Securing Red Hat OpenShift Virtualization with CyberArk: Identity Security for VMs and Containers

As organizations modernize IT infrastructure, many are adopting platforms like Red Hat OpenShift Virtualization to run both traditional virtual machines (VMs) and containerized workloads on a single, unified environment. This hybrid model enables greater flexibility and efficiency, but it also introduces significant security complexity.
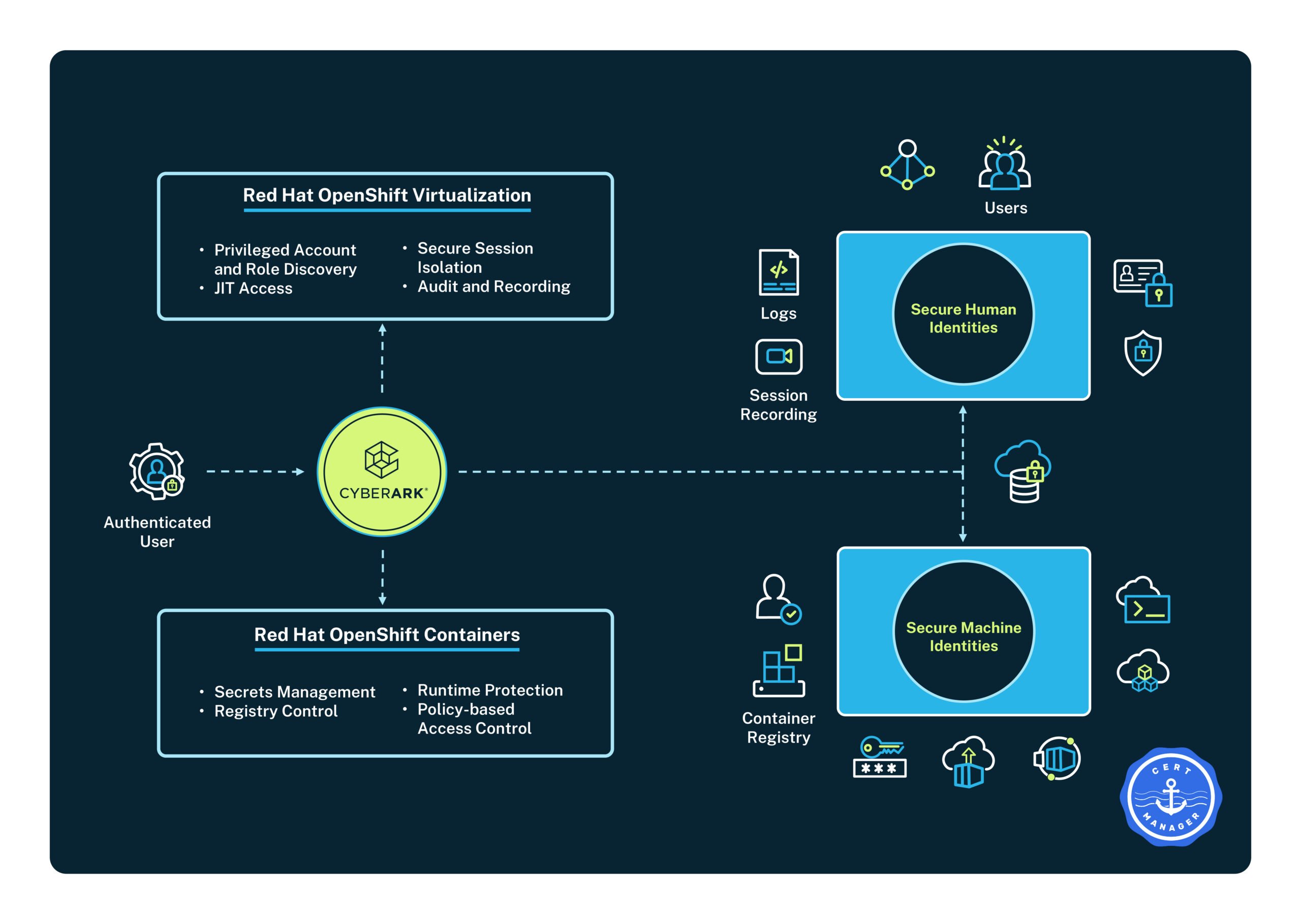
Managing privileged access across VMs, containers and the Red Hat OpenShift control plane requires a consistent, scalable and secure approach. That’s where CyberArk comes in.
The CyberArk Identity Security Platform delivers powerful protection for Red Hat OpenShift Virtualization environments, securing access to virtual machines, Red Hat OpenShift components and containerized applications. Whether you’re migrating VMs or securing secrets for containers on platforms like Red Hat OpenShift, CyberArk helps reduce risk and accelerate modernization.
Securing Access to Red Hat OpenShift
Before securing workloads, it’s critical to protect access to the platform itself. Red Hat OpenShift provides powerful APIs and control plane components that can be used to create, scale and manage both VMs and containers. Misused access here can lead to serious breaches.
CyberArk protects platform-level access with:
- Centralized Identity Management: Manages human and machine identities with strong authentication, granular permissions and access policies.
- Session Isolation for Platform Access: Logs and isolates access to Red Hat OpenShift itself, whether through web UI, command line or API.
