
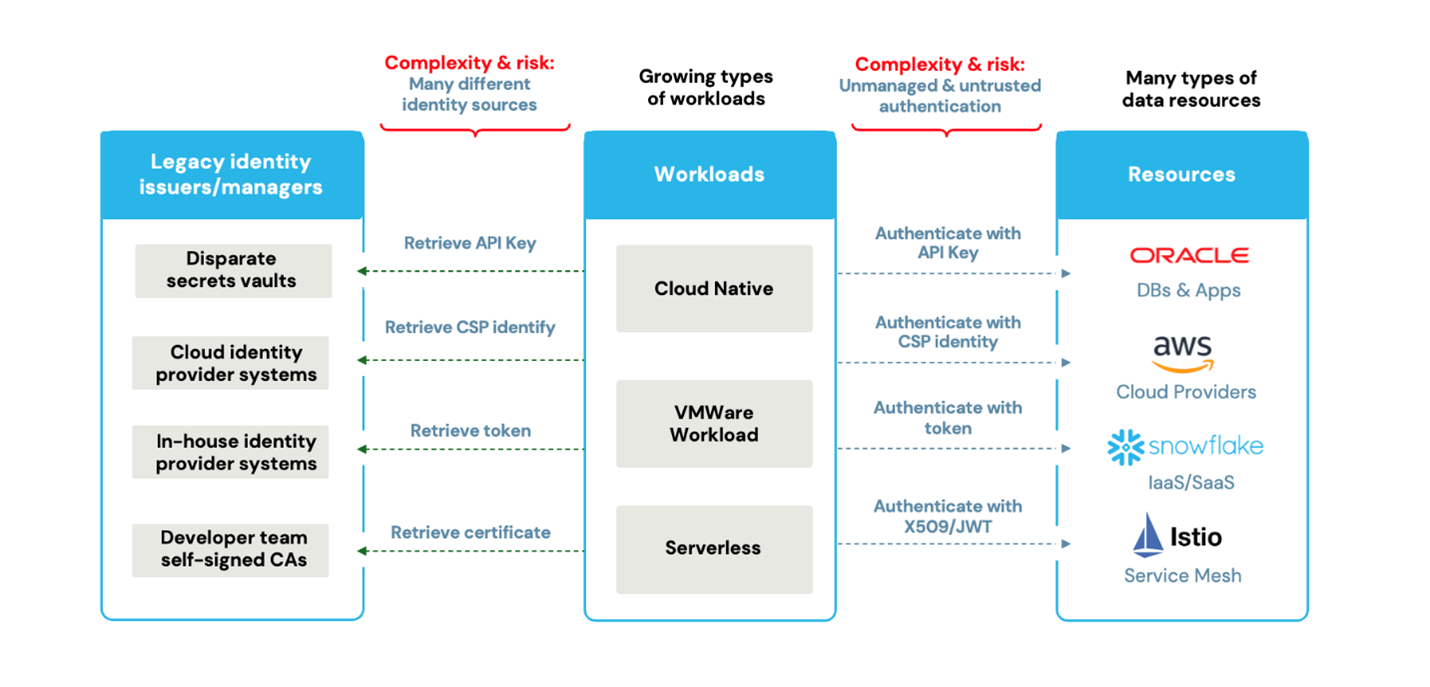
Modern workloads operate across a complex landscape—cloud platforms, virtualized environments, data centers and SaaS applications. Each requires its own authentication method, from static credentials and PKI certificates to cloud service account tokens. The rapid growth and diversity of workloads across various cloud platforms and infrastructures—each relying on a mix of secrets, API keys, access tokens and passwords—have pushed workload access complexity to the limit.
With cloud adoption surging and workloads multiplying, security risks are growing just as fast. Attackers thrive on this complexity—exploiting credential sprawl, leaked secrets, mismanaged certificates and misconfigurations—to gain unauthorized access. As environments scale, so does the challenge: How do you protect your workloads without drowning in security gaps?
