RPA and bot automation
Automate privileged access to avoid manually rotating credentials for robotic process automation (RPA), bots and virtual agents.
Take less time to secure virtual agents
Eliminate deployment delays – run and scale RPA faster, and safer, when you centrally secure credentials. Simplify deployments with out-of-the-box integrations so you can address security issues before you even know you have them.
92% of Respondents
Cite they’re planning to extend automation use cases.*
Tier zero
RPA, bots and automation processes—whether unattended or attended— require high levels of privilege to do their jobs.
<33% of Respondents
Say they’re very confident they can identify the number of privileged accounts and credentials used within applications and processes such as RPA.**
Securely accelerate RPA, bot and virtual agent adoption
RPA and bot automation deliver new levels of efficiency—but they also expose security risks.
Robots require privileged credentials
Attackers can gain control of robots and then access the systems the bot’s access by stealing unsecured RPA admin and bot credentials. Remove privileged credentials from automation scripts and local secrets stores to prevent bots, attended or unattended, from being easy targets. Plus ensure citizen developers only get the credentials they need.
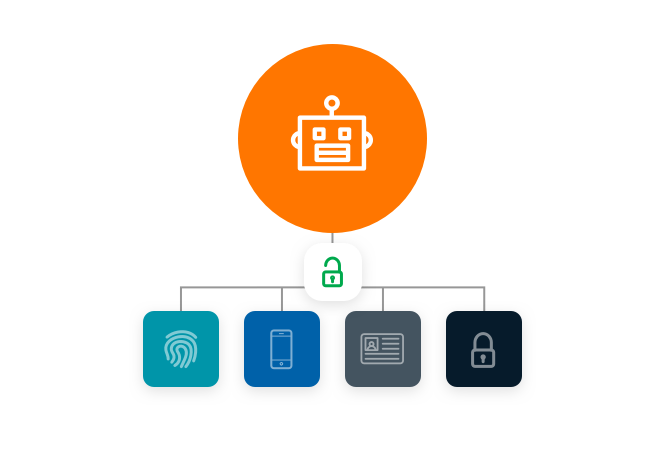
RPA increases attack surface
Organizations gain immense efficiencies with thousands, or even a few, software robots. But they can increase the attack surface, so as a best practice only grant robots privileged access to the specific applications, they need to perform their tasks.
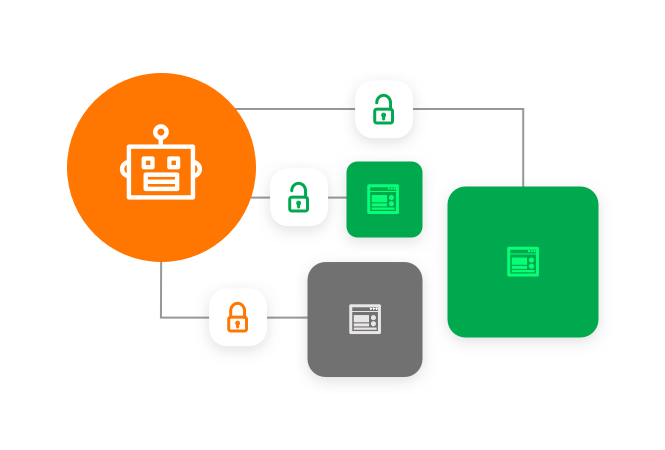
RPA credentials must be managed
Why use RPA to automate processes and then manually assign, manage and update the credentials they need to perform their tasks? Centrally managing credentials across the enterprise’s RPA, bots and virtual agents increases efficiency, strengthens security and simplifies compliance.
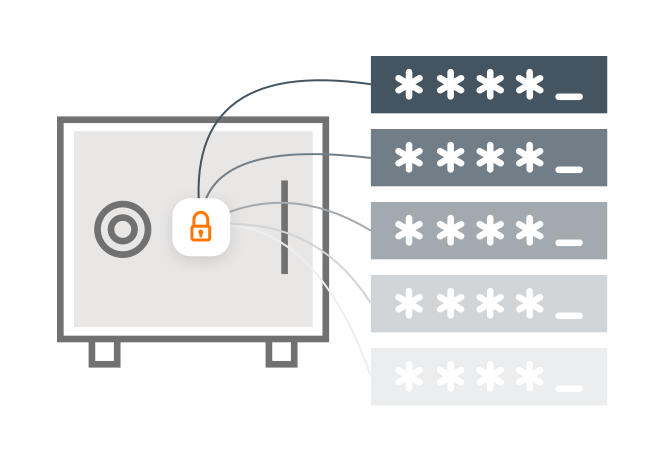
Identity security fundamentals

Identity Security: Why it Matters and Why Now
Put Identity Security first without putting productivity second.
Request a demo
Prevent bots from becoming easy targets
Decrease vulnerabilities while Improving operational efficiency
Strengthen security and simplify compliance
*SOURCE: https://www.cyberark.com/resources/blog/5-best-practices-for-robotic-process-automation-security
**SOURCE: CyberArk Global Advanced Threat Landscape 2019 Report