- Policy-Based Controls: Enforces role-based and attribute-based access across users, services and namespaces.
By implementing these controls, organizations can significantly reduce the risk of misconfigurations, unauthorized changes and privilege escalation within Red Hat OpenShift.
Securing Privileged Access to Virtual Machines on Red Hat OpenShift
VMs remain critical for many enterprise workloads—and securing access to them is essential. Red Hat OpenShift Virtualization allows organizations to migrate or provision VMs directly within Red Hat OpenShift, but these VMs still require traditional security measures to prevent abuse of privileged credentials.
CyberArk secures VMs on Red Hat OpenShift Virtualization by:
- Privileged Account Discovery and Onboarding: Automatically identifies and brings under management privileged accounts associated with new or migrated VMs. This prevents unmanaged credentials from becoming hidden risks.
- Migrate to Just-in-Time Access: CyberArk helps organizations reduce risk by implementing just-in-time (JIT) access, where privileged access is granted only when needed, requires approval and expires automatically – eliminating standing access and minimizing the attack surface.
- Session Management and Isolation: CyberArk brokers privileged sessions to VMs, allowing organizations to isolate and monitor activity without exposing direct access.
- Session Recording and Audit: Every action taken on a VM is recorded and can be reviewed for compliance, incident response and forensic investigation.
These capabilities allow organizations to secure their VMs from the moment they are deployed on Red Hat OpenShift Virtualization—protecting sensitive data and ensuring operational accountability.
Deploying CyberArk on Red Hat OpenShift Virtualization
CyberArk doesn’t just secure workloads on Red Hat OpenShift—it can also be deployed as part of the platform itself. Running CyberArk components such as SaaS Connectors or the CyberArk Self-Hosted Solution on VMs inside Red Hat OpenShift Virtualization helps organizations simplify infrastructure while maintaining a strong security posture.
Benefits of deploying CyberArk on Red Hat OpenShift Virtualization:
- Unified Infrastructure: CyberArk runs within the same environment as the workloads it protects, simplifying platform operations.
- Flexible Deployment: Whether Red Hat OpenShift is running on-prem or in the cloud (e.g., via ROSA), CyberArk supports deployment in all environments.
- Scalable and Resilient: Leverage Red Hat OpenShift’s orchestration and monitoring features to scale and secure CyberArk services.
Running CyberArk on Red Hat OpenShift Virtualization allows security teams to consolidate tooling, reduce infrastructure sprawl and apply consistent policies across workloads and platforms.
Securing Secrets and Certificates in Containers on Red Hat OpenShift
While VMs continue to power critical workloads, containerized applications are rapidly becoming the engine of innovation. CyberArk helps secure both types of workloads on Red Hat OpenShift by protecting all machine identities. Secrets such as API keys, tokens, database credentials and TLS certificates are prime targets in modern attacks—and must be safeguarded throughout the CI/CD pipeline.
CyberArk helps more seamlessly extends security into this domain to manage secrets and certificates for containers running on Red Hat OpenShift:
- Secure Secrets Management: Centralized vaulting of API keys, database credentials and tokens used by containers and rotating the secrets periodically.
- Secrets Injection at Runtime: Securely inject secrets into containers without exposing them in code or CI/CD pipelines.
- Certificate Lifecycle Management: Automate certificate issuance, rotation and revocation for secure communication between services.
- Granular Access Policies: Control which workloads and services can access specific secrets, using role, label or identity-based rules.
By embedding secrets management directly into the DevOps toolchain and Red Hat OpenShift environment, CyberArk reduces risk without slowing down innovation.
Why CyberArk and Red Hat OpenShift Virtualization?
CyberArk delivers out-of-the-box capabilities that help organizations secure every aspect of their Red Hat OpenShift deployment—across VMs, containers, platform APIs and developer pipelines.
Key benefits include:
- Unified Security Posture: Consistent controls across virtualized and containerized workloads.
- Deployment Flexibility: Run CyberArk anywhere Red Hat OpenShift Virtualization runs—on-prem or cloud.
- Accelerated Migration: Securely onboard and manage privileged access for newly or migrated VMs.
- Cloud-Native Compatibility: Integrated secrets management and access controls for OpenShift-native apps and services.
- Audit Readiness: Full visibility into privileged sessions, access logs and secrets usage for compliance and governance.
Final Thoughts: End-to-End Identity Security for Hybrid Environments
CyberArk is more than just a privileged access solution—it’s a strategic enabler for hybrid and modern cloud-native environments. As organizations adopt platforms like Red Hat OpenShift to run VMs and containers on the same infrastructure, CyberArk provides the identity security foundation needed to protect users, workloads and infrastructure across the board.
From VM migration and access control to secrets management for containers, CyberArk ensures security doesn’t slow down transformation—it drives it.
CyberArk not only protects Red Hat OpenShift Virtualization and the VMs running on it, but also secures and manages secrets and certificates for containerized applications on Red Hat OpenShift. With a single platform for securing both human and machine identities, CyberArk empowers organizations to modernize with greater confidence.
Ready to secure your Red Hat OpenShift environment with CyberArk?
Niels van Bennekom is a manager of Tech Alliances Product Management, Corporate and Business Development at CyberArk.