
Simply put, APIs (short for application programming interface) are how machines, cloud workloads, automation and other non-human entities communicate with one another. They also represent an access point to highly sensitive company data and services. Almost every organization uses these machine interfaces, and their usage is only growing because they are essential to digital transformation and automation initiatives. Machine identities and APIs are closely connected because any programmatic interface accessing important data or protected services needs an identity, such as a password, API key or another secret.
While essential and prevalent, APIs are potential attack vectors when not properly protected via machine identity security best practices. They can be exploited to expose sensitive data (e.g., customer lists, personally identifiable information (PII) and credit card details) while enabling application-to-application communication.
How Cyber Criminals Abuse and Exploit APIs
Cyberattackers are constantly attempting to steal and compromise the powerful secrets that allow machines to run APIs as the stolen machine identity. By doing so, they can assume the identity of whatever had that secret and use it to gain more access and privileges to reach their goal. Along the way, they could, for instance, enable a script or a user to stop or start a virtual server, copy a database or even wipe out entire cloud workloads.
Fortunately for attackers, developers under pressure to move quickly often take shortcuts, such as hard-coding API keys and other secrets. Take the Uber breach reported in 2022 as an example: the attacker found and used hard-coded secrets embedded in a PowerShell script to gain high-level access and escalate privileges.
Since many security teams view API security as a code issue, they may not know how many APIs and API secrets exist within their organization, where they’re located or how they are used. A 2023 Ponemon Institute study reveals that more than half of IT and IT security professionals say it’s challenging to discover and inventory all APIs. The many third parties connected to an organization’s APIs exacerbate this challenge. And as attackers shift left into software development and testing environments, insecure API design and functionality significantly increase software supply chain risks.
These factors may be why organizations are only confident in preventing 26% of API attacks and believe that only 21% of such attacks can be effectively detected and contained, according to the same Ponemon study. As API access to critical resources continues to sprawl, it’s time for security to change how they think about APIs.
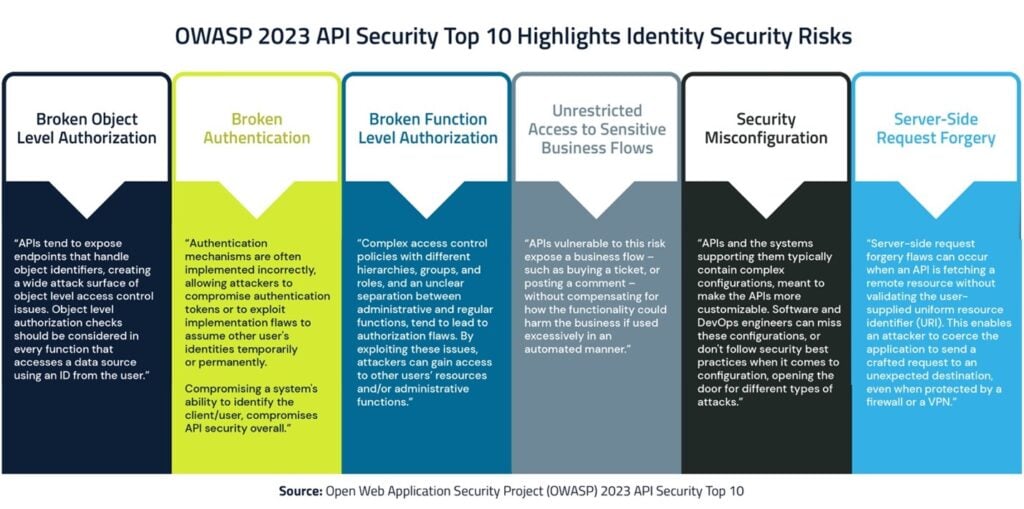
Top API Identity Security Risks
Most of today’s top API security risks relate to identity. Yet, critical identity security controls in many organizations, including least privilege enforcement and continuous monitoring, only cover human users. This means that secrets used by applications, scripts and other machine identities – that outnumber human identities 45:1 – are exposed. Attackers can “hook” API keys and other secrets through phishing attacks, find them embedded in applications, automation scripts and DevOps tools and steal them from public repositories like GitHub to access sensitive company assets. Artificial intelligence (AI) advancements have made it even easier for cybercriminals to automate and scale identity-based attacks.
The Open Web Application Security Project (OWASP), a recognized industry source for software security research, highlights some recent pressing API identity security issues in its 2023 API Security Top 10 list, including those outlined below.
Simplify API Security with Centralized Secrets Management
Forward-looking organizations are working to understand how digital business characteristics impact their security practices and move toward a Zero Trust model. As part of this, they view human and non-human identity security as equally important. They’re tackling secrets management challenges by centralizing and automating how applications, DevOps and automation tools use API keys and other secrets to access databases, cloud environments and other sensitive resources. With this approach, they only have one program to support but can gain the full visibility, audit trails and policy enforcement capabilities they need to ensure nothing falls through the cracks.
Companies we work with have also seen how centralized secrets management simplifies how development and security teams protect applications, CI/CD pipelines and the software supply chain. They’re doing this with out-of-the-box integrations with existing tools and platforms so that tasks like secrets rotation, audit and data collection automatically run in the background without impacting developer workflows.
Properly securing APIs and other non-human identities is imperative for business. Organizations that do it right will be better positioned to defend against cyberattacks, drive operational efficiencies, satisfy audit and compliance requirements and enable innovation.
John Walsh is a senior product marketing manager at CyberArk.























