
Let’s face it—passwords are a pain, especially for employees and contractors who deal with them daily. We all know that our so-called “secure” passwords often end up being something like “Password123,” “qwerty” or another easily forgotten combination—and those same passwords are frequently used between personal and corporate accounts. And even when we try to be smart about it, they are still the easiest way for hackers to get in.
According to the CyberArk 2024 Identity Security Threat Landscape Report, in the 12 months leading up to its publication, nine out of 10 organizations experienced a breach due to phishing or vishing attacks. These attacks often impersonated trusted contacts or organizations, deceiving employees into disclosing sensitive information or clicking on malicious links. According to Verizon’s 2024 Data Breach Investigations Report (DBIR), over the past decade, phishing and compromised credentials have been directly responsible for more than 70% of publicly announced security breaches, with credential theft often being the most prevalent method for attackers to gain initial access to systems.
Passwords are the ultimate prize for attackers. So, how do you stop one of the most exploited attack vectors? Change the paradigm—fewer passwords. No passwords, no prize. That’s where passwordless authentication changes the game by eliminating the easiest way in.
The passwordless buzz has swirled for the last three or four years, but adoption has been slower than anticipated. Was it a technology barrier? Was it a perceived risk from the known? Was it the fear of something we do not fully understand? All the above?
That’s about to change with the recent release of new technologies, standards and integrations.

The Journey from Passwords to Passwordless
The Password Era: Challenges and Risks
Back in the day, passwords were the standard. They were simple, and for a while, they got the job done to some extent. But, as companies grew and technology advanced, the shortcomings of passwords became apparent: There were too many of them. Employees often reused the same password across multiple systems or chose weak, easy-to-guess passwords.
The consequences of these habits have been severe, leading to high-profile breaches and account takeovers that have exposed sensitive company information. In the SolarWinds breach in 2020, attackers gained initial access through a compromised account, enabling them to infiltrate major companies and government agencies.
These incidents highlight how passwords, even when paired with basic security measures, often fail to protect against modern threats. This is why organizations are rapidly moving toward passwordless authentication methods to eliminate these vulnerabilities.
Initial Steps: From SSO to MFA
Single sign-on (SSO) was a game-changer for many organizations. It dramatically reduced the number of passwords employees had to remember by allowing them to access multiple applications with a single set of credentials. The arrival of SSO simplified the user experience and helped minimize the security risks of managing numerous weak or reused passwords.
Building on that foundation, multi-factor authentication (MFA) added an extra layer of security by requiring additional verification, such as a code, biometric scan or security token on top of the SSO login. Today, MFA has evolved further with context-aware capabilities, meaning it can consider factors like location, device and user behavior to adjust security measures dynamically. This ensures that each access attempt is scrutinized based on risk level, making authentication secure and seamless.
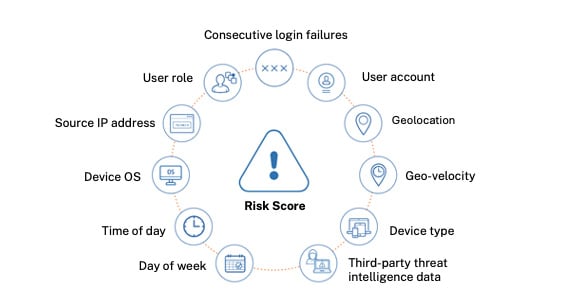
The Rise of Passwordless Authentication
Passwordless authentication removes the password entirely from the equation, where possible. Instead of remembering a string of characters, employees can use their fingerprint, a secure hardware key or even a passkey stored on their mobile device. These methods are more challenging for attackers to breach and speed up the login process, allowing your team to get straight to work without unnecessary delays.
Passkeys: The Future of Secure Login?
Passkeys are quickly becoming the game-changer that is making passwordless login a reality. Passkeys use strong public-key cryptography and stick to your device, making them more secure. They are built on FIDO2 standards, meaning they follow open protocols like WebAuthn and CTAP that ensure smooth compatibility across devices and platforms. Big names like Apple, Google and Microsoft are already rolling them out, so logging in can be as simple as a quick fingerprint scan or tap. Passkeys are not just a futuristic idea—they are driving passwordless awareness and adoption and changing how we think about security.
Addressing Feasibility Concerns: Is Passwordless Authentication Realistic?
Despite the clear benefits of passwordless authentication, its widespread adoption has been slower than expected for a variety of reasons:
- Legacy systems. One major challenge is the prevalence of legacy systems built around traditional password-based authentication protocols, such as HTTP headers and RADIUS, which weren’t designed for modern, passwordless methods. These outdated protocols lack support for more secure, token-based standards like SAML and OIDC, making integration with modern identity solutions complex, costly and, in some cases, impossible. As a result, certain systems will continue to rely on passwords for the foreseeable future, highlighting the need for solutions that bridge legacy and modern authentication approaches.
- Complex environments. Organizations operate in complex environments where diverse types of users access a wide range of apps and services, from web-based platforms and cloud applications to legacy systems on various devices. These environments are dynamic and constantly changing with new apps, users and devices added. This diversity often requires tailored solutions that can accommodate different user roles, devices and security requirements.
