
The director of Identity and Access Management (IAM) is fundamentally responsible for ensuring controls are in place to protect access to sensitive assets within the organization. This includes all aspects of identity, access and authentication for the entire workforce and also applies to Privileged Access Management (PAM) – which is what we’ll be focusing on in this blog. Specific accountabilities within this role typically include setting strategy, defining a PAM-based risk framework, designing and implementing appropriate access controls and providing monitoring, reporting and mitigation strategies around overall risk.
Executive reporting is essential in providing transparency around the state of risk within the organization and to demonstrate progress with PAM-based programs as they serve to continually reduce that level of risk. This type of reporting can be delivered in the form of key performance indicators (KPI), which are updates tracked and compared to a specific framework of goals, and Key Risk Indicators (KRI), which serve as a mechanism for monitoring risk reduction.
Scorecards and dashboard tools are often leveraged to help visualize metrics that used to capture the effectiveness of risk mitigation programs. These metrics are key to providing comprehensive reporting back to executives, lines of business and various oversight functions (i.e. risk management, audit and regulators). However, determining the appropriate level of reporting for each audience is often difficult. One important piece that requires careful consideration is to convey a specific message amongst all the data. And, for that message to hit home, it has to be tailored to the needs of the recipient.
These five fundamental steps can help establish your program, define your risk tolerance and report on your outcomes.
