Security standards and frameworks
Design the kind of framework that enables authorized users to drive your business—and prevents attackers from disrupting it.
Can your framework stand up to evolving cyber threats?
From new tactics to new techniques, expect cyber attacker to innovate just as fast as your business.
13% Increase
From 2016-2020 of targeted attacks exploiting user privileges.*
Average 57% of vulnerabilities
In 2020 were classified as being ‘critical’ or ‘high severity’.*
Nearly 4,000 vulnerabilities
Disclosed in 2020 can be described as ‘worst of the worst’.*
Safeguard your most critical systems and assets
Implement identity security controls that work across multiple security standards and frameworks.
Secure privileged access
Compromised privileged identities are the leading cause of security breaches—which makes privileged access one of the biggest priorities for your business. The most secure privileged access approach prevents human and machine identities from having more access to systems and resources than they need.

Enforce least privilege
The least privilege principle ensures the right access is provided to the right users for the right amount of time. The practice extends beyond human access to include applications, systems or connected devices that require privileges or permissions to perform a required task.
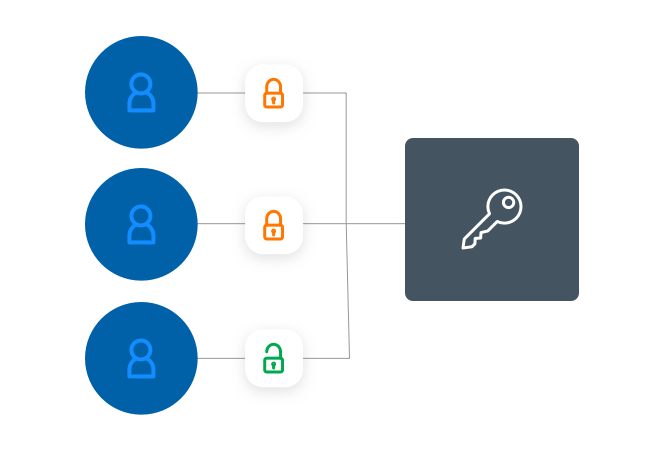
Enable strong authentication
Multi-Factor Authentication (MFA) and Single Sign-On (SSO) are two best practices for ensuring your users are who they claim to be. MFA secures your entire organization: Apps, VPNs, Workstations, etc. SSO provides secure and frictionless sign-in experience for both internal and external users.

Broker secure sessions
In a secure brokered session, privileged users are able to connect to systems without exposing credentials to end-users or their machines. The approach ensures accountability, identifies risk, and produces a tamper-proof audit trail.
Integrate with compliance tools
To address IT audit and compliance requirements, our Identity Security platform integrates with compliance and reporting tools. Consequently, you’ll be able to provide comprehensive and integrated reports on privileged access and session activities to address questions and pass an IT audit.

Top compliance assets
Cyber-attacks connected to the Society of Worldwide Interbank Financial Telecommunication (SWIFT) continue to emerge. As a high-value target for attackers, the SWIFT network provides a community of financial institutions worldwide the ability to exchange sensitive information relating to international financial transactions.
Learn how you can leverage Privileged Access Management to assist with SWIFT Customer Security Controls Framework (CSCF) compliance.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) 27002 standard is an internationally acclaimed standard of best practice for information security. Following this internationally-recognized standard helps organizations meet contractual obligations with customers and business partners. For service providers, from cloud data centers to law offices, their license to operate increasingly requires them to prove they are responsible stewards of sensitive information for a global clientele. Auditors worldwide also rely on ISO security 27002 as a basis for evaluating controls and/or verifying compliance to various regulations and standards.
Learn how you can meet requirements. Download the privileged access management whitepaper.
The National Institute of Standards and Technology (NIST) has provided technical requirements for federal agencies implementing digital identity services. The 800-63-3 Digital Identity guidelines have expanded on a singular concept of level of assurance (LOA) for all electronic authentication of digital identities that was originally introduced in 800-63-2.
The new guidelines cover three processes, Identity Proofing, Digital Authentication and Federated Identity Management.
Learn more in our 4-part blog series.
The National Institute of Standards and Technology (NIST) has created a special publication on Zero Trust Architecture in an effort to help businesses mitigate the risk of cyber-attacks in the modernized environments.
Learn how you can implement a more modern security approach.
Request a Demo
Improve confidence in achieving audit/compliance requirements
Reduce audit and compliance costs and time
Remediate audit gaps before they are flagged