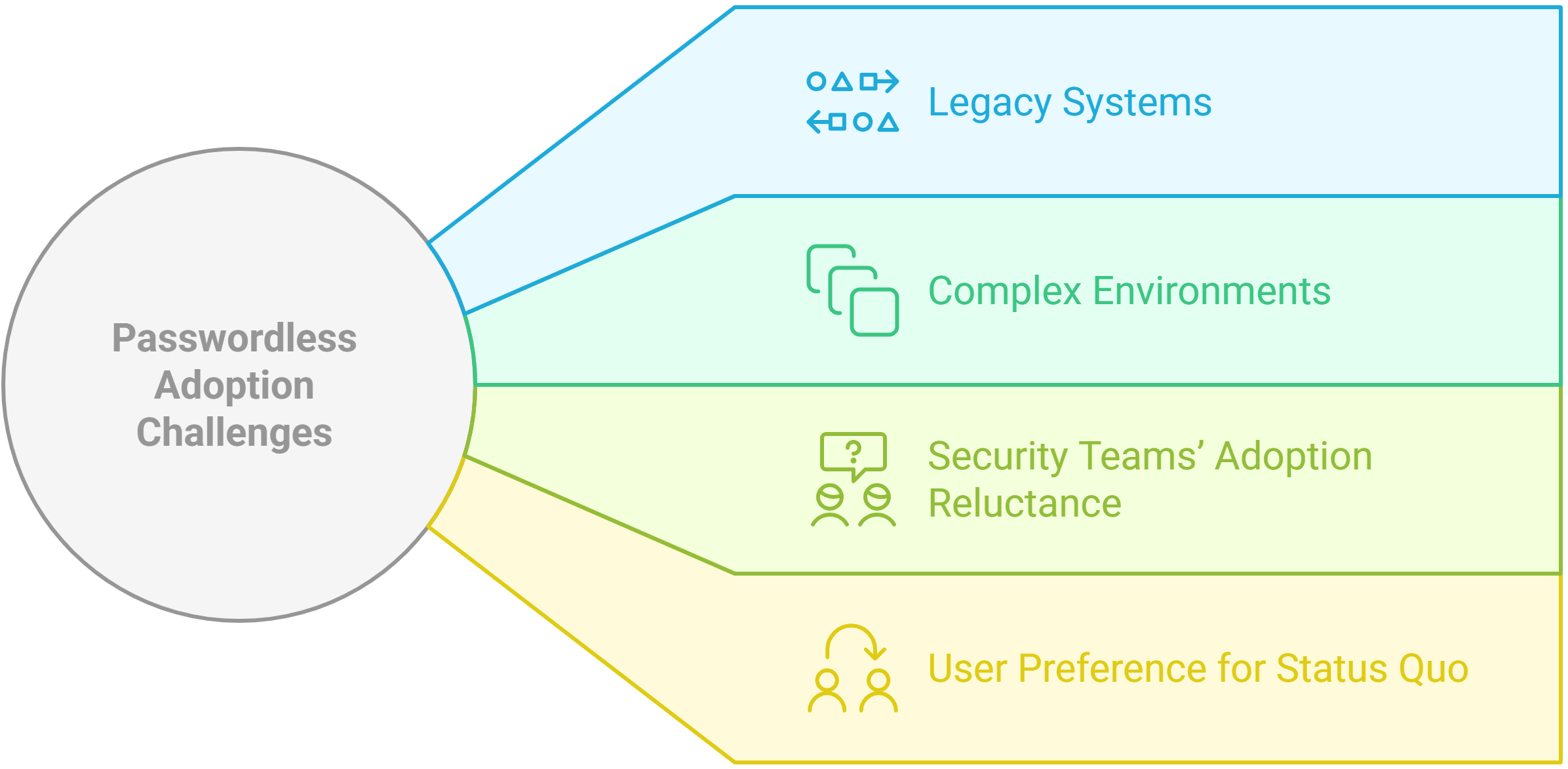
- Security teams’ adoption reluctance. Many organizations also remain cautious about transitioning to new technology due to security risks and the perceived immaturity of passwordless methods, leading to a “wait and see” approach.
- User preference for status quo. Many users are comfortable with the traditional password system they have used for years and may view the new methods as unfamiliar or intimidating. This hesitance can slow down adoption and require additional education.
The benefits of passwordless authentication are becoming more apparent, but that doesn’t make it a breeze to implement. However, more and more companies are pursuing the passwordless path because it balances security and user experiences, enhancing them both. Achieving a balance between security and user experience is not often the case with typical security projects.
Turning the Corner: Embracing Passwordless Solutions
Despite earlier challenges, passwordless authentication is rapidly gaining traction today. Companies now utilize identity and access management (IAM) tools and workforce password managers that integrate with existing systems, allowing them to deploy passwordless solutions incrementally.
Further developments of FIDO2 and enhanced security features such as biometrics, security keys, passkeys, and context-aware authentication offer better protection against modern cyberthreats. Still, they also streamline the user experience, reducing helpdesk costs and boosting productivity.
