The CA/Browser Forum’s recent unanimous vote to reduce maximum public TLS certificate validity to just 47 days by March 2029 marks a seismic shift in the digital security landscape. This new standard isn’t a proposal—it’s an approved policy. And every organization that issues or relies on public TLS certificates must begin preparations today.
Because it’s no longer about watching Apple’s early lead in reducing lifespans but following an industry-wide mandate. Security leaders should read this as the call to act now, as this sweeping change will facilitate efforts to increase crypto agility, reduce potential attack windows and drive automation on an unprecedented scale.
But what does this momentous decision mean for your organization, specifically? And more importantly, how can you prepare for what’s ahead? Today, we’re breaking down the implications, the CA/B Forum’s new phased timeline and why automation isn’t just helpful but essential.

Apple Breaks Ground and the World Follows: TLS Reform is Official
If you’ve followed the trend of decreasing SSL/TLS certificate lifespans in the last decade, you already know that Apple has pushed the envelope before.
In 2020, despite initial opposition, the company enforced a 398-day certificate validity period on its Safari browser, which ultimately set the new industry standard for shorter certificate lifespans.
Fast-forward to 2025, and Apple is again paving the way—this time toward a TLS lifespan of as short as 47 days.
Here is the confirmed phased rollout:
- March 15, 2026: Certificates capped at 200 days
- March 15, 2027: Reduced further to 100 days
- March 15, 2029: Certificates limited to 47 days, with Domain Control Validation (DCV) periods shortened to 10 days
This approach provides some time to prepare, but make no mistake, manual orchestration will be untenable, even from phase one.
Changes begin this year, and readiness must start immediately.
Why Shorter Lifespans Are a Cybersecurity Necessity
Shorter TLS certificate lifespans create certificate management challenges, but they’re critical for improving digital security. Shorter certificate lifespans drastically reduce exposure time for overlooked, expired or compromised certificates. Instead of letting a vulnerable TLS certificate linger for 398 days, shorter lifespans allow compromised credentials to, in essence, “self-destruct” more quickly, thereby minimizing risk windows.
As we move toward shorter TLS certificate lifespans, the urgency to adapt becomes even more critical. The rise of quantum computing presents a significant threat to the protection of today’s cryptographic systems behind machine identities. This adds additional urgency to driving shorter certificate lifetimes. Boards and auditors are now challenging CISOs on their readiness plans, emphasizing the need for automation to change certificate lifetimes more frequently. This approach makes it harder for adversaries to employ capture-now, decrypt-later tactics and will speed changes to new cryptographic algorithms when needed. The business case for this shift is clear and compelling for CFOs and CEOs alike.
Three Key Benefits of Shorter TLS Certificate Lifespans
Shorter TLS certificate lifespans offer several significant advantages that enhance security and operational efficiency. Here are three key benefits:
1. Minimizes Exploit Risk
Expired or long-lived certificates can become low-hanging fruit for attackers. And with 77% of security leaders believing that every undiscovered machine identity is a point of compromise, shorter certificate lifespans force more frequent validation, reducing blind spots and enhancing resilience.
2. Improves Compliance Readiness
Regular certificate rotation ensures adherence to standards like NIST, ISO 27001 or PCI DSS, reducing audit failures and regulatory fines.
3. Drives Automation Adoption
When lifespans shrink, automation helps ensure no certificate is forgotten, expired or mismanaged.
New Reality for Infosec Teams: Eightfold Increase in Renewals
If you thought the previous shift from 825-day to 398-day validity periods was resource-intensive, buckle up.
Moving to a 47-day lifespan means enterprises will face an eightfold increase in certificate renewal workloads. So, if you’re still relying on spreadsheets or manual workflows to track expirations, the message is clear: Automation is no longer optional.
And now, the clock is ticking.
The Growing Risk of Certificate-Related Chaos
Additionally, when it comes to securing certificates, the risks aren’t theoretical. And they’re only growing. Our 2025 State of Machine Identity Security Report found that, in the last year, 72% of organizations experienced at least one certificate-related outage, with 34% suffering multiple. And 50% reported security incidents or breaches related to compromised machine identities.
Industry research further highlights the financial impact: the average organization experiences three certificate-related outages per year, each lasting four hours and costing $9,000 per minute—although it varies based on company size and industry. As TLS certificate lifespans drop to 47 days, the potential for mismanaged or forgotten renewals rises dramatically, as does the risk of additional outages.
The marked increase in the volume, variety and velocity of machine identities—like API keys, certificates, and workloads—only intensifies the issue. And it’s not slowing down. In fact, 79% of security leaders expect to see an increase of up to 150% in machine identities in 2025.
