
Phishing attacks are pervasive, whether you work at a global telecommunications company or a small local retail shop. Fortunately, employees have come a long way in spotting phishing attempts, especially those of the email variety: Only 2.9% may click on phishing emails, according to the latest Verizon DBIR. Yet attacks on several large technology firms show how sophisticated some multi-pronged phishing schemes have become.
5 Common Factors Observed in Recent Major Phishing Attacks
Like a choose-your-own-adventure book, phishing can be approached from any number of angles, using an ever-expanding list of attack tactics, techniques and procedures (TTPs). What blocks a phishing attempt one day might not stop the next spoof – making layered defenses a must. Understanding where to focus, and when, can help cyber defenders gain an edge. To that end, we’re exploring five factors observed across these high-profile phishing attacks, along with cyber risk reduction tips from our CyberArk Labs and Red Team.
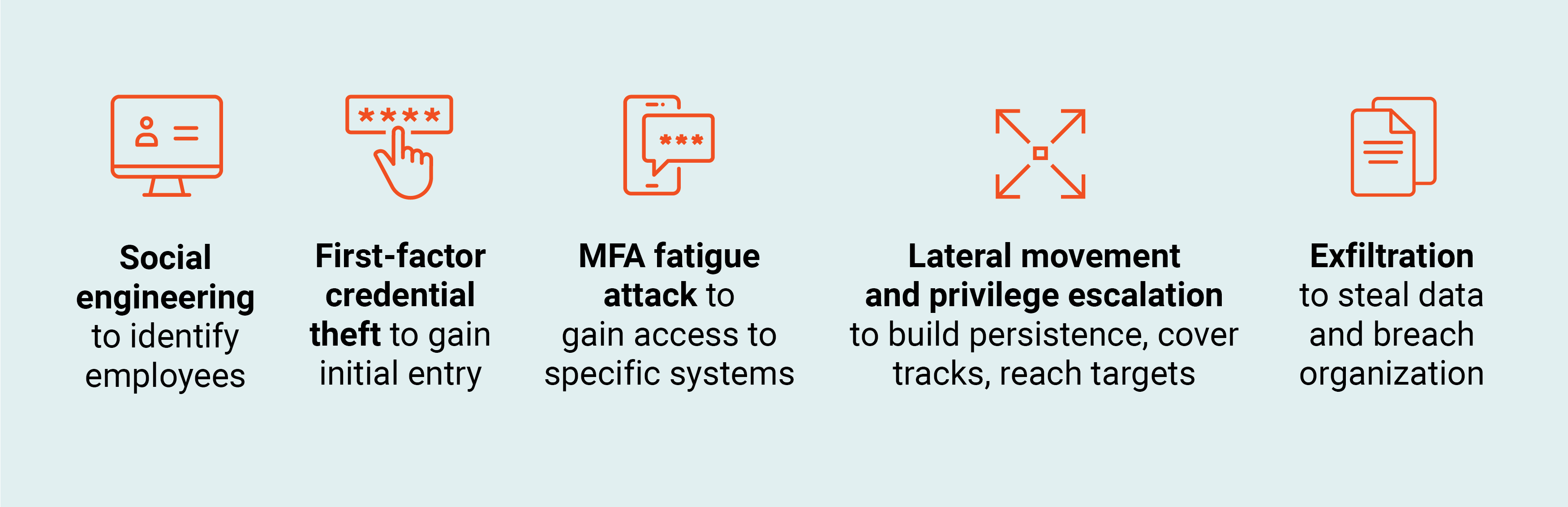
1. Social engineering to identify individuals working at specific technology organizations.
Cyber risk reduction tip: Recently surveyed security leaders ranked security awareness training as the second most effective defense-in-depth strategy for ransomware protection. Conduct routine training and education sessions to help embed security-conscious behavior into organizational culture – and keep employees informed of evolving social engineering and phishing attack techniques. Consider enhancing these trainings with ethical phishing exercises. And make sure your spam filters are working as they should to stanch the flow of suspicious emails, bulk campaigns and unsolicited marketing materials from reaching employee inboxes.