Define a PAM Risk Mitigation Strategy
Defining a comprehensive PAM strategy is a critical step to establishing the key risks you need to mitigate for your organization and how to prioritize your program’s activities. It is informed by the enterprise cyber security framework, emerging threats, industry trends and oversight requirements. A sound PAM strategy allows you to develop a risk mitigation plan, a roadmap for privileged access and a target operating model (TOM) that helps ensure the long term sustainability of your controls.
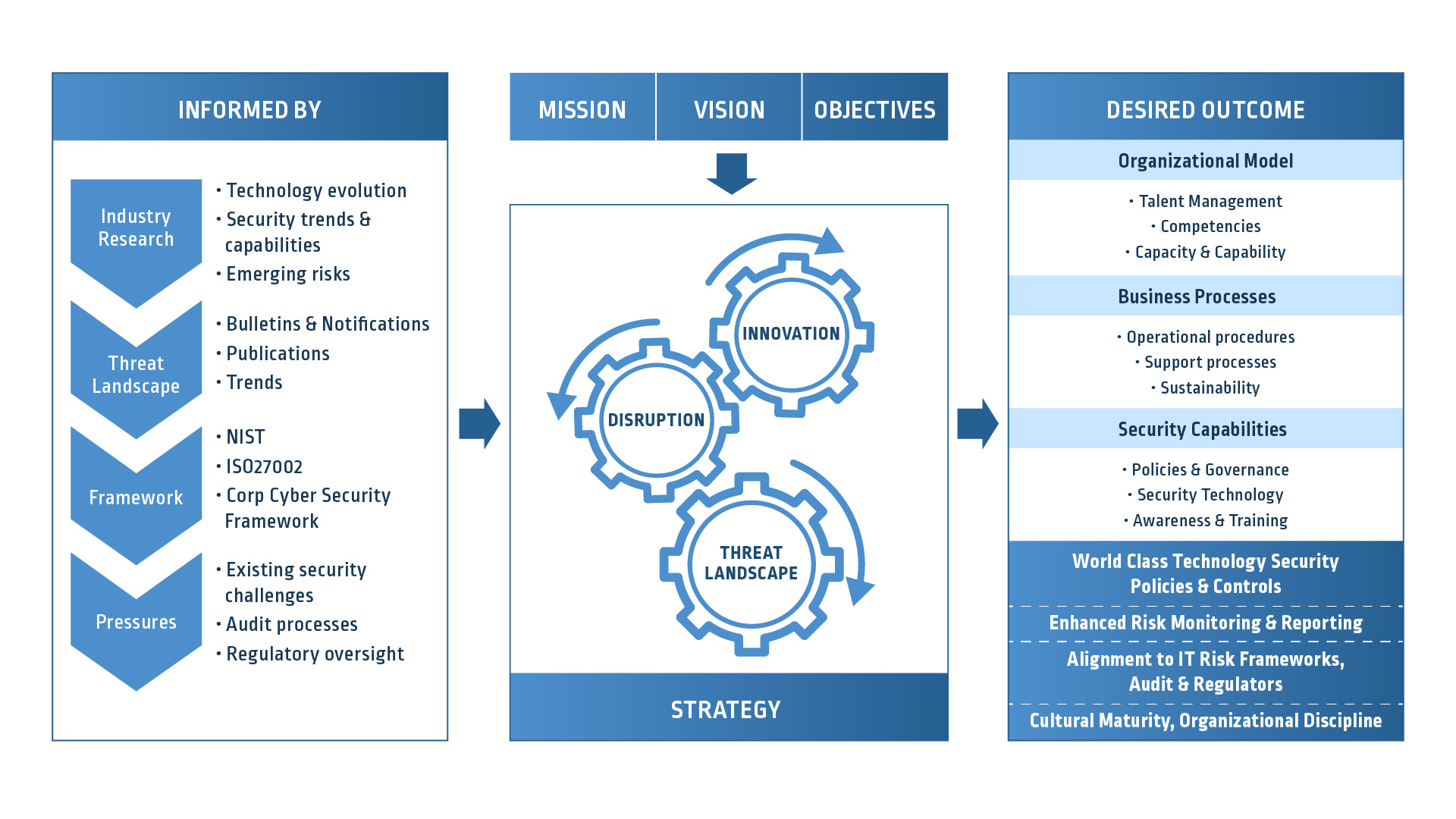
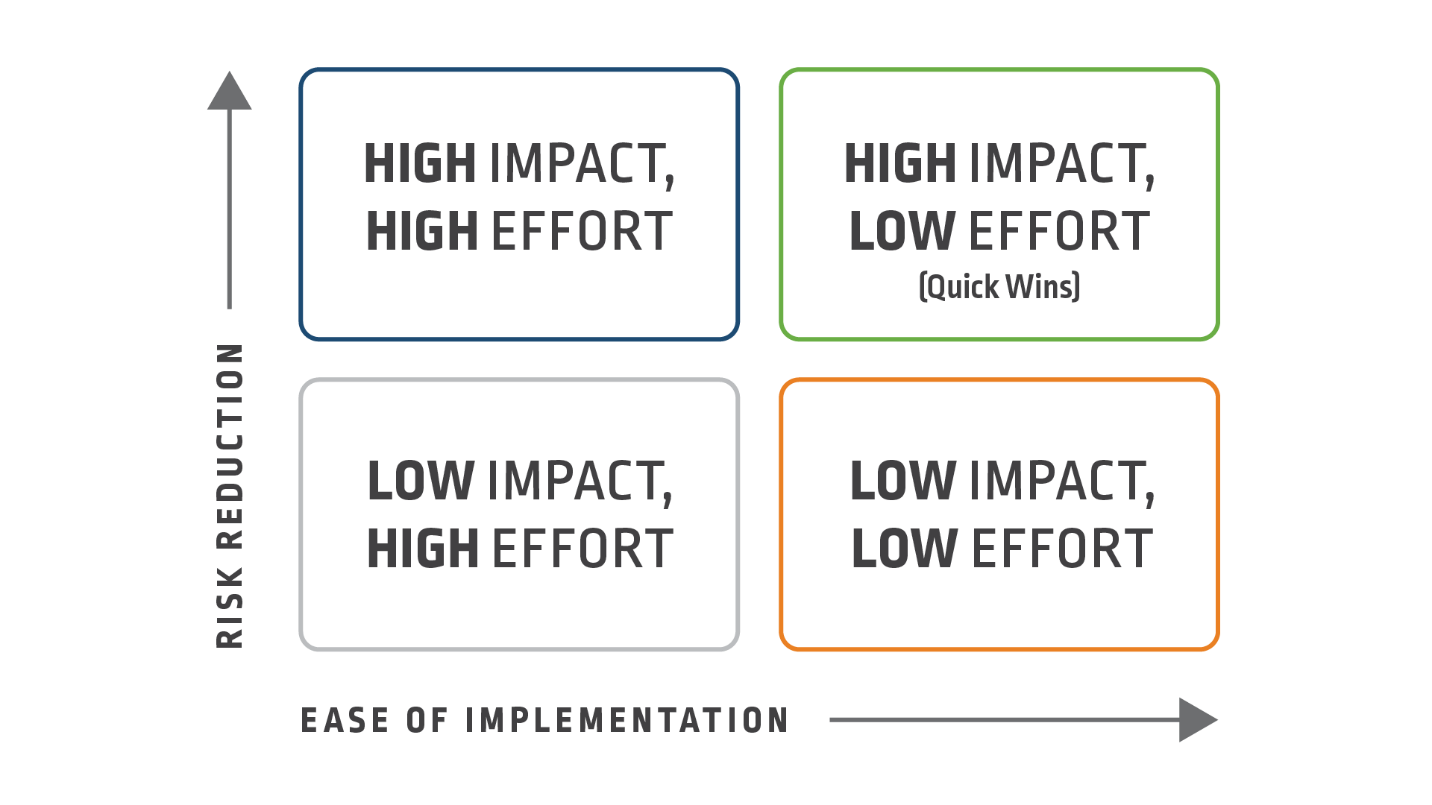
Designing your PAM model will not only provide you with a long-term view of your risk mitigation strategy, but it will also allow you to consider short-term quick wins, such as delivering PAM controls that provide rapid risk mitigation with the least amount of effort – both technically and politically.
IAM leaders should explore the CyberArk Blueprint, a PAM framework that provides prescriptive guidance and best practice recommendations for PAM development. It’s comprised of three guiding principles that make it easy to articulate the value of the PAM work that’s being executed on and why it’s important. This framework provides actionable risk reduction, which can be turned into a customized plan and roadmap that is then captured and included as part of your metrics reporting.
If you don’t have a PAM strategy and roadmap, your reporting does not provide any meaningful insight into the effectiveness of your risk mitigation activities. Although your reporting will continue to demonstrate some degree of progress, it will not be aligned to an overall series of goals and objectives; therefore, it won’t reflect a true risk posture.
