
The public cloud is empowering organizations to do incredible things, from exploring new realms in space to transforming cultures. This week at AWS re:Invent in Las Vegas, these real-world cloud innovation stories were on full display.
“Technology has changed how we explore our imagination together,” said Amazon Web Services (AWS) CEO Adam Selipsky in his keynote. “The world is all one neighborhood, and we can all come out and play.”
Companies of all sizes continue flocking to the cloud for its many business benefits: Reduced infrastructure costs, increased flexibility and more dynamic application development, to name a few. Selipsky shared how Airbnb — a company hit particularly hard by the pandemic — took advantage of cloud scalability to help weather the storm and make a remarkable comeback.
Virtually every organization now uses the cloud for some facet of their business — and most companies want to do even more. Especially now, “Businesses are leaning in [to the cloud] as we face economic uncertainty,” said Selipsky. “It can help them be prepared for anything.” He expects cloud adoption will continue to surge over the next five years, in which time the amount of data worldwide will double in a “data explosion.”
Explosive Cloud Growth Brings Benefits and Complications
But with “explosive” data growth come new security challenges. Leading cloud service providers (CSPs) like AWS have combined decades of innovation and technology to deliver modern platforms. And they continue to expand their offerings — from compute infrastructure like virtual machines (VMs), containers and services, to databases and other supporting IT assets — to help organizations achieve their goals even faster.
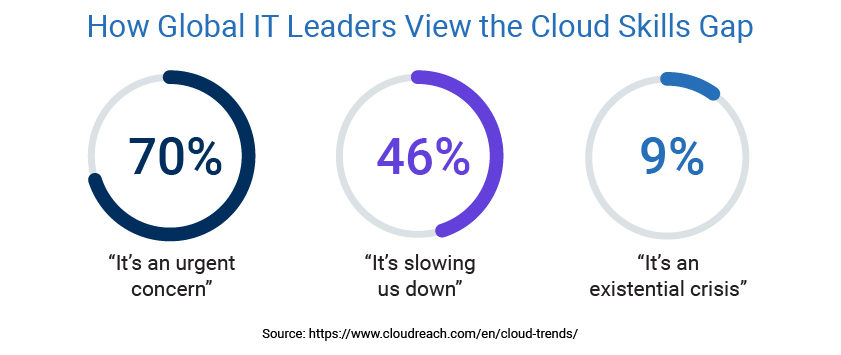
For one, there simply aren’t enough skilled cloud professionals to keep pace with this evolution. A recent study commissioned by AWS and Cloudreach found more than 70% of global IT leaders view the skills gap as an urgent concern, 46% believe it’s slowing them down and nine percent describe it as an “existential crisis” for their companies.
Modern cloud platforms combine decades of innovation and technology, and customer organizations have access to an ever-growing list of new offerings — from compute infrastructure like virtual machines (VMs), containers and services, to databases and other supporting IT assets — to help them achieve their goals even faster.
Even with highly skilled professionals at the helm, cloud migrations can be complicated — and even create friction between functional groups. For example, development teams may be eager to forge ahead quickly to accelerate their cloud-native DevOps practices, while security teams may want to proceed more slowly. As the latter team evaluates potential impact on existing environments, new risks and increased security management requirements, their caution is warranted. For security teams taking on the cloud, Uncle Ben Parker’s famous advice to the young Peter Parker (aka Spiderman) rings true: With great power comes great responsibility.
With Great (Cloud) Power Comes Great Responsibility
AWS operates under a shared responsibility model in which the CSP is responsible for security of the cloud, while cloud customers are responsible for security within the cloud.
This means customer organizations’ cybersecurity teams are responsible for proper configurations within their own environments. Here’s a concrete example from the Identity Security world: CSPs must patch software on virtual machines (VMs) in a customer environment, but it’s up to the customer to configure Identity Security controls for access to those VMs, such as requiring multifactor authentication or implementing least privilege.
As such, security practitioners have the uniquely challenging job of embracing the cloud to enable the business, while preserving people, process and technology best practices learned on-premises.
Finding the right balance between control and access in cloud environments is crucial, said Selipsky in his keynote. Establishing the right security governance encourages innovation.
Don’t Reinvent the Wheel. Keep Identity Security Simple to Eliminate Cloud Migration Friction
Fortunately, CSPs are investing heavily to increase the flexibility of their services. This makes it possible for customer organizations to use their existing security tools and workflows in their cloud environments. In practical terms, this means security teams don’t have to learn another system, toggle between another interface or hire specialized experts to bridge skills gaps. Interoperability also enhances risk reduction efforts by helping security teams stay ahead of attackers, maintain centralized security control and meet end-users’ requirements for speed and ease of use.

This week at AWS re:Invent, the world’s largest CSP continued to unveil ground-breaking cloud services and innovations. Several new security offerings center on this interoperability concept, enabling organizations operating hybrid environments to integrate and extend their existing Identity Security controls to new AWS services, among other proven cybersecurity practices.
CyberArk was a launch partner for two of these new security services:
- Amazon Security Lake: CyberArk Audit, an Identity Security Platform Shared Service, now delivers security event information to Amazon Security Lake. Organizations interested in leveraging a security data lake through AWS can now pull in security event findings from CyberArk’s audit service, which collects session recordings and audit information for a variety of identities accessing sensitive systems across hybrid cloud environments. This integration allows organizations to holistically review their security and audit data, enabling operational efficiencies and improving analysis of security events.
- AWS Verified Access: CyberArk Identity can now provide identity-related signals for AWS Verified Access — a new AWS service that delivers secure access to private applications hosted on AWS without a VPN. Organizations can now manage all user information, credentials, authentication and role access for AWS in CyberArk Identity as a single source of truth. This enables them to realize all benefits of AWS Verified Access without needing to change their Identity Provider (IdP) or make additional investments in the identity management infrastructure.
We believe security teams work hard enough. They shouldn’t have to reinvent the wheel to reap cloud benefits or defend their hybrid environments from attacks. These launches reflect a broader trend and much-welcomed emphasis on interoperability in cloud security. And our CyberArk team is proud to play a part in this effort.
Interested in extending your organization’s existing Identity Security controls and practices to your AWS environment? CyberArk offers more than 20 certified integrations (and counting) with AWS services. Explore them all on the CyberArk Marketplace.






