Standardizing workload access for all environments using identity-driven authentication provides greater flexibility and security by allowing any workload to securely access and communicate seamlessly across dynamic clouds, SaaS partners and on-premises environments.
To help organizations achieve stronger security for workload access, CyberArk has introduced its Secure Workload Access Solution. This solution delivers a modern workload identity system that replaces the need for static credentials for high-volume cloud workloads, removes credential exposure for virtualized workloads and simplifies overall workload operation as the demand for containerized and cloud-native environments grows.
Our Vision: The Future of Secure Access
Regardless of whether workloads run across traditional data centers or high-scale Kubernetes cloud platforms, organizations want to allow them to communicate seamlessly and securely without needing to manage different types of identity systems. At the same time, security teams need to move away from inflexible practices that rely on long-lived secrets and credentials that will undermine the security of the whole environment if leaked or compromised by attackers. CyberArk’s Secure Workload Access Solution is a modern security approach that ensures every workload is assigned a unique and universal identity, always authenticated and authorized with the appropriate levels of privilege controls. Without an identity-based solution to enforce secure access for any type of workload, security teams will struggle to keep pace with the rapid expansion of workloads, leaving environments vulnerable and exposed to attacks.
Delivering Secure Access for Any Workload Environment
The CyberArk Secure Workload Access Solution is created to help organizations combat the alarming rise in cybersecurity threats that target valuable cloud workloads. By deploying a system that provisions short-lived, trusted identities to seamlessly authenticate workloads across data centers and hybrid and multi-cloud environments, organizations can replace outdated access mechanisms and mitigate the risks of long-lived secrets being exposed to attackers. This approach eliminates the complexity of managing disparate identity systems and strengthens workload security, reducing the risk of cyberattacks.
The complexity and security risks of workload authentication across diverse environments have become highly challenging. Modern workload activity relies on multiple identity sources and various authentication methods, leading to credential sprawl and security gaps.
To remove this complexity and deliver the highest security standards for workload authentication, CyberArk’s Secure Workload Access solution enables workloads to authenticate securely using a universal identity for all workload types. The CyberArk Workload Identity Manager issues and attests workload identities, while CyberArk Secrets Manager allows workloads to retrieve secrets if a credential exchange is necessary to allow that particular workload to operate, for example, perhaps accessing an established environment hosting an Oracle database. Any workload —including Virtual Machines —can use these identities to authenticate seamlessly with various resources such as databases, cloud providers, SaaS applications, and service meshes. CyberArk’s solution reduces reliance on at-risk static credentials, enhances security, and simplifies workload authentication across on-prem, hybrid and multi-cloud environments.