Establish a Baseline of Privileged Controls
You can’t protect what you don’t know exists. To protect privilege within your enterprise, it is essential to understand the current state of privilege within your enterprise. This includes the inventory of assets within your operating environment and the array of privileged accounts that are used to support them. Privileged accounts and credentials can be found everywhere – extending across Active Directory, *NIX, IaaS, PaaS, SaaS, SQL and many other IT, OT and business services. It’s important to scan systems on your network and cloud providers on a regular cadence to uncover privileged accounts, credentials, entitlements and misconfigurations that can pose a risk to your organization.
The data generated from inventory will enable you to assess your level of risk based on your PAM framework and establish a set of targets and priorities for your implementation schedule. It will provide you with a set of numbers (i.e. 15 Window domain accounts, 2500 Windows server local admins, etc.) that will not only define your remediation strategy but will also establish a set of metrics that can be measured and reported against going forward.
One best practice to consider is integrating your PAM solution with vulnerability management and discovery technologies from vendors like Rapid7, Forescout and Tenable. This serves two purposes: providing security for the privileged credentials used to automatically sign-in to sensitive infrastructure environments and, at the same time, providing valuable insights into asset- and credential-based information that can help inform your migration strategy.
The only thing worse than having risk, is not knowing where you have risk or how extensive that risk is!
