Privileged Access
침해는 피할 수 없습니다. 하지만 피해는 피할 수 있습니다.

최소 권한 시행
최소 권한 보안 제어를 적용합니다. 엔드포인트부터 클라우드에 이르기까지 모든 아이덴티티, 인프라 및 앱에서 특권 액세스를 보호합니다.
공격 방어
침해의 주요 원인인 아이덴티티 및 자격 증명 유출을 예방합니다.
디지털 비즈니스 활성화
보안과 원활한 경험이 균형 잡혀 있는 디지털 경험을 제공합니다.
감사 및 규정 준수 충족
아이덴티티 중심 감사 및 규정 준수 요구 사항을 해결하는 통합 솔루션입니다.
공격자를 즉시 차단합니다.
CyberArk Privileged Access Management 솔루션은 온프레미스, 클라우드 및 그 사이 어디든 존재하는 모든 곳에서 권한 있는 자격 증명과 비밀정보를 보호합니다.
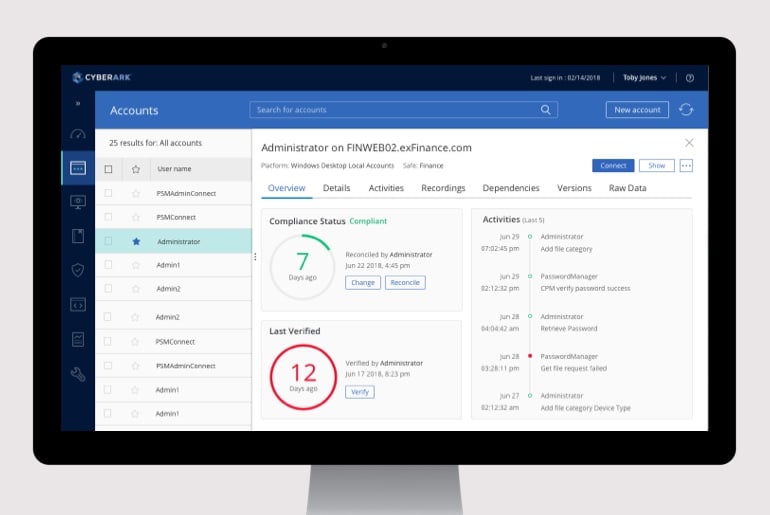
Privileged Access Manager
특권 계정과 자격 증명을 지속적으로 탐색 및 관리하고, 특권 세션을 격리 및 모니터링함으로써 환경 전반에서 위험한 활동을 해결합니다.
Endpoint Privilege Manager
Windows, Mac 데스크톱과 Windows 서버에서 최소 권한을 적용하고 애플리케이션을 제어하며 자격 증명 도용을 방지함으로써 공격을 억제합니다.
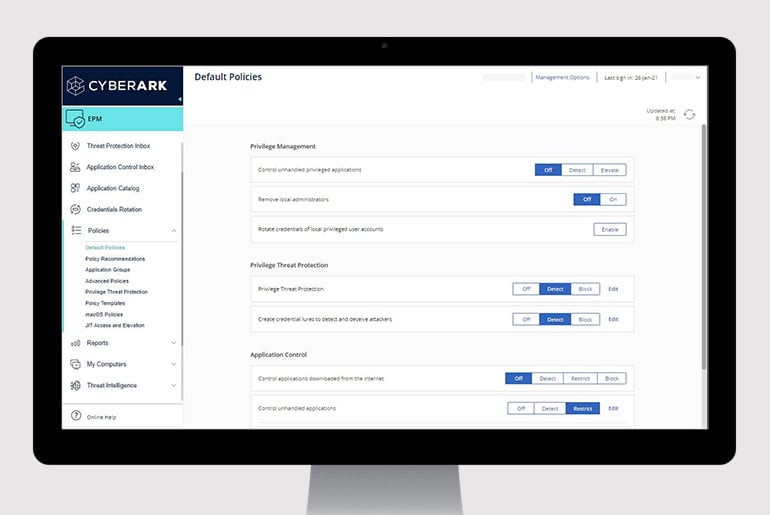

Vendor Privileged Access Manager
VPN, 에이전트 또는 암호 없이 CyberArk에서 관리하는 가장 민감한 IT 자산에 대한 안전한 원격 공급업체 액세스를 지원합니다.
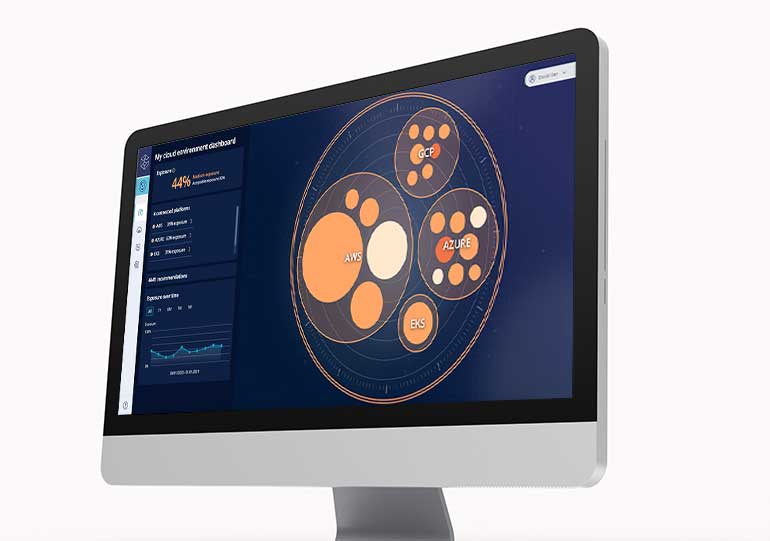
Secure Cloud Access
다중 클라우드 환경의 모든 계층에 대해 Zero Standing Privileges로 필요한 순간에만 네이티브 액세스를 보장합니다.
모든 방면에서 보안
디지털 세상으로 전환하는데 도움이 되는 몇 가지 방법을 소개합니다.
지능형 권한 제어를 중심으로 하는 아이덴티티 보안

CyberArk가 Gartner® Magic Quadrant™의 Privileged Access Management 부문 리더로 다시 한 번 선정되었습니다.
관련
리소스 살펴보기
데모 요청
특권 계정 및 자격 증명 관리
엔드포인트에서 최소 권한 시행
과도한 클라우드 권한 제거
원격 공급업체 액세스 보안 활성화
CyberArk Has Patent Rights Relating To This Technology – https://www.cyberark.com/patents















