
You know when you get stuck sitting next to that one relative who takes forever to tell a story or get to the punchline of a joke? Executive board meetings and quarterly updates sometimes go this way. With so many metrics to share, cybersecurity program leads can easily get bogged down in the technical details — leaving company stakeholders or steering committees glassy eyed, or worse, questioning the program’s efficacy altogether.
Cybersecurity leaders must come to the table with a powerful, yet succinct, reporting framework and dataset to build a compelling case and continuously justify their programs. But this requires a shift in perspective — because you can’t see the forest if you’re stuck in the trees.
Zooming Out on the Forest Starts with the Right Framework
Despite constant and evolving digital threats, cybersecurity programs are too often viewed as a black hole: money goes in but doesn’t come out, as they’re not traditional revenue-generating parts of the business. This makes it even more important for Identity and Access Management (IAM) and other security program leads to demonstrate their program’s value within the broader business context — either in quantitative terms of dollars and cents or through a compelling qualitative storytelling approach.
Fortunately, the solution is something cybersecurity professionals are already well-accustomed to using: a reporting framework.
Every company’s reporting framework will look a bit different — after all, your organization has a unique set of goals and requirements. But there are several common foundational elements that should be incorporated into any reporting architecture to help demonstrate program health and overall value.
The first? Defining what overall program success means to your organization. Do this by asking three important questions:
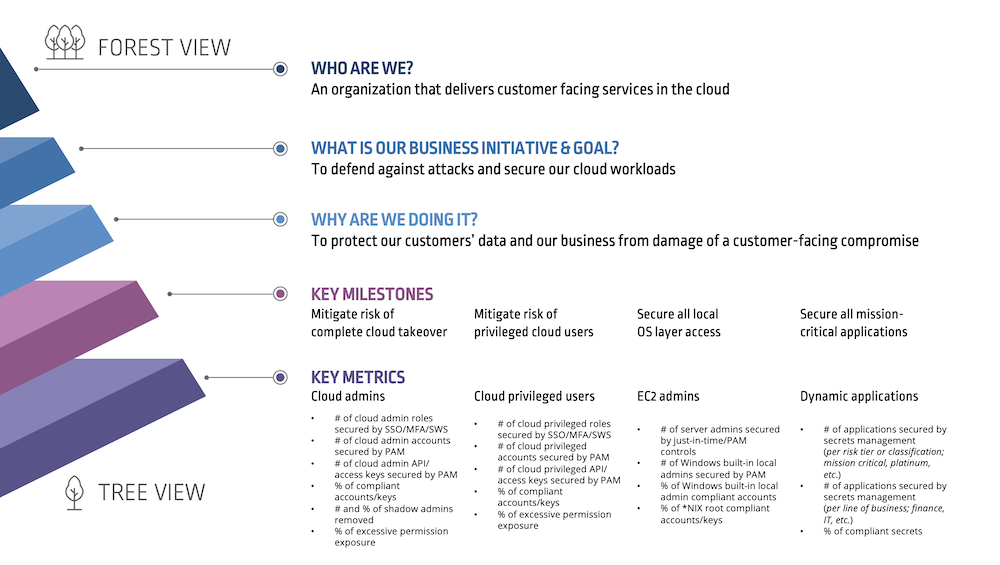
1. Who are we?
2. What are the business initiatives and goals that motivate us?
3. Why do we pursue those goals?
Your answers to these questions reveal what your business prioritizes and why. The next step is to dive deeper, defining the milestones and metrics that matter most:
4. Define the milestones or smaller objectives and outcomes related to the workstream, system or process encompassed by the program’s roadmap.
5. Map each milestone directly to the workstream, system or process you’re planning to secure. For instance, if a key program objective is to mitigate the risk of a complete cloud takeover, then you would want to measure things such as number of admin and privileged roles secured by single sign-on (SSO), multi-factor authentication (MFA) and session protection controls, along with the number of accounts and access keys secured by Privileged Access Management (PAM) controls.
Here’s a look at what this approach could look like in action:
The Right Reports for the Right Stakeholders
We’re starting to shift our focus onto the forest now, but there’s still work to do. Every company has stakeholders at various levels within the organization who will need to be briefed. Their role determines the nature of the metrics in your report: those closest to the security team will be interested in the nitty gritty — the individual trees. But the higher up the ladder you go, the broader you must zoom. For example, this cybersecurity veteran uses a one-page “placemat” when reporting to executives. In his words, “If we can’t tell some of the most senior executives within the organization how we’re doing and what the situation is or where they need to help on one page, we don’t deserve to be in this role.”
At most companies, IAM leaders typically report security metrics to four key audiences at regular intervals. Here are some guidelines on how to customize your reports for each level:
Director or vice president of identity (or similar role): With this stakeholder, you’ll typically focus on the individual “trees” — the data for specific metrics and milestones — on a regular basis. Reporting typically occurs monthly, or at least quarterly, and will play a critical role later when it’s time to make board-level reports.
Steering committee: With this group made up of IT and security leaders, project managers and other stakeholders, you’ll cover the same metrics and milestones but will also move up a level to discuss goals and report on blockers or issues related to your security initiatives. These meetings typically happen once or twice each quarter.
Strategic business review by IAM stakeholders: Now you’ll be briefing IAM leaders, lead engineers and key stakeholders, as well as security vendors and partners. In addition to giving reports to the steering committee, you’ll describe how to push forward to help reach the company’s desired business goals and outcomes. These briefings are typically held quarterly or semi-annually.
C-level executives and the Board: This is when the whole forest comes into full focus, and the reports for your director or vice present become part of a presentation given by the CISO or CIO. The board will want to know the overall state of security affairs and how the work you’ve done to achieve your goals impacts the business — as well as what the return on their security investment has been. Board meetings are usually annual or semi-annual affairs.
Notice how in this progression you’ll move gradually from discussing trees in the beginning to presenting the forest in the end. The reporting framework you develop returns its dividends in the form of informed stakeholders and supportive leadership.
Now You’re Flying Above the Treetops
Gaining perspective on the entire forest means realizing it’s more than just the trees. That knowledge enables more transparent, effective reporting and communication across all lines and levels of business.
So where can you go from here?
- Don’t let the scope of this undertaking daunt you. Yes, the forest is big, but a conscious shift in perspective goes a long way in refocusing efforts.
- If you aren’t already doing so, start developing your own reporting processes, set review cadences and drive your programs forward with the data you collect from these.
- Dig into the CyberArk Blueprint for Identity Security Success to help guide your roadmap and set major goals and milestones.
- Check out the eBook Securing Success: Reporting PAM Wins, which discusses how to define a PAM risk mitigation strategy, designing effective frameworks, and executing your reporting strategy.