Evaluate the Strength of Existing Controls
Defining your PAM strategy and framework establishes your risk goals and tolerance. Meanwhile, your baseline of privileged controls delivers an inventory of both privileged accounts and technology assets. Understanding the state of the existing controls that protect privileged accounts and sensitive information within your assets is critical to defining the next steps of your action plans. Consider the following:
- Existing governance and policy language around privileged accounts and asset management
- Policies and procedures around provisioning, including gating, automation and signoffs
- A complete review of privileged accounts, roles and responsibilities and entitlements that ensure they are appropriate
- Security technology controls to protect, detect and monitor access
- Continuous assessment and testing on a regular basis to validate and remediate the strength of controls
Assessments of these types of controls will provide you with a knowledge of the key areas where you need to focus your program, whether that means quick wins or longer term strategic plans, and will also provide intelligent information to feed either your existing mapping framework or your governance, risk management and compliance (GRC) tools. This will enable you to visually illustrate where you have controls in place, where they need to be strengthened and how they map to other industry or regulatory compliance requirements
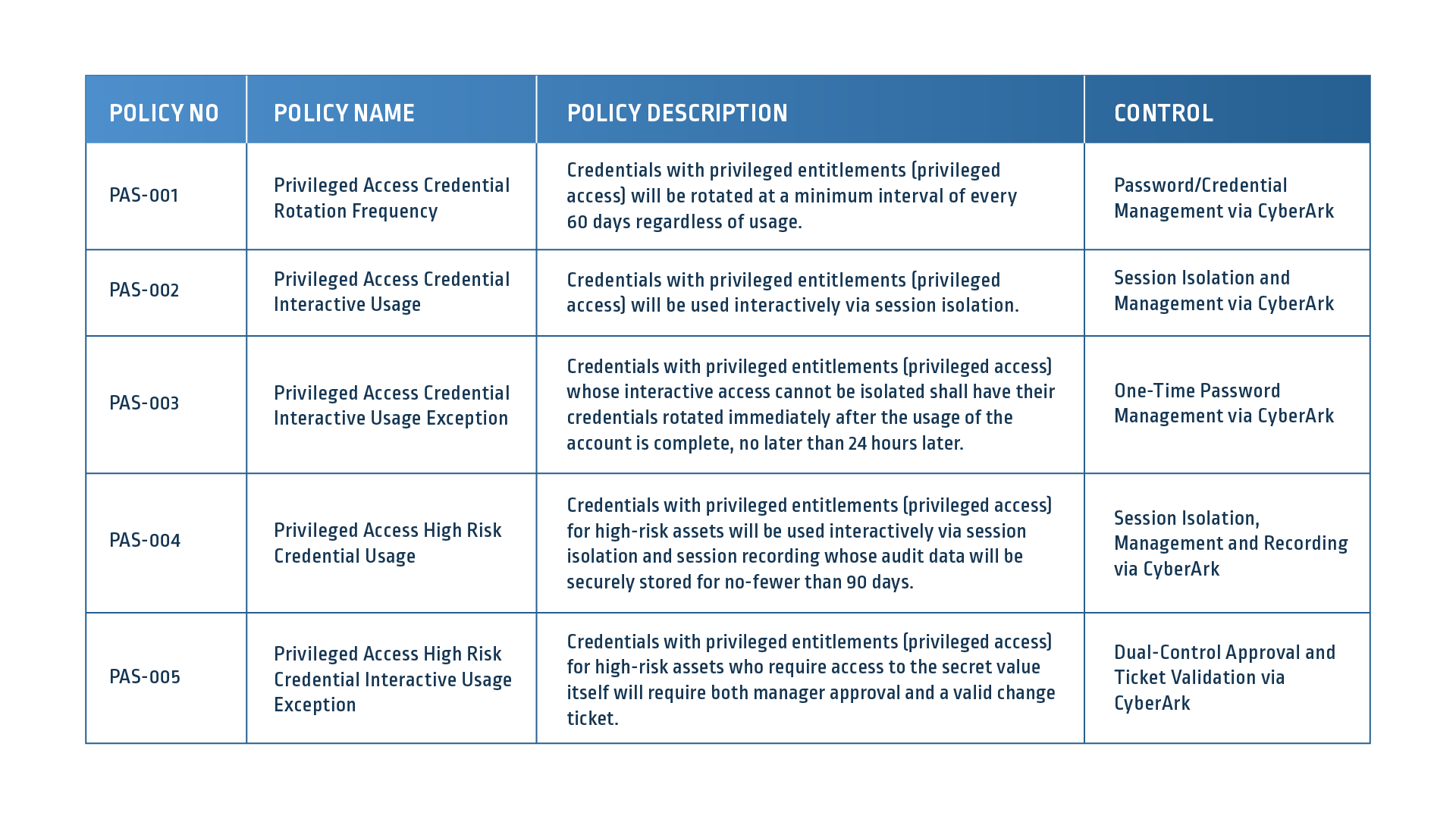
Understanding the state of your existing controls puts you in the risk driver seat. It allows you to demonstrate your remediation activities against your risk framework and alters the paradigm of having to rely on Audit to discover deficiencies. It transforms into a sound governance model.