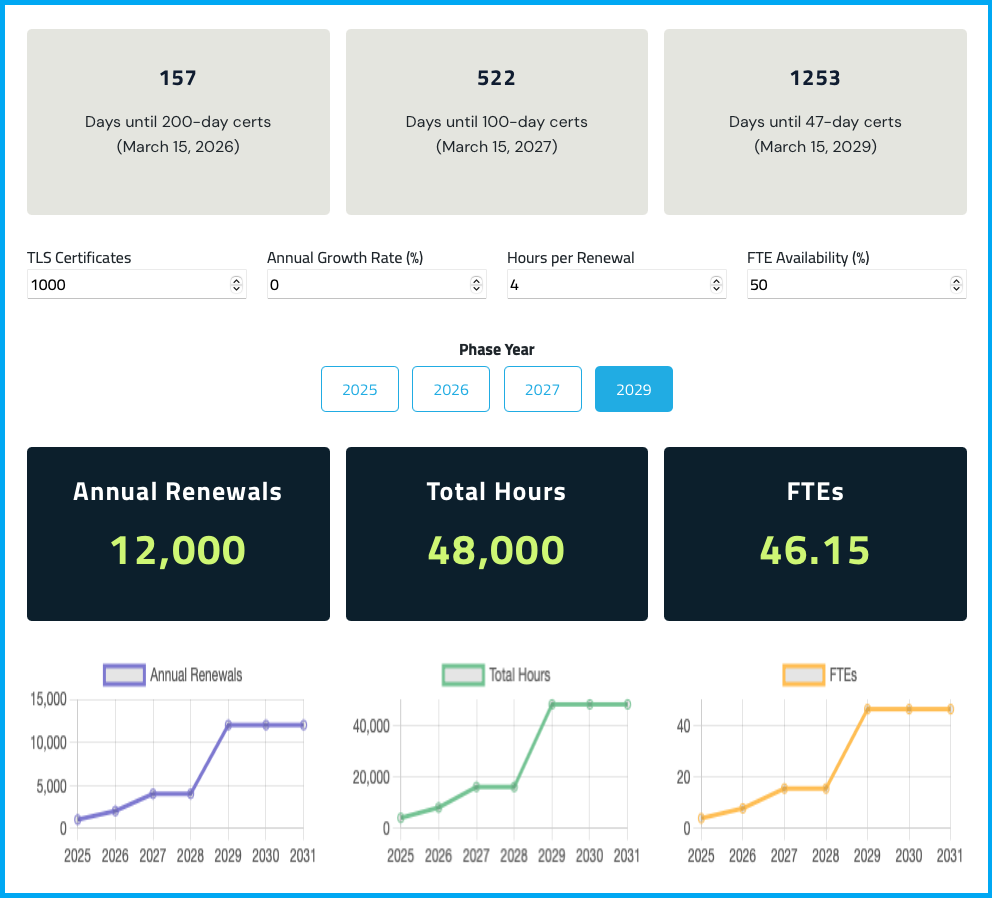
To look specifically at certificates, let’s examine the snapshot above, which illustrates the impact of shortening certificate lifecycles on operational workloads.
It takes about four hours to manage a single certificate manually. Let’s say you’re managing 1,000 (a very low number for today’s enterprises). With 398-day lifespans, that workload will take around 4,000 hours per year.
By 2029, however, the same set of 1,000 certificates will result in a twelvefold increase in renewal events—or 48,000 hours a year.
Without automation, scaling certificate management to meet shorter lifecycles is no longer feasible, making TLS certificate lifecycle management a strategic imperative.
Automated TLS Certificate Management Is the Only Way Forward
Imagine renewing thousands (or millions) of certificates manually, not once, but eight times a year. For most organizations, that’s simply unmanageable. The sheer amount of labor involved, combined with the expanded chances for human error, make this impractical, particularly as machine identities continue to grow at an alarming rate of 82:1 compared to humans.
Automated Certificate Lifecycle Management (CLM) delivers continuous certificate discovery and context, automatic lifecycle renewal, ongoing policy enforcement and enhanced crypto agility in the event of a certificate authority (CA) distrust event or other major cryptographic shift.
With automated CLM and a modern, cloud-based PKI-as-a-service, your organization gains scalable coverage for both internal and external machine identities. Plus, once your automation foundation is in place, you’re better prepared for a post-quantum world.
A Quick Note on the Quantum Conundrum
How are CLM and quantum computing connected? The eventual rise of viable quantum computers introduces new urgency around crypto agility and certificate flexibility. As adversaries begin to adopt “capture now, decrypt later” tactics, organizations must shorten certificate validity periods and be ready to rapidly shift cryptographic algorithms.
Essential Features of TLS Certificate Lifecycle Automation
To effectively manage TLS certificates and ensure robust security, it’s essential to utilize automation. The following are key features of TLS certificate lifecycle automation:
- Continuous discovery and context: Eliminate blind spots by tracking all certificates across your ecosystem, including hybrid and multi-cloud environments, and gain insight into behaviors, risks and priorities.
- Auto-rotation and renewal: Never worry about accidentally letting a certificate expire. The right solutions provide rapid issuance and seamless renewal workflows.
- Compliance enforcement: Automated tools help simplify updates so you can comply with the latest standards and stay audit-ready.
- Rapid response and crypto agility: Should a compromise occur, automated workflows ensure that affected certificates are revoked and replaced without delay.
- Independence from certificate authorities: Avoid lock-in and reduce business risk. In a world where CA trust can shift overnight, your CLM should be independent from the certificate authority itself.
Don’t Wait Until 2029 to Make Your CLM Future Ready
While March 2026 and 2029 are key milestones, the shift is already underway. For organizations still grappling with manual processes, every day without automation adds unnecessary risk.
However, by proactively upgrading your organization’s CLM processes today, you’ll safeguard operational continuity and gain a competitive edge in security and compliance.
The coming shift to 47-day TLS certificates may feel drastic, but it’s a change you don’t have to face alone. Ready to take your first step toward automating CLM? Run a free TLS certificate discovery scan to identify where certificates are deployed across your ecosystem and gain insights into expiring, weak or misconfigured certificates—before they cause outages.
Kurt Sand is the general manager of Machine Identity Security at CyberArk.