Privileged Access Manager
Keep your business and its most valuable assets secure. Preventing malicious account or credential access starts with comprehensive Privileged Access Management.
Privileged Access Manager
Mitigate risks, maximize productivity
Don’t settle for less than the industry leader in Privileged Access Management (PAM).
Enable the digital business
Securely authenticate users with VPN-less access from a single web portal.
Outsmart the smartest attackers
Stay one step ahead of cyberattacks. And your competition.
Keep unauthorized users out
Detect and stop threats in real-time
Easily deploy PAM as-a-Service or host it in your own environment
79%
of enterprises have had an identity-related breach within the past two years.*
600%
increase in cybercrime activity since the COVID-19 Pandemic began.*
The best defense is good cybersecurity
Manage privileged access and minimize risk.
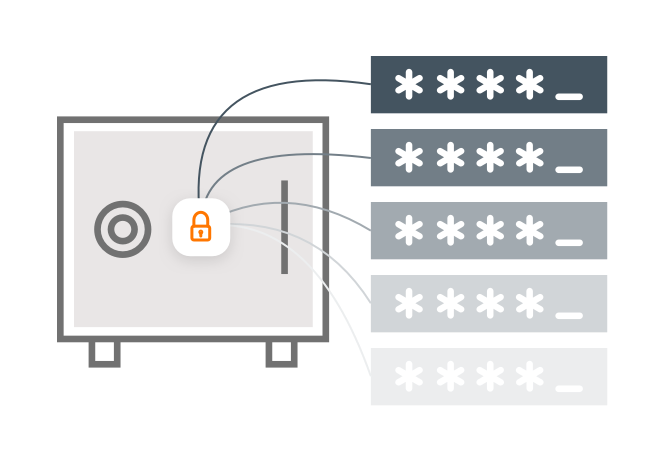
Manage privileged credentials
Automatically discover and onboard privileged credentials and secrets used by human and non-human identities. Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes, and more. Automated password rotation helps strengthen security while eliminating time-intensive, manual processes for the IT teams.
Isolate & monitor sessions
Maintain compliance with recorded key events and tamper-resistant audits. Establish secure, isolated remote sessions and record all activity during that session. End users never directly connect to target systems, reducing the risk of malware. Session recordings are securely and centrally stored to make it easy for security, audit and compliance to increase accountability and compliance.