2. Identity compromise via first-factor credential theft to enter network. For instance, through man-in-the-middle (MitM) attacks that intercept passwords, or by targeting cached passwords stored in users’ browsers.
Cyber risk reduction tip: Awareness campaigns cannot always prevent a user from getting phished. Says Shay Nahari, VP Red Team Services at CyberArk, “In the grand scheme of defense strategies, endpoint privilege management that can protect client-side credentials – and help prevent the theft of cookies that could enable MFA bypassing – is an important layer.” When deploying endpoint security controls, consider prioritizing users who have a record of clicking on phishing attempts.
3. MFA fatigue attacks utilizing SMS and voice phishing to impersonate trusted sources, solicit the user to approve MFA notifications, “fatigue” the user with numerous MFA pushes, then gain access to the corporate VPN and other target systems once the user responds to the push.
Cyber risk reduction tip: Attackers continue to find new ways to target MFA and circumvent security controls. Selecting phishing-resistant MFA factors, such as a FIDO, QR codes or physical tokens, can help thwart these efforts.
“One method to mitigate MFA fatigue is switching your organization’s MFA setting or configuration to require a one-time password (OTP) versus a push notification,” says Nahari. “When faced with repeated authentication messages and touchpoints, users can often become careless and unwittingly create openings for attackers. While OTP requires more involvement from the user, it can mitigate the risk associated with MFA fatigue.”
He continues, “As part of my team’s adversary simulation exercises, we look at different types of detections, including hard indicators of compromise (IOCs). Hard IOCs are fundamental to a specific attack. In the case of MFA fatigue, the attacker already has access to credentials and needs to solicit the user to approve the MFA notification in order to gain access. If an organization is successful in blocking MFA fatigue, the attacker will be forced to choose another attack path. The OTP configuration can make the user less susceptible to this type of attack and significantly reduce risk.”
A more user-friendly approach is to require number matching for successful MFA authentication. With number matching, users responding to MFA push notifications using the authenticator app are presented with a number. They must type that number into the app to complete the approval. During a phishing attack, the end-user has no knowledge of the correct number sequence and therefore cannot approve the request.
When protecting against MFA attacks of all sorts, it’s important to mandate MFA anytime a personal profile is changed to keep malicious actions from going unnoticed, and set up proactive reviews of risky events. Additionally, your SOC can leverage user behavior analytics to set contextual triggers that notify if anomalous behaviors are detected, or block user authentication from suspicious IP addresses.
4. Lateral movement to establish persistence, cover up tracks and compromise additional systems and servers. Privilege escalation to reach critical systems, including domain controllers.
Cyber risk reduction tip: Enforce least privilege across all infrastructure, applications and data. It seems like a straightforward concept, yet it can be particularly challenging to do at scale. That’s where intelligent privilege controls come in, helping to seamlessly secure access for all identities and flexibly automate the identity lifecycle with continuous threat detection and prevention, along with behavioral analytics, to protect your most critical assets.
5. Data exfiltration.
Cyber risk reduction tip: In one of the latest phishing attacks, threat actors reportedly attempted to get back into the network after exfiltrating data and being detected and removed. To do so, they targeted employees who may have made single character changes to their passwords after a mandatory credential reset. Fortunately, the attackers were unsuccessful, but strong password practices are always worth reiterating. Better yet, take the burden off users completely by giving them a way to automatically generate unique and strong passwords.
Phishing has reached new levels of innovation, with recent events showing just how far attackers will go to dupe their unsuspecting – or MFA-weary – victims. Effective anti-phishing protection should involve both technical and human elements of security, assume that rogue clicks are inevitable, and focus on catching threats quickly before they become bigger phish to fry.





















