Identity Compliance
Strengthen your security posture by enforcing least privilege, comply with regulatory requirements.

Identity Compliance
Centralized visibility and stronger control
Simplify your compliance initiatives while mitigating the risk of unauthorized, accumulated and overprivileged access.
Understand who has access to what
Discover user access and authorizations to various resources, including access to highly privileged accounts.
Continuously review access and enforce least privilege
Make informed decisions to continuously enforce least privilege and ensure users only have the access they need to do their jobs.
Demonstrate compliance
Leverage intelligent analytics to proactively detect risks and make critical remediation decisions to stay in compliance with the most stringent regulations.
By 2023, 75% of security failures will result from inadequate management of identities, access, and privileges—up 50% from 2020.*
-Gartner®
Keep auditors happy, keep attackers out
Identity Compliance Provides a Single Control Pane for Access and Compliance Management for All User Accounts and Privileges.
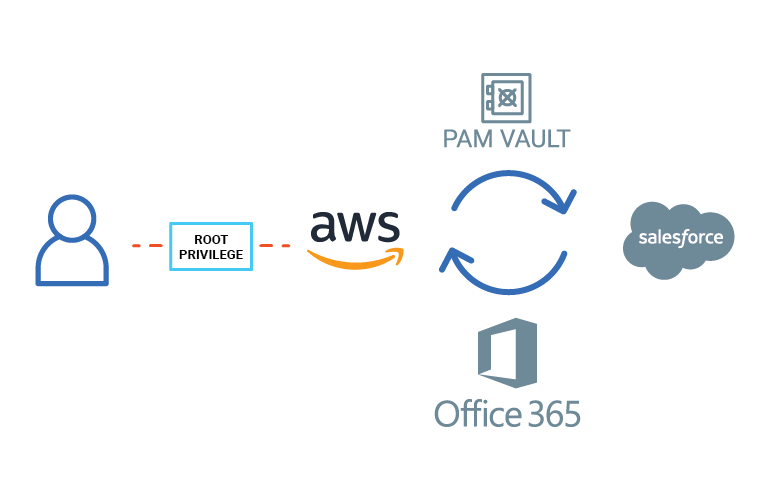
Access Discovery
Discover all the resources and entitlements granted to users within the organization including access to SaaS applications, and access to privileged accounts stored in CyberArk Privileged Vault.
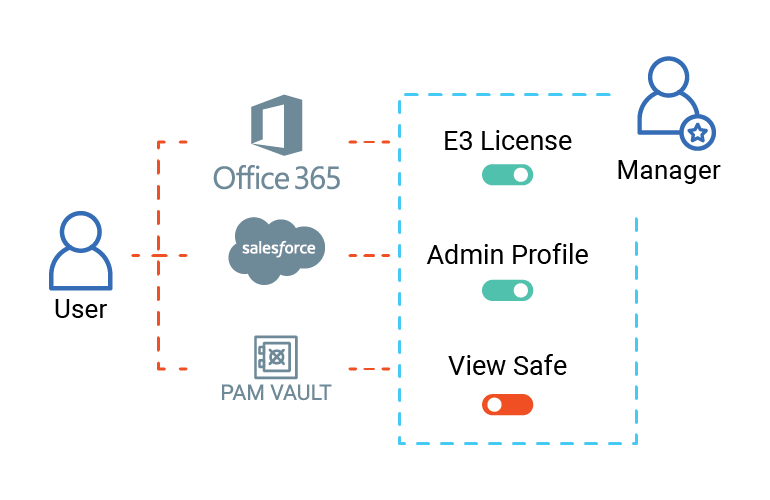
Access Certification
Periodically review, approve or revoke access privileges to applications and permissions to various safes within the CyberArk Privileged Vault. Leverage contextual information for these decisions with rich insights on access history and risk scores.
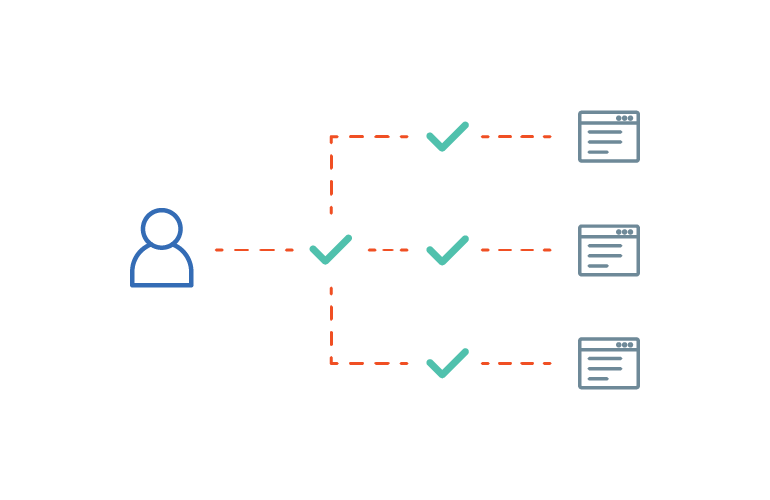
Analytics and Reporting
Access advanced analytics and dashboards to intelligently identify potential compliance issues, view detailed audit trails and create custom reports.

Access Automation
Integrate with CyberArk Identity Lifecycle Management to boost productivity by removing manual tasks, simplifying self-service access workflows, and automating onboarding and offboarding processes.
Advanced Workflows
Leverage CyberArk Identity Flows to orchestrate and automate the complex business processes involved in demonstrating regulatory compliance with no code workflows.
Continuously discover, certify, remediate and audit access
Extend the zero trust model across your enterprise by leveraging Identity Compliance for user access.
Plans
*GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
*Gartner, “Managing Privileged Access in Cloud Infrastructure”, June 9, 2020.