Securing IoT and OT
Broaden your business horizons while minimizing your risk.
New devices and technologies have changed the it landscape
Connected devices are a huge asset for innovation—and yet can be a massive headache for IT. Keeping track of all these devices and ensuring compliance has become increasingly difficult.
51 Percent
Of all networked devices will be machine to machine by 2022.*
15 Percent
Of IoT device owners fail to change default passwords.**
90 Percent
Of organizations had at least one OT system intrusion in the last year.†
Shore up entry points to your most critical assets
IoT and OT devices present a unique set of problems for security and operations teams.
Centrally manage privileged credentials
Keep your business safe by preventing the malicious use of privileged accounts and credentials—a common path to an organization’s most valuable assets—especially with the proliferation of new devices joining your networks.
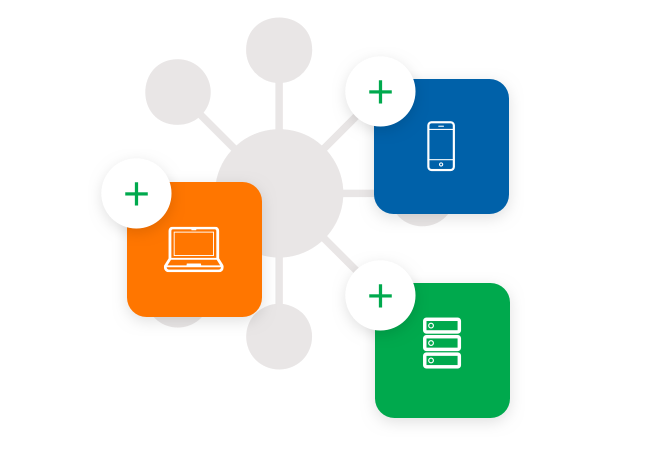
Discover accounts
Discover devices connecting to the network and automatically onboard those credentials, manage lifecycle, vulnerability and patch management for IoT devices plus detect and respond to threats in real time.

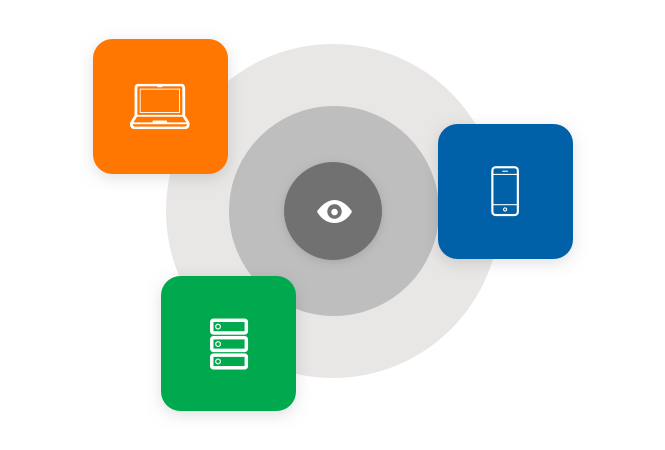
Session isolation, monitoring and recording
Anytime an OT environment or IoT device is accessed, enable automatic isolation, monitoring and recording. This approach gives you complete control—without disrupting end-user workflow.
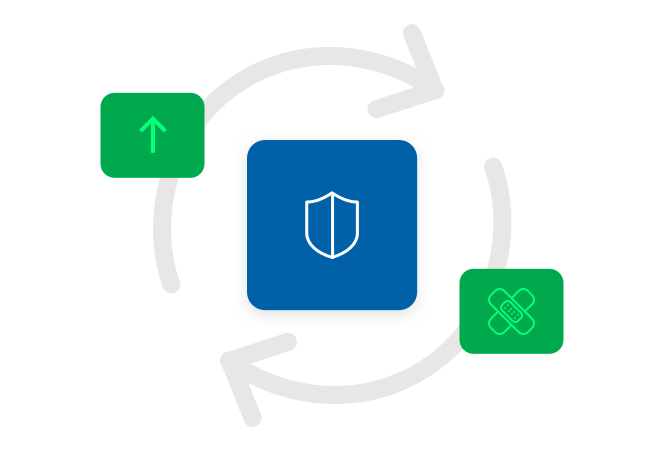
Patch and manage IoT and OT connections
To keep them running smoothly and securely, it’s important to consistently upgrade and patch your systems. Just be sure you have the right tools in place to reduce the risk of an attack.
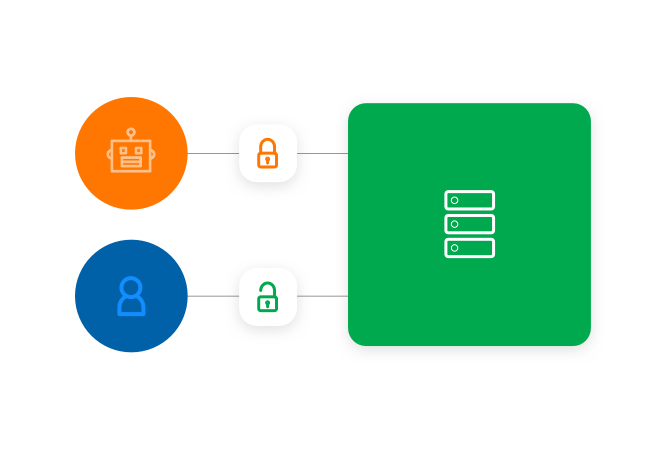
Provision access to external vendors
Provide continuous controlled access to systems and devices, for human and non-human users alike.
Explore
related
resources
Focus on running your business,
not reacting to threats lorem
Request a demo
Identify and secure devices with privileged accounts and credentials
Leverage threat analytics & detection
Enhance security while maintaining productivity
SOURCE: *https://www.juniperresearch.com/press/iot-connections-to-reach-83-bn-by-2024
SOURCE: ** http://blog.ptsecurity.com/2017/06/practical-ways-to-misuse-router.html
SOURCE: †https://www.itweb.co.za/content/rxP3jqBmNJAMA2ye