Adaptive
Multi-Factor Authentication
Secure access to your entire organization with a broad range of secondary authentication methods with CyberArk Identity Adaptive Multi-Factor Authentication.
Adaptive
Multi-Factor Authentication
Adaptive MFA adds security with less hassle
Strengthen access controls with adaptive secondary authentication.
Secure authentication
Eliminate reliance on passwords with a broad set of authentication factors.
Protect everything
Secure your entire enterprise to reduce the risk of security breaches.
Simplify user experience
Limit challenges to risky access requests based on context and behavior.
Adaptive authentication
Use AI to intelligently assign risk to each access event.
Extra layer of protection
Device, network, and user behavior context
Dynamic access policies
90%
of organizations employing contextually-aware automation can quantify reduced IT effort and costs.*
74%
reduction in unauthorized users accessing business apps when behavioral biometric authentication is adopted.*
Threats knock but no one answers
Adaptive MFA provides added protection to keep attackers out.
MFA Everywhere
Adaptive Multi-Factor Authentication secures your entire organization: Apps, VPNs, Workstations, Mac and Windows Endpoints, Virtual Desktops and RADIUS servers.
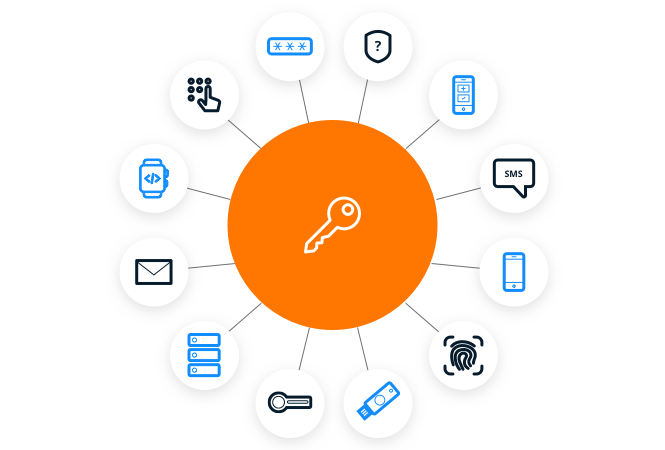
Authentication Factors
Adaptive MFA supports a comprehensive range of authentication methods to make it easy for users, customers, and partners to securely access applications and data.
Context-based
Analyze access requests against historical patterns, assign risk to each login attempt, and create access policies triggered by anomalous behavior.

Endpoint Protection
Endpoint MFA and Secure Desktop offerings significantly reduce the risk of attacks that leverage compromised credentials and ransomware to access corporate applications and data from end-user devices.

Easy Administration
Includes features to help administrators streamline secondary authentication controls and enhance the end-user experience.
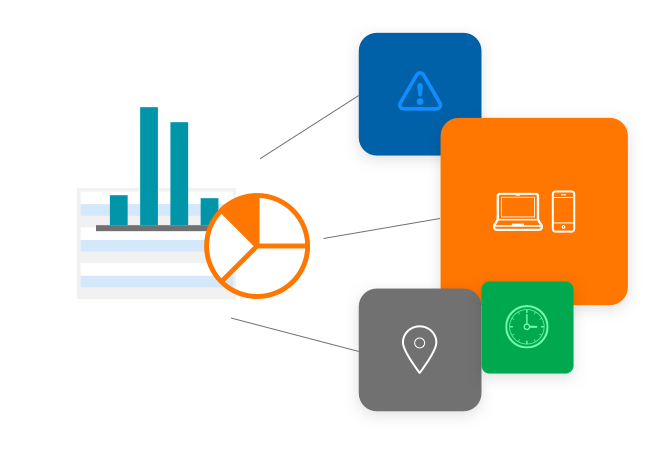
Dynamic access policies
Use contextual information, such as user risk, location, device and time of day to determine which authentication factors to apply to a particular user in a particular situation.

"CyberArk has been the best vendor I have worked with in my 20+ year IT career. CyberArk delivers great products that lead the industry in managing privileged access."
IT Security Manager, Security and Risk Management

"With CyberArk, we are confident that we have implemented technology that will work with us as our business grows and develops."
Jean-Pierre Blanc, Bouygues Telecom

"This isn’t just a compliance check-box exercise, we’re actively designing and aligning policies to cybersecurity best practices to strengthen our overall security posture and align internal teams."
Joel Harris, Manager

"CyberArk gave us the visibility and granular control needed to implement both least privilege and ‘default deny’ application control with minimal disruption to the organization."
Ken Brown, CISO

"With RPA and Cloud migrations, credentials are becoming more and more spread out away from 'normal' controls. CyberArk can spread out to cover all of the scenarios in a standard way."
Information Security Consultant, Enterprise Cybersecurity Solutions Technologies
Identity security that knows you but doesn’t slow you
Explore all the ways CyberArk gives you peace of mind to move fearlessly forward.
Plans
Get a 30-day trial
Add an additional layer of authentication
Reduce the risk of compromised credentials
Reduce friction for users with context-based risk scoring
*SOURCE: EMA, Contextual Awareness: Advancing Identity and Access Management to the Next Level of Security Effectiveness, Steve Brasen, March 2020