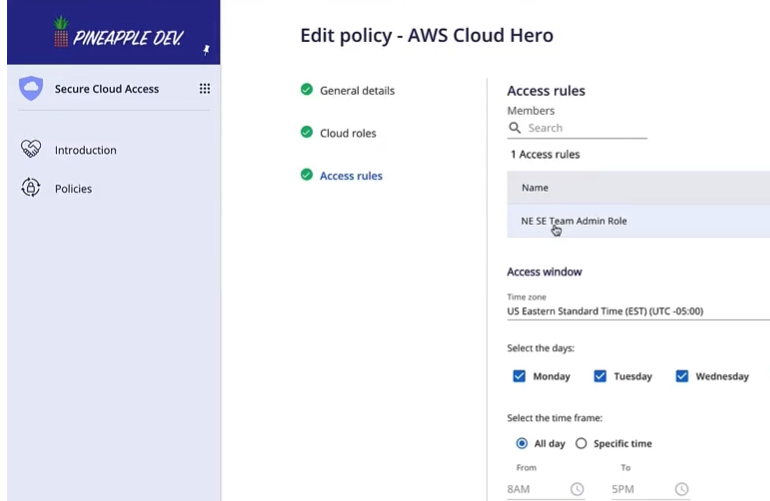
동적 긴급 액세스
엔지니어가 위험한 상황(critsit)에서 안전하게 액세스를 요청하고 신속하게 받을 수 있음
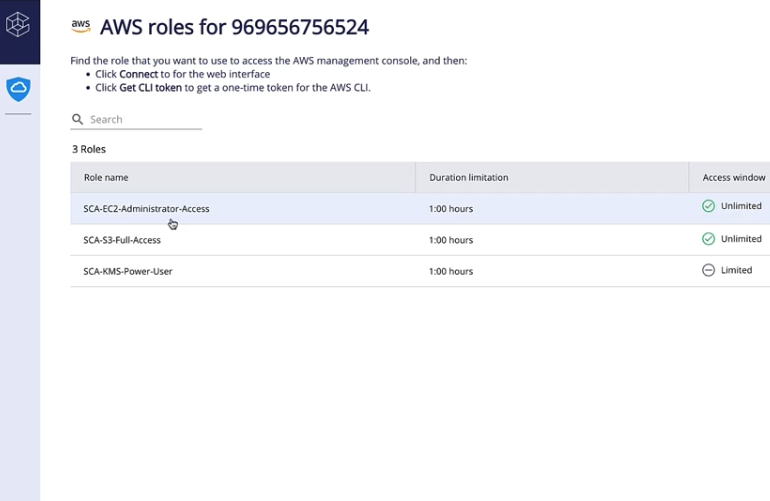
원활한 통합
서비스 데스크 또는 ChatOps 도구와 통합하여 액세스 요청을 효율적으로 처리
관련 리소스 살펴보기
CyberArk가 생산성에 영향을 미치지 않으면서 클라우드 보안을 지원하는 방법 알아보기
