A phishing attack is a social engineering tactic commonly used to steal confidential data or deliver ransomware or some other form of malware. The term is a play on the word fishing, meaning the attacker throws out a baited hook and waits for the victim to bite.
The attacker typically poses as a trusted source (bank, service provider, retailer, etc.) and sends an intended victim an email, a mobile text message, instant message, or social media post with a legitimate-looking but malicious link. When the victim clicks on the link, malware downloads to their computer or mobile device. Many phishing messages include misspelled words, poor grammar, or bogus-looking URLs and ar easily spotted as phony. Other phishing messages appear authentic and can be challenging to detect at first glance.
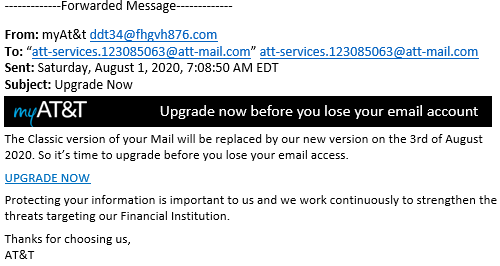
An example of a phony phishing email posted by AT&T
Phishing Attack Types
There are many varieties of phishing attacks, including general phishing attacks, spear phishing attacks and whaling attacks. With a phishing attack, the attacker casts a wide net, spraying fake messages to a large audience, hoping to dupe as many victims as possible. With a spear phishing attack, the attacker narrowly targets specific individuals within an organization. With a whaling attack, the attacker goes after “big whales,” targeting high-worth or high-profile individuals like corporate executives or government leaders.
Phishing attacks are one of the oldest forms of cyberattacks, dating back to the 1990s. They remain one of the most common types of attacks and are used in a wide variety of exploits. According to Verizon’s 2021 Data Breach Investigation Report, phishing is the most frequently deployed attack action and is present in 36% of all breaches.
Phishing Attack Costs
Phishing attacks are also one of the costliest forms of cyberattacks. A 2021 Ponemon Institute report revealed large U.S. companies lose an average of $14.8 million a year to phishing.
Some of the most financially damaging phishing attacks over the years include:
- A $100 million attack against Facebook and Google.
- A $75 million attack against Crelan Bank in Belgium.
- A $61 million attack against FACC, an Austrian airline component manufacturer.
- A $47 million attack against Ubiquiti Networks, a networking equipment provider.
- A $44 million attack against Leoni AG, a German cable manufacturer.
Phishing and Ransomware
Ransomware perpetrators often carry out phishing attacks to install encryption malware. According to a 2021 Statista study, phishing emails are the most common ransomware delivery vector and leveraged in 54% of all ransomware outbreaks. The notorious Ryuk attack, for example, used phishing emails to lure victims, ultimately netted over $150 million in ransom payments.
Threat actors also execute phishing campaigns in the wake of ransomware attacks, preying on fear and uncertainty. For example, in July 2021, the ransomware-as-a-service operator REvil waged an attack against the IT Management Platform service provider Kaseya that impacted over 1,000 companies across the globe. Shortly after the ransomware attack, other scammers initiated a phishing campaign, sending susceptible Kaseya customers bogus emails disguised as Kaseya software update notifications.
Phishing Attack Prevention and Mitigation
Commonsense tips for preventing and mitigating phishing attacks include:
- Educate employees about phishing scams and help them recognize suspicious emails.
- Use antivirus solutions and endpoint protection solutions to harden devices and block malware at the point of entry.
- Implement multi-factor authentication solutions to prevent threat actors from accessing applications and penetrating systems if credentials are compromised.