Secure Cloud Access
Secure access to multicloud environments, reduce risk and maintain native user experience
Secure Cloud Access
Secure access consistently across your cloud estate
Provide secure, native access to cloud consoles and services with Zero Standing Privileges across your multicloud environment
Consistent
Apply multicloud access policies from one platform.
Native
Drive utilization with Native Access.
Pragmatic
Reduce risk by implementing Least Privilege with on-demand elevation.
Holistic approach to control for cloud access
Implement Zero Standing Privileges in your multicloud estate without impacting productivity
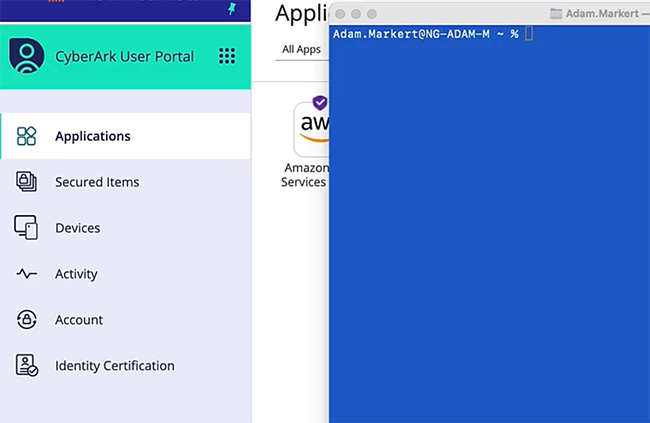
Native Access to Cloud
No agents, no drama. Just secure native access to Multicloud consoles
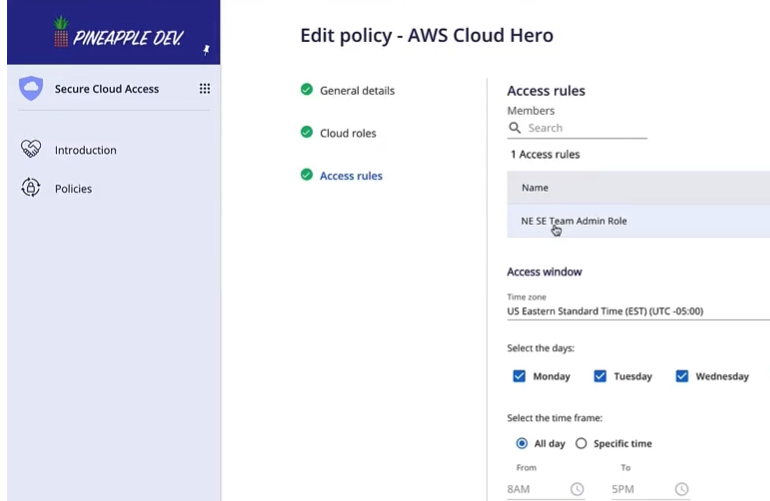
Define Access Policies Globally
Define how users access cloud consoles by setting centralized secure policy
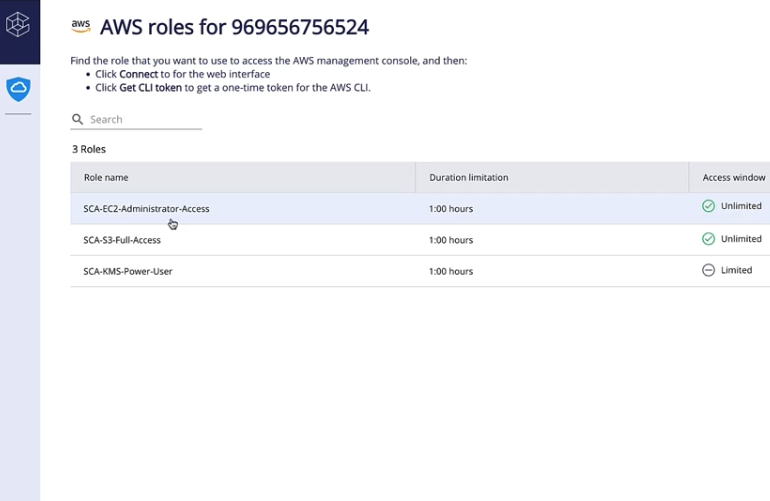
Zero Standing Privileges
Remove all standing permissions. Grant entitlements Just-in-time

Dynamic Break-Glass Access
Engineers can securely request and rapidly receive access in critical situations (critsit)
Seamless integration
Integrate with service desk or ChatOps tooling to efficiently handle access requests
Explore
related
resources
Learn how CyberArk can help you secure your cloud without impacting productivity