
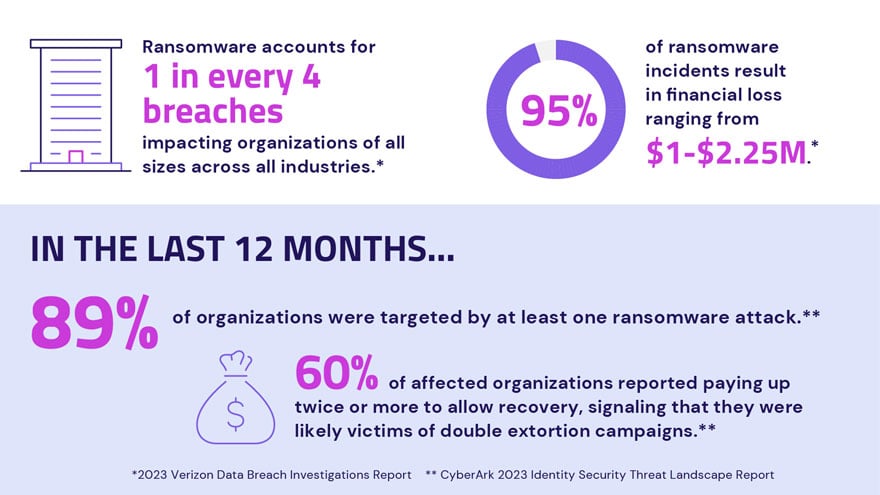
Ransomware accounts for one in every four breaches, and increasingly, it’s going after enterprise macOS users.
macOS Ransomware Attacks are Mounting
Historically, it didn’t make much financial sense for attackers to create Mac-specific malware since most company machines ran on Windows or Linux, but that’s changing. Macs now make up about a quarter of enterprise endpoints and malware as a service is readily available for every operating system. In the workforce, Mac users are often power users such as developers or executives who have admin rights and can access sensitive data and systems. This makes them highly attractive targets for criminal organizations seeking out the most impactful users – and necessitates robust endpoint privilege security controls.
Recent reports suggest that opportunistic attackers are paying closer attention to macOS – from new information stealers that grab passwords and extract data from web browsers and cryptocurrency wallets to the first-ever Mac ransomware samples linked to the notorious LockBit gang.
5 Reasons EDR/XDR Alone Can’t Block Mac Attacks
Since most cyberattacks originate at the endpoint, many security teams rely on endpoint detection and response (EDR) or extended detection and response (XDR) tools to protect against macOS ransomware and other cybersecurity threats. Unfortunately, adversaries count on this, which is why organizations still suffer costly and damaging endpoint attacks despite hefty endpoint security investments.
Here are five reasons why conventional endpoint security tools aren’t enough to stop macOS attacks:
- Many macOS attacks involve administrative privileges. Attackers routinely look for ways to exploit privileged accounts to deploy ransomware and achieve their goals. While EDR tools play an important defense-in-depth role, they aren’t designed with privileged attackers in mind.
- EDR solutions focus on known threats. EDR tools suss out threats by monitoring and analyzing various endpoint activities (i.e., processes, registry settings, file operations, network traffic) for red flags. They typically use signature-based detection methods to do this (looking at file signatures, threat-class signatures, string signatures and/or behavior signatures). But this type of detection doesn’t recognize unknown malware variants or zero-day exploits, and it takes time for EDR vendors to roll out updates addressing newly discovered attacks. This can create security gaps since attackers constantly change up their tactics.
- Attackers can bypass EDR/XDR tools. For instance, MITRE ATT&CK T1070 and T1562 and other
other adversarial techniques involving privileged accounts are often used to circumvent popular endpoint security products. And since most EDRs hook into Gatekeeper, Apple’s native software inspection technology, attackers have also devised a variety of methods to circumvent the tool’s security checks to execute ransomware and other malicious content. - Speaking of bypassing security checks, EDR solutions also can’t stop attackers from skirting or tampering with other endpoint security tools in place. A recently identified strain of macOS malware dubbed “Rustbucket” shows why this matters. Rustbucket sneakily circulates via a legitimate PDF viewer app. Since it’s an unknown strain, EDR tools are unlikely to flag it as malicious, and since it only tries to infect the target device after it runs the correct PDF file, antivirus probably won’t detect it either.
- Processing the massive volume of security events generated on endpoints – then creating (and continuously evolving) policies that follow security best practices – can be very challenging and time consuming, especially for large organizations with diverse environments.