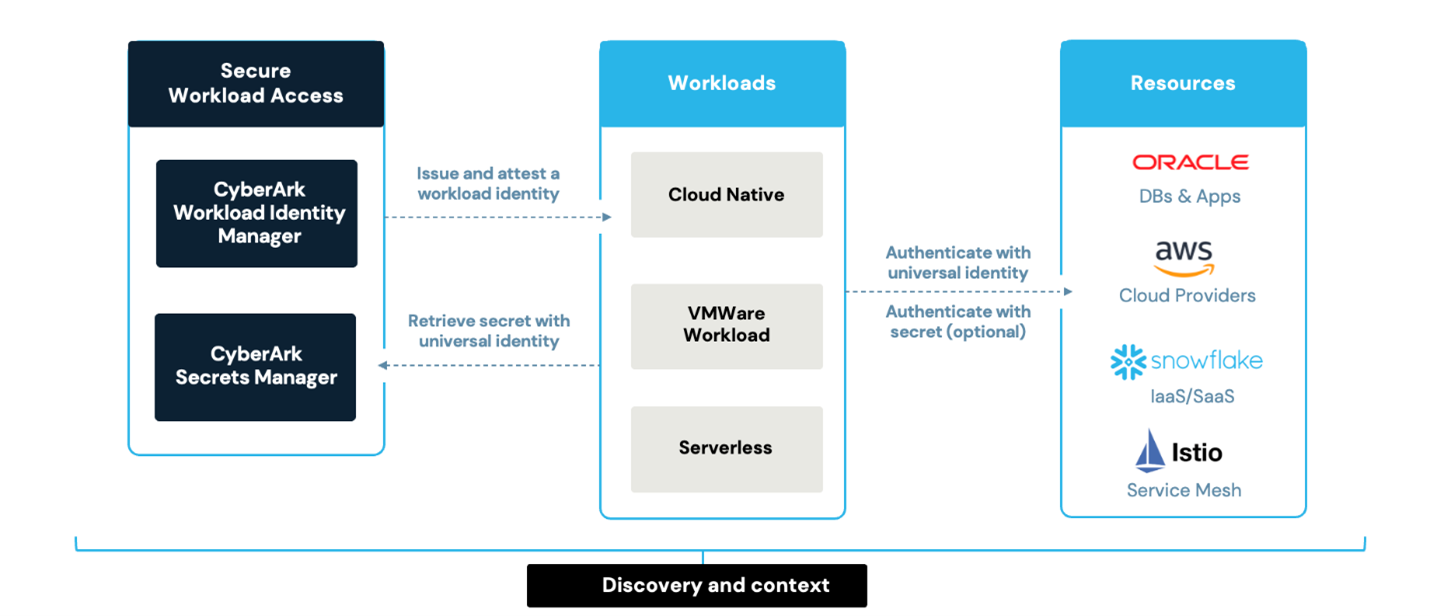
Organizations can use CyberArk’s solution to identify untrusted workload patterns to uncover security gaps caused by outdated mechanisms like long-lived credentials and unmanaged secrets. By providing discovery and context, this solution enables security teams to take the first steps to modernize workload authentication. Visibility into workload environments is essential to understand where to prioritize governance, reduce reliance on legacy systems and mitigate associated security risks.
To take these first steps, we are super excited to invite organizations to join our Secure Workload Access Partner Program and collaborate directly with CyberArk’s experts, who are developing new cybersecurity practices that leverage workload identity to combat rising threats targeting untrusted workload communication. By participating in this program, organizations can embrace modern standards for secure workload access, set clear objectives to simplify secrets management and achieve key security outcomes, including:
- Securely connect on-premises and cloud workloads across environments with unique and universal SPIFFE identities that work with existing applications, clouds and SaaS services.
- Simplify architecture design and operation as the demand for containerized and cloud-native environments grows.
- Integrate seamlessly with existing API key and access token authentication, as well as secrets management.
- Provide a modernized workload identity architecture without secrets sprawl to reduce complexity and risk of compromise, especially in high-volume, high-velocity workload environments.
- Ensure security team-approved workload identities are issued using enterprise-approved PKI, helping developer teams remain compliant and simplify operations.
- Create dynamic trust domains for authentication, reducing reliance on static credentials like API keys and access tokens to mitigate the risk of exposure, data breaches and cyberattacks.
Embrace a Modern Security Approach
It is critical for organizations to act and put securing workload access at the heart of their cloud security strategy. Existing legacy identity systems that cannot support the huge growth and security needs for modern workloads lead to environments swiftly becoming large, unprotected attack surfaces. Against the backdrop of a rising trend in high-profile security breaches, more and more organizations recognize identity-driven systems as the best approach to securing modern, dynamic workload environments.
Become part of our mission to use secrets more efficiently, secure cloud workloads, and build more resilient platforms and environments using an identity-driven solution to validate and secure access for any type of workload. Our Secure Workload Access Solution and partner program leverage a burgeoning open-source ecosystem, provide expert guidance and deliver architectural solutions to simplify securing workloads across dynamic environments. Sign up and take the first step toward stronger workload security.
Matt Barker is vice president of Workload Identity Architecture at CyberArk.























