This research is published following the public release of a fix and CVE, in accordance with coordinated vulnerability disclosure best practices.
CVE‑2025‑60021, a critical command injection issue in Apache bRPC’s /pprof/heap profiler endpoint, was identified during broader analysis of diagnostic and debugging surfaces in the framework. The issue was discovered using Vulnhalla, CyberArk Labs’ AI tool that assists in triaging CodeQL results using an LLM. Prior to version 1.15.0, the heap profiler appended unvalidated extra_options input directly to a command string, enabling remote code execution when the endpoint was reachable. All versions earlier than 1.15.0 were confirmed to be affected.
What Apache bRPC provides and why profilers exist in production
Modern systems are often built from many small services, commonly called microservices. Instead of one large program, a system might include separate “users,” “payments,” and “recommendations” services that need to communicate with each other continuously.
RPC (Remote Procedure Call) frameworks make that communication feel like a local function call, even though it happens over the network. A high-performance RPC framework is optimized to handle large numbers of calls per second with low overhead, keeping services fast under load.
Apache bRPC is a C++ open-source library that helps developers build backend services that communicate over RPC, handling much of the networking and performance work automatically. It also includes built-in HTTP debugging and profiling endpoints, such as CPU and heap profiling, to help engineers troubleshoot production issues.
These endpoints are exposed as small HTTP URLs, for example /pprof/*, that return diagnostic data such as CPU samples, heap and memory snapshots, and other runtime statistics. This allows engineers to investigate issues without attaching a debugger.
Although these debugging endpoints are typically intended for internal or administrative networks, they still represent a sensitive attack surface. Misconfigurations can accidentally expose them to the public internet, and even when access is restricted to an organization’s internal network, vulnerabilities in privileged diagnostic endpoints can be abused by malicious insiders, compromised internal services, or attackers who gain an initial foothold inside the environment.
How extra_options led to command injection in /pprof/heap
The heap profiler service /pprof/heap did not validate the user-provided extra_options parameter before incorporating it into the jeprof command line. Prior to the fix, extra_options was appended directly to the command string as –<user_input>.
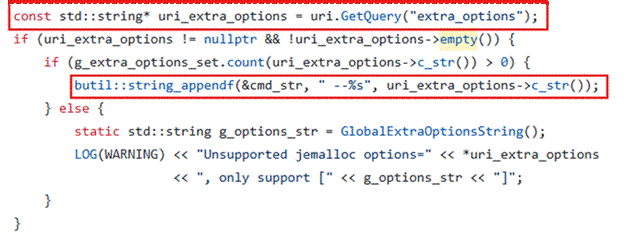
Figure 1: jemalloc code that parses extra_options from a user-provided URI and appends it to cmd_str. Source: Apache bRPC (Apache License 2.0). Code excerpt shown for security analysis and commentary.
Because this command is later executed to generate the profiling output, shell special characters in attacker-controlled input could alter the executed command, resulting in command injection.
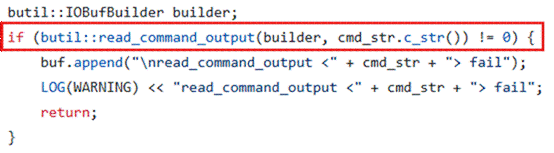
Figure 2: jemalloc code that executes the cmd_str. Source: Apache bRPC (Apache License 2.0). Code excerpt shown for security analysis and commentary.
When /pprof/heap is reachable, RCE follows
If the /pprof/heap endpoint is reachable, this issue allows an attacker to execute arbitrary commands with the privileges of the Apache bRPC process, resulting in remote code execution.
/pprof/heap?display=text&extra_options=;touch${IFS}/tmp/new_file
Snippet 1: Example showing how commands can be injected
Because bRPC services often run in privileged backend environments, successful exploitation can lead to full service compromise.
The vulnerability is rated CVSS 9.8 (critical).
Public exposure of /pprof endpoints and what scans show
Profiling endpoints such as /pprof/* are often intended for internal use but may be exposed due to misconfiguration.
At the time of writing, Shodan reported 181 publicly reachable /pprof/heap endpoints and 790 /pprof/* endpoints overall. While this does not indicate which systems run vulnerable Apache bRPC, it shows that profiling endpoints may be exposed.
Even when restricted to internal networks, this vulnerability can still be exploited by malicious insiders, compromised services, or attackers with an initial foothold.
Fix and mitigation
Apache addressed this issue in bRPC 1.15.0 by restricting the extra_options parameter to a small allowlist of supported jeprof options, preventing untrusted input from being incorporated into the executed command.
Users should upgrade to Apache bRPC 1.15.0 or apply PR #3101 if an immediate upgrade is not possible.
Additional hardening and defense‑in‑depth
- Treat /pprof/* as admin-only: restrict by network, bind to localhost, or require authentication at a reverse proxy.
- Disable heap profiling endpoints in production unless actively needed.
How Vulnhalla’s CodeQL‑at‑scale triage flagged the pattern
This issue was discovered using Vulnhalla, a tool developed by CyberArk Labs that runs CodeQL at scale and applies an LLM-based triage layer to help prioritize findings that are more likely to be exploitable.
In this case, Vulnhalla flagged the issue as vulnerable, triggering a manual review to confirm the finding.
Coordinated disclosure milestones and release cadence
- Aug. 5, 2025: Reported to the Apache bRPC maintainers
- Sept. 26, 2025: Fix merged (PR #3101)
- Oct. 27, 2025: Apache bRPC 1.15.0 released (includes the fix)
- Jan. 16, 2026: CVE-2025-60021 published
Simcha Kosman is a senior cyber researcher at CyberArk Labs.





















