Multi-Factor Authentication
Secure access to your apps and websites with a broad range of secondary authentication methods.

Multi-Factor Authentication
Added security. When you needed it.
Protect your apps with multi-factor authentication that adjusts based on risk.
Secure
Eliminate reliance on passwords with a broad set of secondary authentication factors.
Flexible
Customize embedded authentication flows to your needs, including the types and number of challenges.
Frictionless
Limit challenges to risky access requests based on context and user behavior.
Adaptive Authentication
Use AI to intelligently assign risk to each access request.
Extra layer of protection
Device, network, and user behavior context
Dynamic access policies
80%
of breaches involve the use of lost or stolen credentials.*
Threats knock but no one answers
Multi-Factor Authentication provides added protection to keep attackers out.
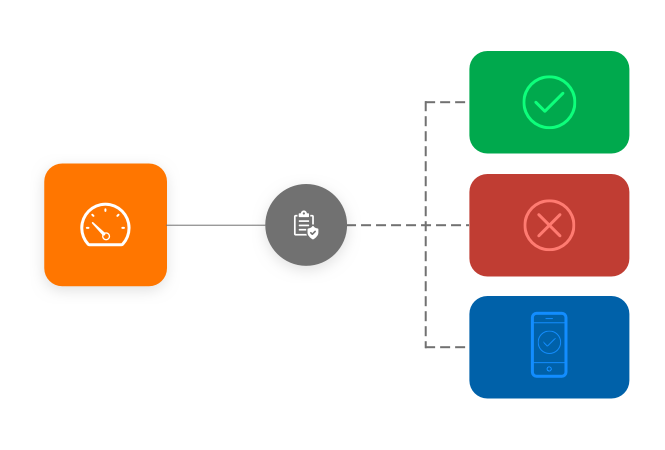
Risk-based policies
Enforce MFA challenges based on contextual information and behavioral signals.
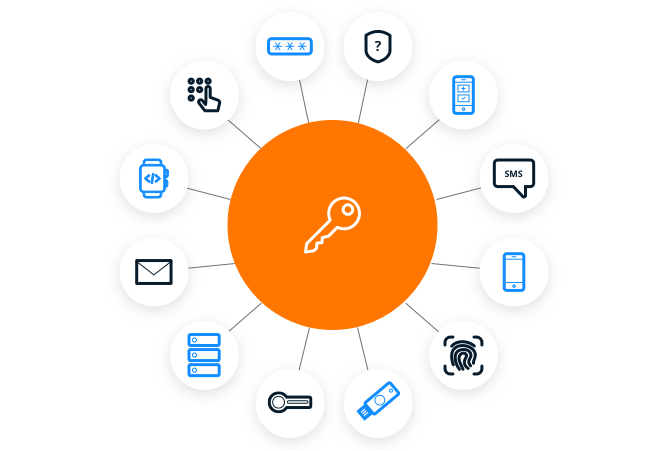
Authentication factors
Validate customer identities with a broad range of supported authentication methods, including passwordless factors, physical tokens, and authenticator apps.
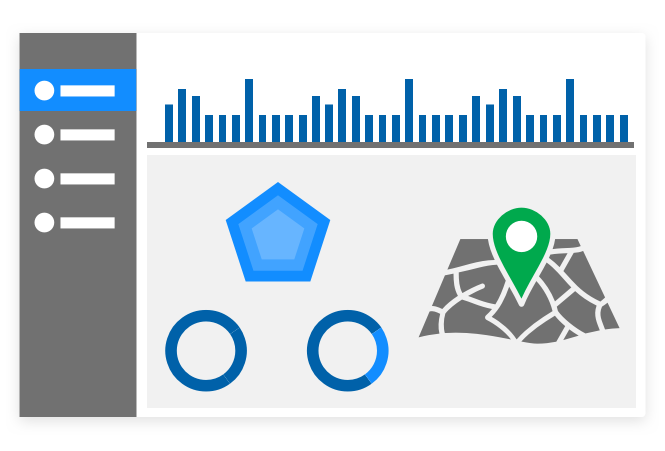
In-depth reports
Analyze access requests against historical patterns, visualize trends in real-time, and investigate failed or high-risk access attempts.
REST APIs
Leverage the CyberArk REST API to deploy MFA in your applications to customize end-user experience.

Dynamic access policies
Define when to challenge users with MFA based on pre-defined conditions such as location, device, day of week, time of day and even risky user behavior.
Identity security that knows you but doesn’t slow you
Explore all the ways CyberArk gives you peace of mind to move fearlessly forward.
Get a 30-day trial
Add an additional layer of authentication to your apps
Reduce the risk of compromised credentials
Reduce friction for users with context-based access controls
*SOURCE: EMA, Contextual Awareness: Advancing Identity and Access Management to the Next Level of Security Effectiveness, Steve Brasen, March 2020