CyberArk Workforce Identity Security vs. OneLogin IAM
Because Reliability, Innovation, and Security Come First.
CyberArk Workforce Identity Security reimagines access management with a smooth, reliable user experience, modern integrated controls, and our security-first DNA. In contrast, the OneLogin IAM solution has struggled with service outages, a stagnant innovation roadmap, and gaps in delivering proactive security.
Empower your workforce with simple and secure access to business resources with CyberArk Workforce Identity.





1
User Experience and Reliability — CyberArk is Ready, Always.
CyberArk delivers a smooth user experience with an industry-leading 99.99% uptime SLA. Whether for day-to-day authentication, password management, or accessing privileged software, targets, or cloud infrastructure, CyberArk enables flexible, easy access while simplifying identity management for IT and security teams. Our differentiated user experience, unified Identity Security Platform, and high up time means that you can trust CyberArk to be ready.
In contrast, OneLogin has faced challenges with service disruptions and UI inconsistencies. Customers have expressed frustration with outages, leading to unexpected downtime and impact on productivity. Its interface lacks refinement needed for smooth integration and user satisfaction.
The Takeaway
CyberArk ensures exceptional reliability, reducing downtime and a smooth experience for both end-users and IT teams. OneLogin’s record of outages and usability issues can disrupt operations, and erode user confidence.
2
Reimagine Workforce Identity Security with Modern, Integrated Controls.
MFA and SSO are foundational controls, but alone, cannot stop today’s attacks on identities. The CyberArk solution includes built-in Workforce Password Management, which secures legacy and non-SSO applications by automatically vaulting and managing credentials. Endpoint Privilege Manager enforces least privilege policies at the device level. This approach is validated by industry best practices recommending endpoint-level controls as a core part of modern IAM. These controls help secure your workforce across all of their access use-cases, ensuring robust security without hindering user experience.
In contrast, OneLogin has struggled with continuous innovation. Customers cite incremental product updates without clear differentiation or modernization. Advanced capabilities require premium/pro licensing or additional tools (e.g. EPM for Mac OS), leading to complexity and potential gaps in coverage.
The Takeaway
By delivering modern, integrated controls that simplify access management and proactively reduce risk, CyberArk helps organizations evolve their IAM strategy with a future-proof platform that goes beyond the basics of MFA and SSO.
3
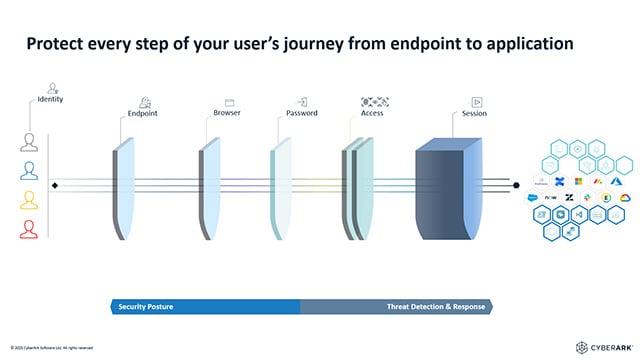
Security-First: Protect Users from Endpoint to Application.
While many IAM providers secure the initial login, the reality is that many attacks target users before and after authentication. CyberArk Workforce Identity Security delivers protection with a unique combination of session monitoring, endpoint & device trust, and by assessing adaptive risk.
Session Monitoring & Real-Time Control:
CyberArk Secure Web Sessions offers visibility into user activity after the login. Proactive security controls such as extra authentication triggers for risky behaviors.
Endpoint & Device Trust:
CyberArk ensures that only secure, verified devices and browsers access critical resources, mitigating the risk from compromised endpoints.
Adaptive Privilege Enforcement:
User access can be automatically limited based on context and risk level. These automations help you implement least privilege principle to minimize the risk of lateral movement and data exfiltration.
CyberArk Workforce Identity solution—and Endpoint Privilege Manager—are FedRAMP High authorized. This certification underscores our security-first approach to help organizations drive fearlessly forward.
In contrast, OneLogin has not achieved full FedRAMP authorization and has faced scrutiny for a reactive security posture. Advanced security capabilities, such as adaptive MFA, enhanced session monitoring, and deeper threat detection integration requires additional modules or higher-tier licensing, which adds complexity in budgeting and implementation.
The Takeaway
CyberArk protects your users before, during, and after the login. With end-to-end threat mitigation that continuously adapts to risk, this means that even if an attacker bypasses initial defenses, they are met with real-time controls that protect your organization throughout the user’s journey.
Some other companies in the industry use tools like Okta or One Identity, but CyberArk’s solutions are designed with a security-first mindset and unified within an identity security platform that provides defense-in-depth protection, secures workstations and servers, implements least privilege and integrates very well with on-premises and cloud environments – all of which was critical for us. ”
Timo Lu, Head of IT
Heng Leong Hang