Design an Effective Reporting Framework
Developing executive reporting can be challenging as you balance the amount of data you produce with setting the right tone with the right message in you reports. It is essential that your reporting not only depicts progress, but also measures your achievements against your strategy and risk reduction against your framework. Your framework should also consider the audience you are reporting to – whether it is an executive oversight committee, PAM steering committee, Senior Leadership team, audit committees or the board of directors.
Generally, the reporting audience is interested in seeing material progress with the program; on pace to achieve the objectives and driving risk reduction aggressively. It is really a report that qualifies the investment in both resources and finances the organization has made towards the initiative.
The score card below (Figure 4) is an illustration of the program “at a glance,” providing a view of the PAM implementation strategy designed for CISOs and highlighting key areas of both progress and exposure. It measures accomplishments against a series of defined timelines and calls out risk levels based on a pre-established set of measures, typically defined by a CISO. At a glance, you can tell if projects are progressing and whether or not the current state of onboarding is operating within the risk tolerance levels.
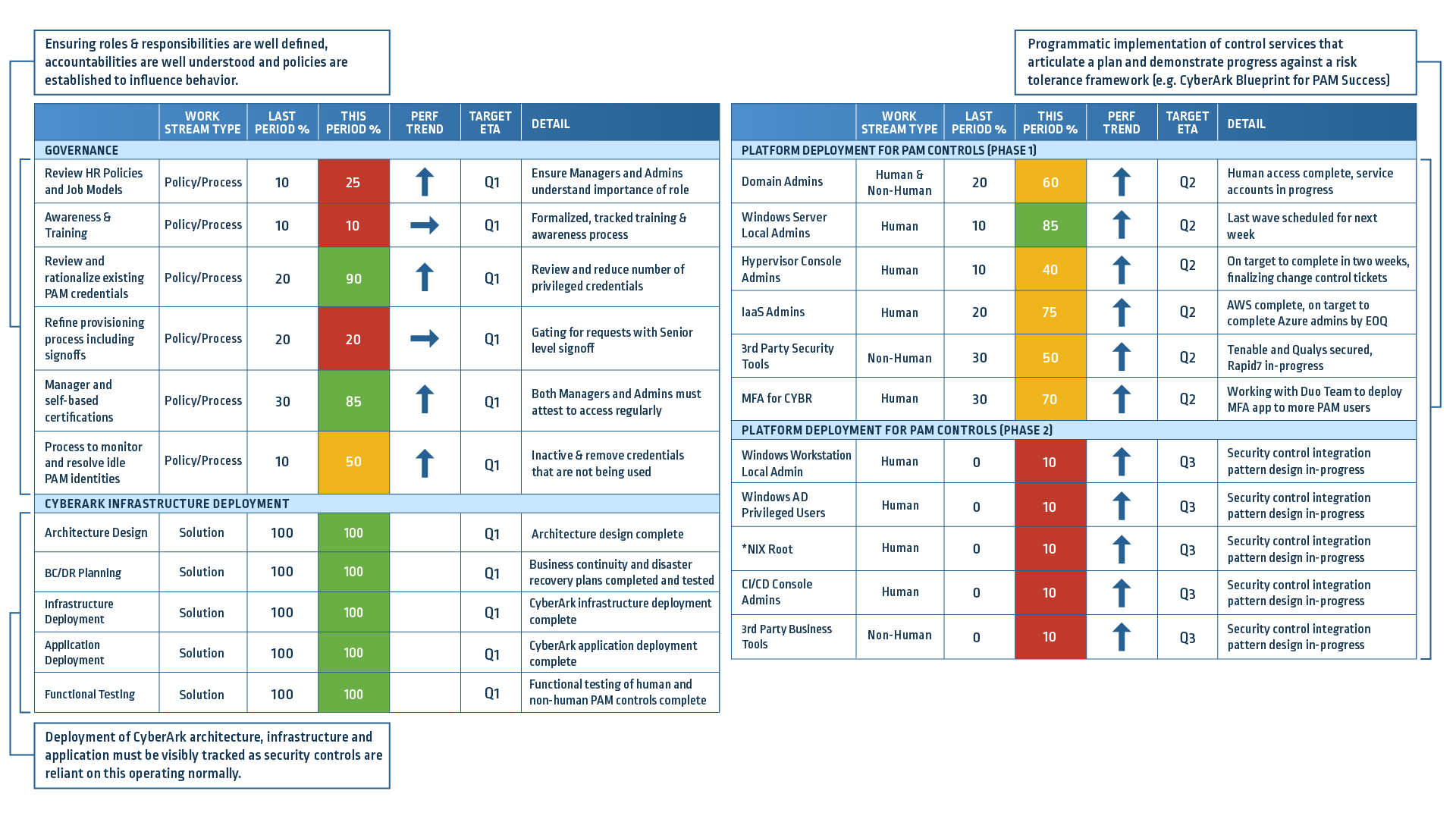
An effective reporting framework should provide measures that align to the progress of your program activities and your strategic framework. Amongst all the data, the complexities of your operating environment and the pervasive risks you are managing, it provides a simplified view into the state of health of your program.
Execute Your Reporting Strategy
Your reporting now becomes your narrative. It informs your leadership and oversight communities of the importance of the program, the progress achieved, issues that need to be managed and the level of risk mitigated as a result of the controls. The messages need to be succinct, concise and informative and will often need to be customized to the audience you are reporting to. Your reporting will be in the form of scorecards, dashboards, presentations and possibly open communications. The most important thing to remember is that your reporting sets the tone of your program. Understanding your audience, what they need to know and where they can help is fundamental to determining how you formalize your communications.
