
Cryptocurrency seems to bring out the best effort from cyber criminals. From nation states to traditional attackers, the rise in crypto-related attacks is staggering. The motivation is obvious: it’s financially driven. Despite the recent drop, cryptocurrency values have skyrocketed over the past couple of years incentivizing attackers to create malicious code and sophisticated hacking tools to harvest cryptocurrency coins. One quick way to a massive payday is achieved by compromising a digital wallet and stealing the wallet’s private key. When attackers get their hands on a digital wallet, they can take full control of the funds.
Retailers have started to accept cryptocurrency right alongside good old fashioned cash and credit. This trend is commercializing decentralized currency and forcing the hand of many big banks to get on board. The leg up criminals have, in many of these attacks, is the anonymity involved in crypto-transactions. As this form of currency gains more credibility, organizations in every industry will need to implement security controls to mitigate risk against crypto-credentials from becoming exposed.
A Quick Review on Digital Wallets
There are two types of digital wallets: hot wallets and cold wallets. Hot wallets are used by individual users and organizations to store smaller amounts of currency, adding the need to be more fluid in nature for quick transfers and exchanges. There are many cryptocurrency services such as Coinbase and Bittrex that manage and store the wallet’s private key and provide users with easy access. In most cases, this type of managed service is password protected.
Conversely, cold wallets, used by organizations and security-savvy individuals, typically hold much larger amounts of digital currency. This type of wallet keeps its associated private key off the internet completely (for obvious reasons) and often stores it on an offline computer. Yet, as demonstrated by some of the recent attacks, if the network becomes compromised, then the keys will follow suit shortly thereafter.
There are solutions available that store private keys on a USB stick-like device that does not allow the extraction of the private key. The device is simply inserted into a computer to prove the user has access to the key (using cryptographic functionality zero trust algorithms). This solution provides sound security on the private keys, however, this is not suitable for larger organizations that need to control who has access to the device and its associated credentials.
Don’t Get Digitally Mugged
Cryptocurrency private keys are not exclusively used by human users. There are many automated processes that perform cryptocurrency transactions as well. Securing private keys for all users (both human and machine) is a foundational first step, quickly followed by authenticating and identifying who has access to the keys, controlling the access and monitoring its usage – and that’s where CyberArk can help.
CyberArk considers cryptocurrency private keys as another type of a privileged credential we can manage and protect. In essence, it’s stored similar to how we store a password with a few slight modifications and specific requirements such as ASCII text and character limitations (1024 characters). A ‘shared credential accountability’ and ‘least privilege’ model will allow organizations to not only understand who has access to keys and wallets, but also place limitations and restrictions around the access to these resources.
When human users access private keys, CyberArk ensures access control for permitted users only and establishes workflows such as dual control approvals. For automated processes, applications and scripts can access keys via APIs, but this is often not enough to be 100% secured. It’s critical to authenticate the application and assure it has not been forged or circumvented by a malicious insider or external attacker. With CyberArk’s application authentication techniques, we can validate to ensure only authorized applications have the ability to access and use the private keys. Furthermore, CyberArk provides auditability and monitoring of private key access both for detection of key misuse as well as forensics.
Here are six key (pun intended) considerations to help secure and protect cryptographic keys:
- Store cryptographic keys in a secure digital vault – Move keys into a digital vault with multiple layers of security wrapped around it, enforce multi-factor authentication to all users who have access to the vault.
- Introduce role segregation – Control individual access to stored keys, preventing even the most privileged administrators from getting to them unless explicit permissions have been granted.
- Enable secure application access – Enable access to stored keys for authorized applications and verify that the applications are legitimate.
- Audit and review access key activity – Audit all activity related to key access and implement trigger events to alert the necessary individuals of any key activity.
- Enforce workflow approvals – Enforce workflow approvals for anything considered to be highly sensitive and the same goes for accessing the keys.
- Monitor cryptocurrency administrator activities – Facilitate connections – similar to an automated secure proxy/jump host – to target systems that are used to perform cryptocurrency administrator activities (e.g. the system hosting the wallet).
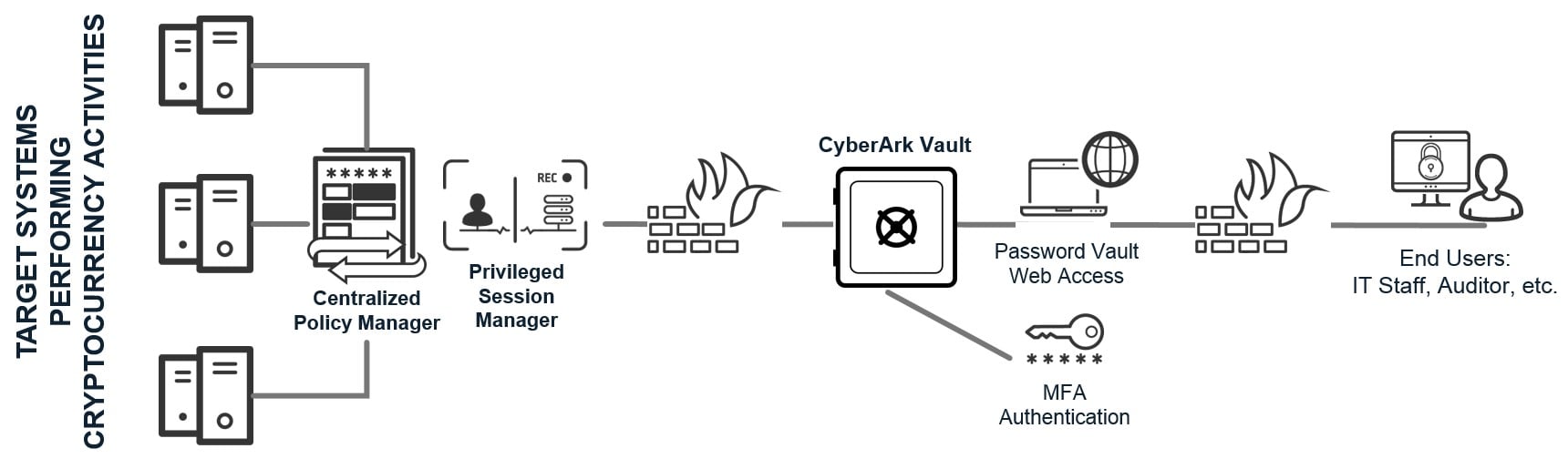
Figure 1: A standard architecture of CyberArk Privileged Account Security securing cryptocurrency activity.
Cybercriminals will continue to look at this technology as another opportunity to line their pockets. As the #1 leader in privileged account security, CyberArk will continue to safeguard critical systems from key harvesting and many other types of advanced attacks. Interested in learning more about protecting your organization’s cryptographic keys? Reach out to us today to see a live demo of how this works and stayed tuned for dedicated research to be published from the CyberArk Red Team on crypto mining in the coming weeks!

























