A recently published Ponemon study revealed that 63 percent of organizations have experienced an advanced attack within the last 12 months. Industry reports note an average time of 146 to 170 days to detect an attack, 39 days to contain it and 43 days to remediate. Time seems to be on the side of an attacker.
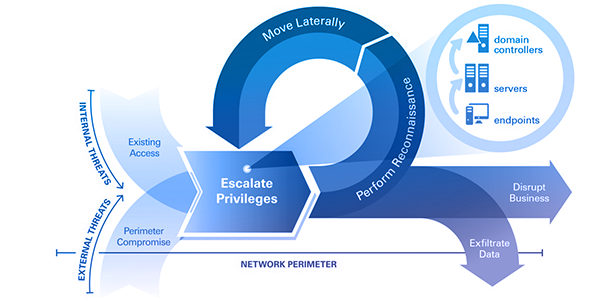
Motivated attackers will find a way to break through the network perimeter – but how are they able to prolong their undetected presence once inside? CyberArk has a dedicated team that studies and analyzes attacks that occur in the wild. Based on ongoing research and findings, we’ve learned that in most attack scenarios, there is a clear attack path that cyber criminals follow to help hide their tracks. Privileged accounts are at the center of this path.
In a short, three-minute video, our Senior Product Marketing Manager Jessica Stanford outlines each key phase of this attack lifecycle:
How common is this? In a highly publicized, first-ever talk by the head of the NSA’s Tailored Access Operations – the US government’s top hacking team responsible for breaking into the systems of foreign adversaries – Rob Joyce detailed each phase of a typical attack. When talking about the “reconnaissance phase,” a theme immediately emerged: the privileged credentials of network administrators and others with high levels of network access are critical for gaining access to key systems, and ultimately, the heart of the enterprise. He stressed the importance of establishing processes and procedures to closely monitor what is going on inside the network – making sure to understand what is normal and what isn’t. For example, are authorized users going to normal places within the network and operating under the norms of those particular credentials? Are they accessing new or different things that they shouldn’t be?
Joyce also revealed that his team “loves” to find admin or other credentials hardcoded into scripts or devices, as they provide covert pathways for attackers to move laterally throughout a network. He specifically noted Pass-the-Hash attacks, commenting with the right credentials, attackers “can pivot like mad throughout the network.” He warned that even temporary “cracks” – small vulnerabilities that only exist for a few hours – are exactly what advanced attackers seek. Even the smallest “crack” of one stolen credential can be enough to take down an entire organization if proper security measures are not in place. If that’s the case, think of the irreversible damage that can be done in 146+ days!
With privilege clearly at the heart of the cyber attack lifecycle, we encourage you to learn more about how CyberArk solutions can help your organization break the chain with privileged account security and detect attacks sooner. You can learn more here.

























