
The Rapid Rise of Web-Based AI Agents
The introduction of OpenAI’s ‘Operator’ is a game changer for AI-driven automation. Currently designed for consumers, it’s only a matter of time before such web-based AI agents are widely adopted in the workplace. These agents aren’t just chatbots; they replicate human interaction with web applications, executing commands and automating actions that once required manual input.
While enterprise automation has already transformed workflows, these new AI agents promise even more significant advancements. However, they bring a host of security concerns and AI risk management that need immediate attention.
Automation has already taken over repetitive enterprise workflows across many teams and functions. Still, web-based AI agents promise to do more than streamline tasks—they could start performing actions that employees themselves cannot. This shift could redefine productivity while bringing myriad security concerns requiring immediate attention.

Personal Assistant or Security Risk? AI Agents in Consumer vs. Enterprise Settings
To understand the potential impact of web-based AI agents in the workplace, consider these two scenarios:
1. Consumer use case:
“Operator, book a weekend gateway: find flights, reserve a hotel, rent a car and make dinner reservations—all within my budget.”
2. Enterprise use case:
“Operator, analyze six months of IT access logs, cross-reference with HR records to identify job changes, flag orphaned accounts, detect privilege escalations and generate a security risk report for IT and compliance teams.”
While the consumer use case is a “simple” personal task with minimal security implications, the enterprise use case involves handling privileged data, automating security decisions and potentially bypassing traditional IT oversight. This raises critical questions about artificial intelligence cybersecurity: How do we control what AI agents can access? Who governs their actions? What happens if they are compromised?
Enterprise Automation: Unlocking Potential Beyond IT Efficiency
Enterprise automation has traditionally focused on streamlining repetitive tasks—doing what we already do better and faster. But as AI agents move beyond mere task automation, their potential—and risk—expand significantly.
These agents could hypothetically do things like:
- Log in to Salesforce, create an opportunity and generate reports autonomously.
- Automate customer engagement via email sequences in HubSpot.
- Manage file access and data extraction from images or text.
- Spin up cloud infrastructure on demand.
Unlike traditional automation, these AI agents don’t require API integrations or deep technical expertise. They operate just like human users, interacting with business applications, clicking buttons, entering credentials and performing real time actions. The potential for efficiency is vast, but so are the risks.
From Cloud to AI: Embracing the Next Wave of Transformation
Just as cloud computing reshaped the enterprise landscape, AI is following suit. The cloud introduced agility, speed and scalability but came with its own security challenges—misconfigurations, identity risks and an expanded attack surface. IT and security teams spent years catching up.
AI is on a similar path. Businesses are moving ahead, but security teams are still figuring out how to secure an agnetic AI-driven architecture, workflows and data. Alongside web-based AI agent risks, CyberArk research highlights several emerging threats:
- Infrastructure threats: AI agents rely on credentials, keys and tokens. A compromised session token could give an attacker control over the AI agent, allowing them to impersonate authenticated users.
- Session/access-level threats: AI agents can be tricked into executing unintended actions through prompt injection attacks—a new form of social engineering.
- AI identity threats: AI systems can be poisoned, leading to malicious behaviors like data exfiltration or the introduction of backdoors into enterprise systems.