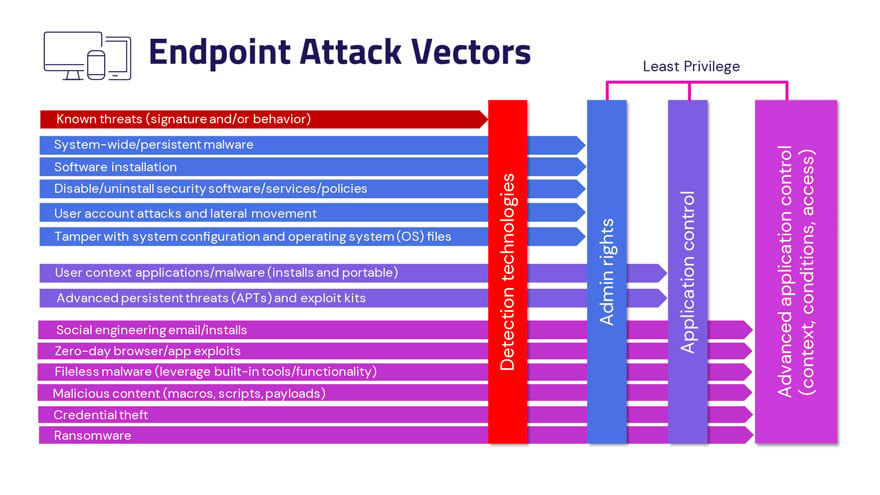
How Least Privilege Control Reduces the macOS Attack Surface
Reactively analyzing complex data sets for known attack patterns isn’t an effective (or sustainable) macOS protection strategy. Instead, the focus should be on establishing fundamental identity security controls to proactively defend against privileged attacks of all kinds – known and unknown. This comes down to least privilege.
Least Privilege to Eliminate Standing Local Admin Rights
No user should have local admin rights. But as any security professional knows, removing them all is a gargantuan task. It’s also a move that’s sure to frustrate Mac users and complicate IT operations. This is where AI-powered policy creation and consistent least privilege control are key for achieving balance – by automatically removing local admin rights, contextually authenticating identities and dynamically authorizing temporary, on-demand privilege elevation instead. Some applications require the user to be a local admin or have a local admin account. In these instances, admin rights can be granted just in time, then taken away as soon as the task is complete.
Least Privilege for Smarter Application Control
Mac users often need flexibility to download and use applications from the internet. But this creates risk. How do you protect the environment from an application that could be malicious or could attempt to download other apps that are undesirable? Here, conditional policy-based application control helps security teams create scenarios for every user group, from DevOps to HR, while defending against unknown malware variants without impairing legitimate applications. If a Mac power user needs to utilize an unfamiliar app, they can do in a secure, sandboxed environment while access to the internet and/or intranet, network file shares and other processes’ memory is blocked.
Least Privilege to Block Credential Theft
Credential theft remains security professionals’ No. 1 risk area and the root cause of most breaches. By stealing credentials and compromising identities, attackers can move deeper into an environment and closer to their goals. Defending credentials is a critical piece of the endpoint security puzzle. By instituting granular, policy-based least privilege controls, organizations can effectively safeguard credentials cached by macOS and other operating systems, password managers, web browsers, SSO solutions and other applications.
Least Privilege to Stop Ransomware at the Start
A strong mix of endpoint privilege security, privilege threat protection and application control can block ransomware actors before they can even get started. If an attacker does slip through the cracks, these controls will greatly complicate their mission by preventing additional credential compromise, privilege escalation, lateral movement and code execution, while hindering data encryption and exfiltration by ensuring that only approved content handlers can access files.
Trusted entities including the U.S. Cybersecurity and Infrastructure Security Agency (CISA) promote best practices including local admin rights removal, role-specific least privilege enforcement and credential theft protection across all enterprise endpoints – from workstations to servers, to physical and virtual infrastructures on premises and in the cloud. As ransomware and other threats continue to rise, foundational endpoint security controls are a must no matter what operating systems are in play.
To learn how CyberArk Endpoint Privilege Manager can help your organization improve macOS protection and proactively block ransomware and other cyber incidents, read our whitepaper “Tackle EDR Gaps Against Cyberattacks with Endpoint Privilege Security.”
Francis Yom is a regional least privilege specialist at CyberArk.