A wide variety of built-in reports – including inventory, entitlement and compliance reports – can be helpful in developing your scorecards and dashboards. Consider maximizing your time by leveraging automated processes to create your dashboards and scorecards. Exporting easily-ingested data into other business analytics and intelligence tools, such as Splunk Tableu and PowerBI, is another best practice. Consider enriching the data with inputs from other inventory tools, entitlement databases and compliance reports for additional contextual awareness. Your reporting should also be capable of feeding your GRC tools so that the organization has a real time view of the risk and control landscape. Use the tools that you have at your disposal and get the most from your existing technology investments.
When it comes to an effective reporting strategy, perception becomes your new reality. Make sure you understand the audience you are reporting to and that you provide meaningful, transparent and clear communications regarding your program that set the appropriate tone. If you don’t, your reporting committees will draw their own conclusions and they will define the narrative for you.
Secure Your Success as a Director of IAM
As the head of IAM, you are responsible for ensuring the appropriate controls are in place to protect and secure access to your firms most sensitive assets. Privileged access continues to be a prime target for nefarious characters and poses a significant threat if the controls are not operating effectively. This makes privileged access management a top business priority.
As a trusted advisor, CyberArk partners with IAM directors from around the world to secure and manage privileged access for organizations both large and small. Securing privileged access is instrumental in mitigating the risk of a cyber attack and maintaining business continuity. A successful PAM program is about more than just technology; it takes great people and well thought out processes to achieve optimal results.
CyberArk has the knowledge, resources and experience to make sure your PAM program is successful at every stage. Before you can report back the success of your PAM program, it’s critical that you get off on the right foot with a guided and prescriptive framework. Request a Blueprint session today or connect with your existing CyberArk account team to see how we can start securing your success today.