Employees are becoming more familiar with passwordless authentication options (we are all consumers, after all). Consumer-focused companies are focusing on balancing security and experience regarding access. This means that if logging in is annoying, then those customers aren’t coming back again. This improved user experience is now being demanded in the workplace as well.
Benefits of Passwordless Authentication
Passwordless authentication offers several key advantages that can significantly enhance security and user experience. Three major benefits are:
1. Better Security
Passwords are the equivalent of leaving your office door unlocked. Weak or stolen passwords cause 81% of breaches, according to the 2024 Verizon DBIR. Even if you have extra security measures in place, the fact that an easy-to-guess password is being used can undermine everything else. With passwordless methods, you are effectively closing that door. Advanced technologies like biometrics and hardware security keys use robust cryptography that makes it much more challenging for cybercriminals to break in, increasing the level of security.
2. A Smoother User Experience
Have you ever been locked out of your work account because you forgot your password? It is not only frustrating, but it wastes time and interrupts productivity. With passwordless authentication, your team can log in with just a tap or a glance. No more scrambling to remember complex passwords or dealing with cumbersome reset procedures, reducing the downtime that can hurt overall productivity.
3. Time and Cost Savings
Password-related issues are a real drain on IT resources. Whenever an employee forgets a password, it leads to a helpdesk call, which takes up valuable time and money. With help desk calls reduced after companies switch to passwordless solutions, IT teams can focus on more important tasks rather than constantly resetting passwords.
A Unified Approach to Workforce Authentication
A holistic passwordless solution ensures consistency across all touchpoints, making it easier to manage security policies and streamline IT operations. But, as mentioned earlier, it often cannot be accomplished all at once. A phased approach based on identified use cases and requirements is usually best, yet having a vision of where you are going is essential.
That means that as soon as you open your laptop or workstation, a passwordless experience should authenticate you. Then, as you launch your browser and web apps to SSO, passwordless authentication methods should greet you. Beyond the login, continuous authentication must be delivered by monitoring user actions and access. If a risk elevates, the identity provider (IdP) prompts an authentication request.
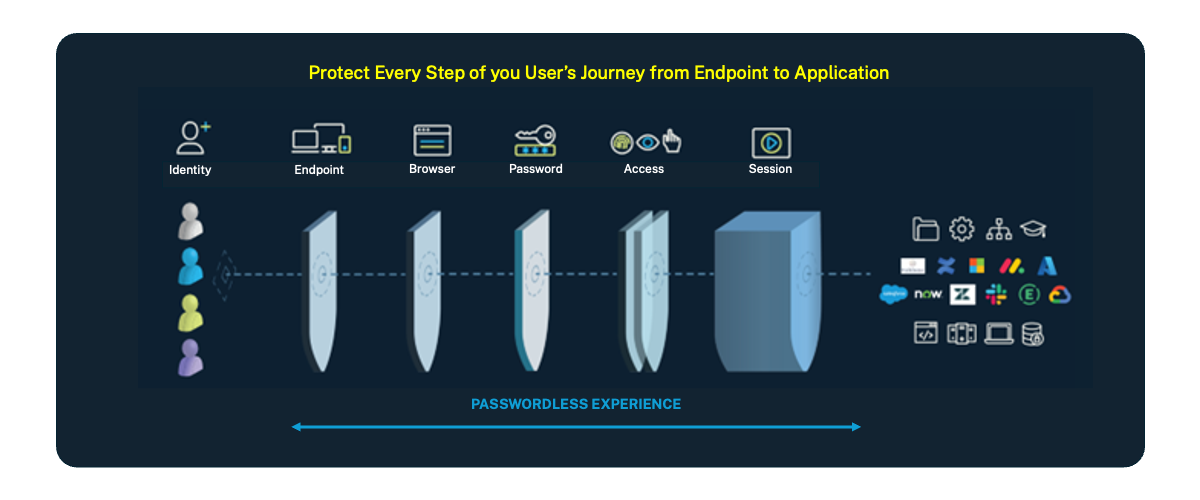
What about those pesky custom, on-prem and legacy apps that cannot live without passwords? A workforce password manager is ideal here, as it delivers a passwordless-like experience by managing passwords for those types of applications. This password management solution, in turn, delivers a passwordless-like experience for all of your applications across the enterprise, giving you full coverage.
Most organizations have various types of users, not just workforce users. It’s important to consider use cases for IT and development teams because they often have higher privileges, meaning they carry more risk to your organization while demanding even better user experiences.
Embracing Passwordless Authentication
Moving away from traditional passwords is not just about keeping up with trends but addressing substantial security and user experience challenges. Passwords are a significant vulnerability in today’s digital world, and by switching to passwordless authentication, organizations can enjoy significantly stronger security, a much smoother user experience and lower operational costs by reducing the reliance on the most hacked resource type, user credentials.
Check out our eBook, “Streamline Your Passwordless Journey,” to learn more about different authentication methods and for guidance on going passwordless.
Yev Koup is a senior product marketing manager at CyberArk.























