
Secrets management is a foundational pillar of cloud security. It enables secure storage, rotation, and access control for application secrets. But in Kubernetes environments, secrets don’t just live in vaults; they move, execute, and often proliferate across clusters and containers. Without visibility into how secrets are used at runtime, organizations risk exposing sensitive data without realizing it.
Sweet Security and CyberArk have partnered to address this issue by integrating CyberArk’s centralized secrets management solution (Secrets Manager, SaaS) with the Sweet solution’s real-time runtime visibility. This partnership works to bridge a critical gap with integrated solutions that detect secrets in use, map them to Kubernetes workloads, and discover unmanaged secrets that traditional tools can’t always catch on their own.
Challenges in Kubernetes secrets management
Security teams often encounter three major challenges when managing secrets in Kubernetes cloud-native environments:
- Kubernetes secrets are not automatically secured: Many developers mistakenly assume that secrets are secure by default. In reality, Kubernetes secrets are not encrypted at rest unless explicitly configured. Unfortunately, this results in secrets being unintentionally exposed through logs, environment variables, or misconfigured RBAC.
- Lack of runtime usage visibility: Secrets managed in Secrets Manager, SaaS, may not always be tied back to active Kubernetes workloads. This makes it difficult to deprecate unused secrets or confirm whether secrets are being used securely.
- Unmanaged secret sprawl: Secrets frequently exist outside of centralized management, hardcoded into environment variables or configuration files. These unmanaged secrets are difficult to track and pose major security risks, especially when exposed in plaintext or associated with public-facing services.
Security teams are left unable to answer critical security questions: Are secrets being used by active workloads? Are they exposed? Are there unmanaged secrets embedded in the environment?
These are exactly the questions attackers hope remain unanswered. Without continuous monitoring and runtime context, secrets can persist unnoticed, creating vulnerabilities that adversaries are quick to exploit.
Why the integrated solution is valuable
Sweet Security and CyberArk bring together two powerful layers of protection: centralized secrets governance and runtime enforcement for Kubernetes environments. This joint integration helps security teams:
- Determine which secrets are managed or unmanaged
- Onboard unmanaged secrets
- Deprecate unused secrets that increase risk
- Validate secret usage across cloud-native workloads
You can’t assume that all secrets are managed. In modern cloud environments, secrets often sprawl across different sources and formats. The Sweet solution monitors runtime activity to detect both managed and unmanaged secrets, so you gain visibility as to where you stand.
With this visibility, teams can confidently take action on unmanaged secrets and help to ensure that every secret in use is tracked and protected. By linking storage to runtime, the integration supports security teams in securing secrets across the full lifecycle.
Benefits of the integration
Sweet Security and CyberArk’s joint solution helps organizations regain control over their Kubernetes secrets and improves their security posture through actionable, context-rich insights.
- Managed secrets insight: Sweet’s solution identifies secrets that are managed by Secrets Manager, SaaS, but are not actively used by workloads, helping teams safely deprecate unused secrets.
- Unmanaged secrets detection: The Sweet solution detects secrets at runtime that are not stored in any secret management tool, and enables easy onboarding into Secrets Manager, SaaS, via CyberArk Privilege Cloud.
- Contextual runtime analysis: The Sweet solution provides environmental context such as to whether secrets are tied to internet-exposed workloads, contain plaintext values, or are connected to inbound access points.
How the integration works
The integration begins with the Sweet solution deploying a lightweight sensor in the Kubernetes environment. This sensor monitors workloads, collecting near real-time data about secrets usage, including environment variables, pod manifests, and process-level details. Concurrently, Sweet’s solution queries Secrets Manager, SaaS, through its API to retrieve the inventory of managed secrets.
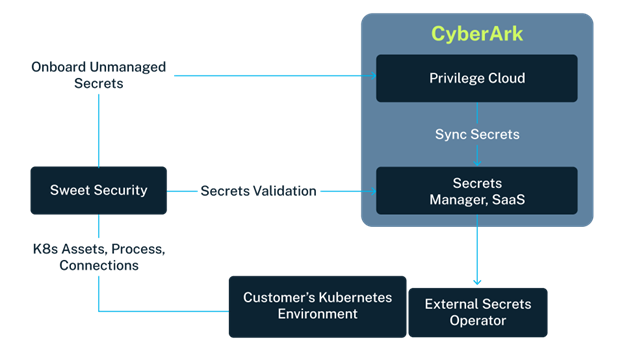
With this data in hand, the Sweet solution performs a comparison between what’s observed at runtime and what’s managed in Secrets Manager, SaaS. If discrepancies are found, such as secrets discovered at runtime that aren’t managed at all, they are flagged within the Sweet solution’s interface.
Users can initiate the onboarding process for these secrets with a single click, which redirects them to CyberArk Privilege Cloud to securely register the secret. Once onboarded, these secrets can be automatically governed with Privilege Cloud’s password rotation policies.
Secrets securely managed in Privilege Cloud are automatically synchronized with Secrets Manager, SaaS, enabling secure integration with Kubernetes.
Once in Secrets Manager, SaaS, the secret is synced into the Kubernetes environment using the External Secrets Operator. The synced secret becomes available to workloads, and the Sweet solution monitors runtime to identify when the secret is being used. If the secret aligns with one managed in Secrets Manager, SaaS, its status is updated accordingly, confirming it as both active and governed.
This streamlined process helps to ensure that secrets are not only stored securely but also monitored and validated throughout their lifecycle, all without the Sweet solution needing to directly create or manage the secrets themselves.
To experience the power of this integration firsthand, contact Sweet Security or CyberArk. Start eliminating unmanaged secrets, improving runtime visibility, and hardening your Kubernetes environments today.
Sarah Elkaim is the head of product marketing at Sweet Security and Niels van Bennekom is the manager of Tech Alliances Product Management at CyberArk.





