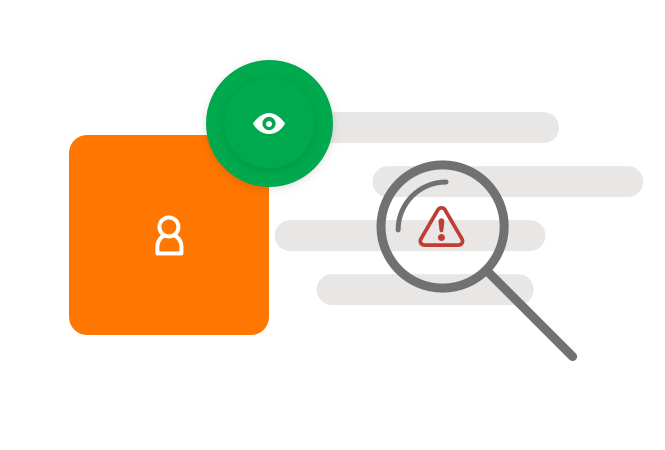
Threat detection & response
Automatically discover and onboard unmanaged privileged accounts and credentials. Detect anomalous behavior and indicators of compromise with policy-driven remediation capabilities.
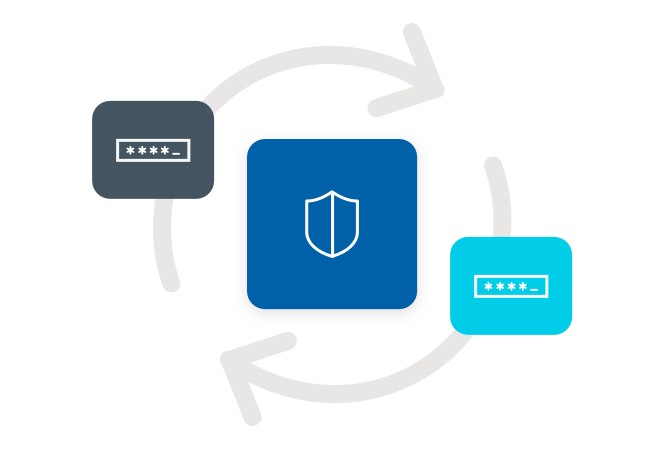
Manage nomadic devices
Enforce security policies and rotate account credentials on endpoints that aren’t always connected to the enterprise network.
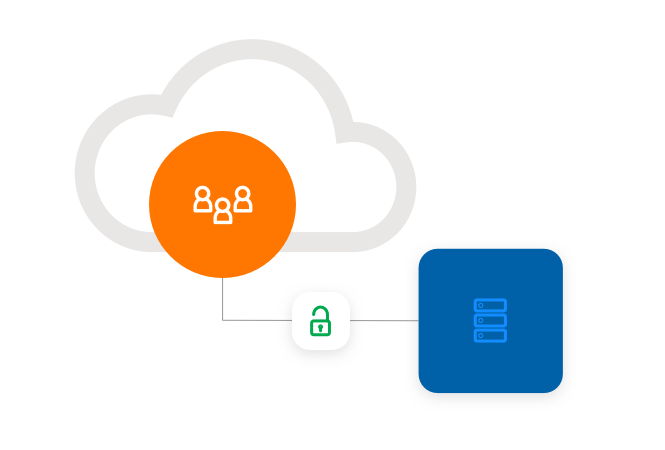
Remote access to PAM
Enable secure access for remote employees and external vendors to Privileged Access Manager, no matter where they are. VPN-less, agent-less, password-less.
Adaptive MFA & SSO
Validate privileged users with context-aware Adaptive Multi-Factor Authentication and secure access to business resources with Single Sign-On.
Deploy as SaaS or self-hosted
Implement and expand PAM with confidence. The CyberArk Blueprint has successfully secured thousands of customer environments and counting.
SaaS
Easily secure and manage privileged accounts, credentials and secrets with our PAM-as-a-service solution.
Automate upgrades and patches for reduced total cost of ownership
Secure, SOC 2 type 2 compliant services with a certified 99.95% SLA for uptime
Hands-on guidance with CyberArk jump start
Self-hosted
Protect, monitor and control privileged access, with on-site deployment.
Deploy in your datacenter, private or public cloud, to meet regulatory compliance or organizational needs
Confidently migrate to SaaS with the backing of CyberArk’s proven expertise
Multi-region deployments fit to scale

"CyberArk has been the best vendor I have worked with in my 20+ year IT career. CyberArk delivers great products that lead the industry in managing privileged access."
IT Security Manager, Security and Risk Management

"With CyberArk, we are confident that we have implemented technology that will work with us as our business grows and develops."
Jean-Pierre Blanc, Bouygues Telecom

"This isn’t just a compliance check-box exercise, we’re actively designing and aligning policies to cybersecurity best practices to strengthen our overall security posture and align internal teams."
Joel Harris, Manager

"CyberArk gave us the visibility and granular control needed to implement both least privilege and ‘default deny’ application control with minimal disruption to the organization."
Ken Brown, CISO

"With RPA and Cloud migrations, credentials are becoming more and more spread out away from 'normal' controls. CyberArk can spread out to cover all of the scenarios in a standard way."
Information Security Consultant, Enterprise Cybersecurity Solutions Technologies
Request a demo
Prevent credential exposure, isolate critical assets
Monitor and audit sessions for suspicious activity
Remediate risky behavior, automatically
Continuously manage and rotate credentials
Secure remote access to PAM
Frictionless and secure access to business resources

Register here for a personalized demo
*SOURCE: December, 2019. The State of Identity: How Security Teams are Addressing Risk
*SOURCE: IBM Security Cost of a Data Breach Report, 2020