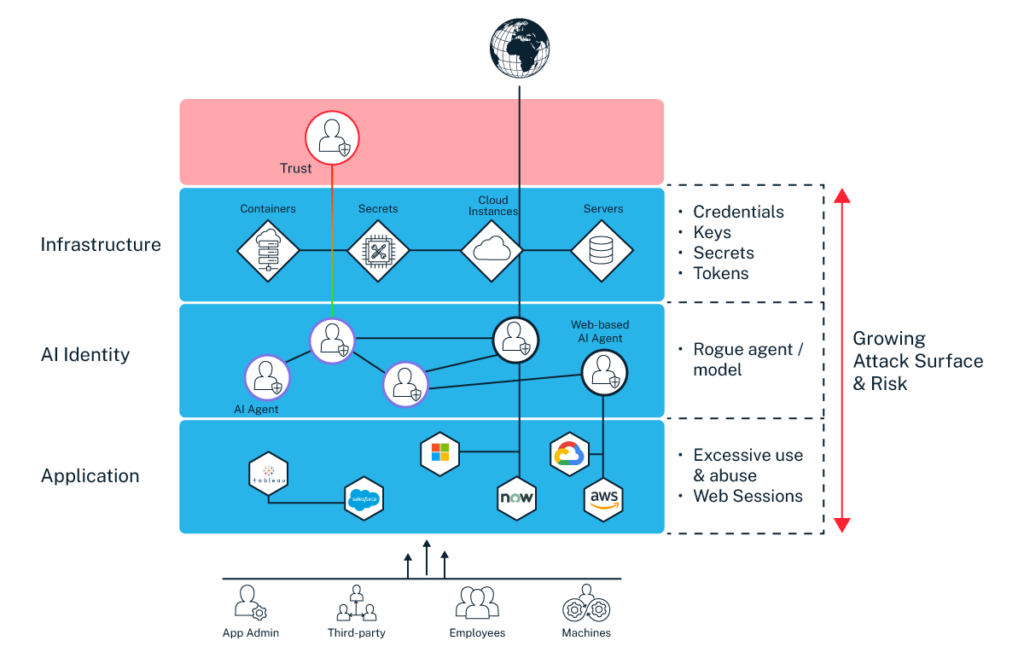
AI-driven transformation is here, but the question isn’t if AI will reshape workflows—it’s whether we can secure it before the risks spiral out of control.
Security Risks of Web-Based AI Agents: Who’s in Control?
As web-based AI agents become more autonomous, enterprises must reconsider their security strategy.
- Browser-based access: How do you control access if AI agents run in the cloud and interact with business applications via a browser? What happens if/when an AI agent uses your credentials to perform actions on your behalf? Who has the liability for actions? Are those actions monitored?
- Session control and auditing: IT teams can monitor their sessions and track activity when humans interact with applications. But how do we maintain the same level of oversight and control with AI agents?
- Authentication risks: AI agents can execute actions without further authentication once granted access. How do we prevent unauthorized actions in the name of automation?
- Identity security and AI vulnerability assessment: As AI agents proliferate, how do enterprises ensure that identity infrastructure remains resilient? Traditional identity controls focus on human users, but AI-driven automation requires adaptive security measures for machine identities. Can we assign and manage AI agents as distinct identities with enforceable least privilege policies? How do we prevent them from escalating access or being exploited as a new attack vector?
- Data lifecycle and exposure: How long do AI agents retain sensitive data? Who has access to their logs and execution history? What safeguards prevent misuse or unintended exposure?
We’ve spent years securing human accounts, enforcing least privilege access and monitoring suspicious activity. We must now extend these principles to AI-powered security.
AI(Sec)Ops: The Birth of a New Security Paradigm?
Are we ready to let AI handle our personal online chores? Perhaps. Are we prepared to let AI take over enterprise workflows? That’s a different question. Businesses will always push for greater efficiency and ROI, but security cannot be an afterthought.
AI-driven automation is inevitable. But as enterprises move toward AI-powered workflows, they need to adopt a security-first mindset. The future of work is changing, and AI agents will play a role. The real question is: how do we ensure they work for us—without becoming a threat?
To secure AI agents, we must adopt the best practices from DevSecOps that we’ve learned in the cloud era. Establishing AISecOps practices now—before the risks outpace our efforts—will ensure we manage risk proactively.
The Next Wave: Transitioning from Consumer to Enterprise AI Agents
Would you blindly trust an Operator? Whether from OpenAI, DeepSeek or any other provider? Open source or proprietary? The AI agent landscape is evolving, and as these tools transition from consumer to enterprise applications, the risks will grow. Imagine an AI agent given the ability to interact with Salesforce, HubSpot, AWS, Office365 and other SaaS platforms. What happens when these agents bypass traditional security controls? Can enterprises track their actions effectively? Who ultimately controls the data processed by AI agents?
These questions must be answered before enterprises fully embrace this AI-driven future. The technology is coming, but security strategies must evolve to keep pace.
Lavi Lazarovitz is vice president of cyber research at CyberArk Labs, and Maor Franco is a director of product marketing at CyberArk.
Editor’s note: For an in-depth exploration of AI agents and their impact on cybersecurity, tune in to CyberArk Labs’ Lavi Lazarovitz on the Security Matters podcast episode, “Building Trust in AI Agents.” Lavi shares valuable insights on this subject as well as broader topics related to AI-driven automation and security. You can listen to the episode in the player below or on most major podcast platforms.























