
As mobile workforces and cloud service usage continue to surge, organizations are struggling to provide secure, authorized access to their most sensitive information while keeping it out of the wrong hands.
This cybersecurity challenge is even more pronounced for the 300,000 companies supplying the U.S. Department of Defense (DoD) because theft of information could damage the U.S. economy, undermine technical advantages and even threaten national security. These organizations need to know exactly who is accessing and sharing confidential data, while balancing availability with security. And their ability to do this effectively is precisely what the Cybersecurity Maturity Model Certification, or CMMC, aims to measure.
Here’s a brief breakdown of what the CMMC is as of today and why it matters. It’s important to note that the DoD is currently making some changes to the program structure and requirements, so keep an eye out for additional updates. In this post, you’ll also explore how CyberArk can help organizations implement essential security controls for privileged and administrative identities to meet current CMMC requirements.
What is the CMMC?
CMMC is a model detailing cybersecurity best practices and processes from several security frameworks, including standards from the National Institute of Standards and Technology (NIST). It was established to protect two key types of unclassified information disseminating throughout the Defense Industrial Base (DIB) and the DoD supply chain:
- Federal Contract Information (FCI): “Information provided by or generated for the government under contract not intended for public release,” as defined by the DoD.
- Controlled Unclassified Information (CUI): “Information that requires safeguarding of dissemination controls pursuant to and consistent with laws, regulations and government-wide policies,” as defined by the DoD.
Why is the CMMC so important?
CMMC represents a major move from self-certification to formal certification by an approved assessor to analyze an organization and assign a maturity level based on the state of its cybersecurity program. Any organization wishing to participate in the DoD supply chain must adhere to CMMC requirements at some level.
What’s included in the CMMC?
The CMMC includes 17 domains broken down into five maturity levels and 171 cybersecurity best practices (75 technical and 96 non-technical controls), aligned with a set of capabilities. This breakdown formalizes cybersecurity activities within organizations, so they are both consistent and repeatable. The CMMC provides a certification that ensures organizations implement these required processes and practices. To meet certification requirements, organizations must meet a cumulative set of processes and practices. In other words, to advance to the next level of certification, an organization first must demonstrate proficiency in processes and practices at lower levels.
To whom does CMMC apply?
All DoD defense contractors, including prime and subcontractors, that handle CUI/FCI data are required to Commercial Off-the-Shelf (COTS) technology is out of scope unless a system manages, stores, transmits, collects, releases and/or supports CUI/FCI data in some capacity.
DIB contractors can seek CMMC certification for an entire enterprise or for only one or more segments of the enterprise, depending on where and how securely they store the information. To qualify for certification, organizations must provide proof of institutionalization of processes. They also must show that they have implemented the practices to support those processes.
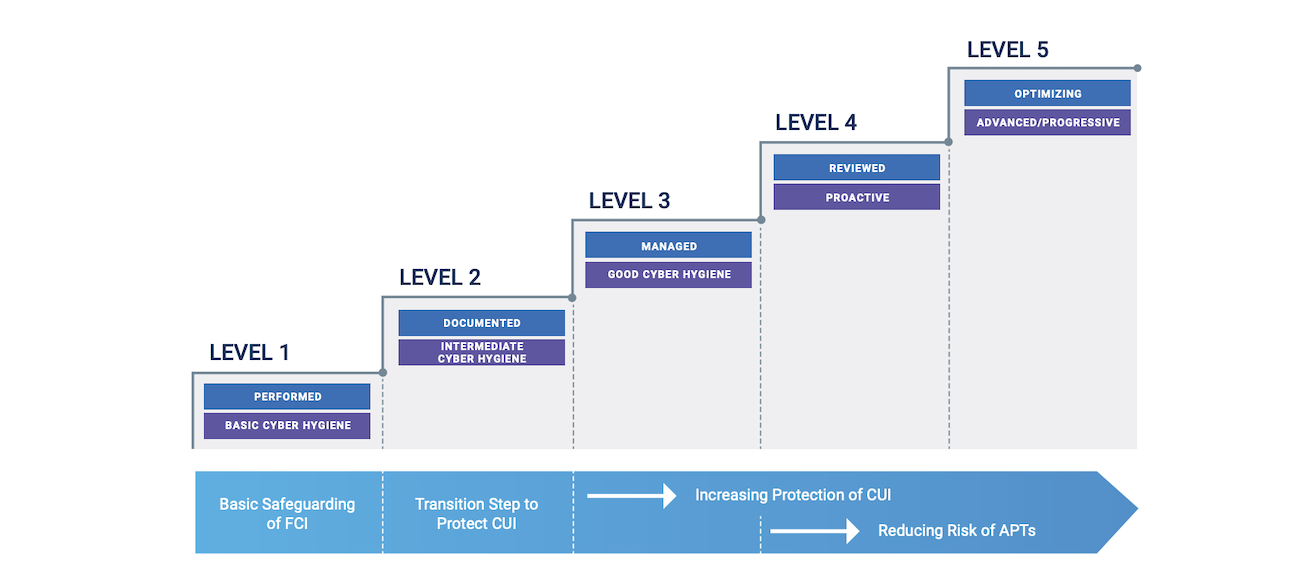
What are the five levels of the CMMC?
The CMMC domains are mapped across five levels of security controls, as shown below. To reach Level 1, organizations must follow a set of defined practices, including implementing 10 specific technical security controls covering basic cyber hygiene fundamentals. To reach Level 3 or above, organizations must prove the maturity of a process and provide documented evidence. To achieve the highest level of information protection (Level 5), organizations must implement a total of 75 technical controls across areas including risk management, access control and identification and authentication. They must also demonstrate how these practices are standardized across the organization.
How can CyberArk support organizations in achieving CMMC compliance?
The CyberArk Identity Security Platform helps federal government agencies meet today’s challenging security and compliance requirements. Our toolset — including DoD UC APL-certified CyberArk Privileged Access Manager — provides organizations a jumpstart to CMMC compliance through:
- Policy enforcement and audit trails based on defined roles
- Integrations with many other tools for a holistic access solution
- Professional services and training that can help to further mature the CMMC program
- A robust CyberArk partner network for integrations
- Integrations with what an organization has in place
- The ability to address risk management, domain administration, firewalls, vulnerability management, credentials and endpoint management
Which of the CMMC technical controls can CyberArk address?
In total, the CMMC has 75 technical controls (the 96 non-technical controls are a mix of administrative tasks, policies and procedures).
The CyberArk solution satisfies 41 of the technical controls needed for the CMMC levels. Through integrations with other security tools offered by our partner network, CyberArk can help organizations meet the remaining 34 technical controls.
On the journey toward CMMC compliance, CyberArk can help your organization effectively and efficiently meet process and practice requirements to protect information through comprehensive Identity Security controls. Visit here for a detailed analysis of the ways in which CyberArk can support compliance with CMMC requirements. You’ll find an at-a-glance view of individual requirements mapped to each CMMC level, the specific type of support provided and whether the solution is supplied directly through CyberArk solutions or with the involvement of third-party partnerships.




















