
A sprawling cyber campaign is turning gamers’ hunger to gain an edge into a massive payday for threat actors who are leveraging over 250 malware samples to steal credentials and cryptocurrencies. The operation has already netted wallets containing more than US$135,000.
In this blog post, we will delve into a specific infection instance, explore its mechanisms. and share indicators of compromise (IoCs).
Introduction – an unusual campaign
The StealC group is a malware as a service (MaaS) group that provides access to their infostealer malware for various periods of time at varying prices. From what we’ve observed, most of the StealC group’s customers buy access for a month and only create a small handful of samples. In contrast, the threat actors from this campaign seem to have purchased longer access of at least three months. Additionally, we’ve observed significantly more builds being created in this campaign compared to others. Not everything they do is unusual, though. Like other threat actors, they are targeting gamers and more specifically, gamers who cheat.
Another unusual thing about this campaign is the use of StealC’s loader capabilities. StealC can be configured to double as a loader-type malware and download secondary payloads from a C2 server (doesn’t have to be the same as the first server). Once again, it appears that not many threat actors use this feature. Still, the ones running the current campaign do use the loader capability to download what appears to be a custom lightweight cryptojacker, which is meant to steal cryptocurrencies from users on infected machines.
Infection chain
As stated, there seems to be multiple infection chains targeting gamers in this campaign. Previous reports have linked the website entrarium[.]live to malware distribution, and it appears to serve as one of the starting points in this campaign as well. The Entrarium site seems to promote various tools for modding and hacking different games, but it appears that in at least some of the cases it has been used as a malware distribution vector. Trying to download one of these tools redirects one to mega[.]nz, a file sharing service that has been widely used by threat actors in previous malware distribution campaigns. Once on mega[.]nz, the victims have to manually download an archive called entrarium.zip containing the malware.
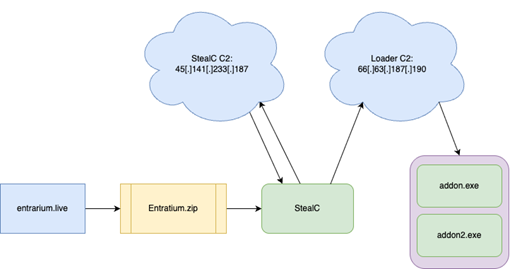
Figure 1 Infection Chain
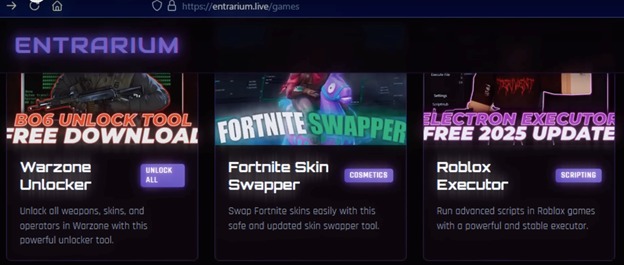
Figure 2 Entrarium website
The image shown above is a screenshot captured from the publicly accessible Entrarium website (entrarium[.]live) at the time of research. It is used strictly for educational, security research, and informational purposes.
After downloading and unzipping the zip archive, the victim ends up with several different files. Notably, in our case, the single exe file — setup.exe — was, in fact, StealC wrapped in a packer. Since we first saw the archive on VirusTotal, we can’t be sure what specific tool led to the infection. However, looking at the attached PDB file provides us with a clue. A (now deleted) GitHub repository is linked to in the pdb: https://raw.githubusercontent.com/Riz-ve/Xeno/87ae4f96f8a0927052c1120167982fb069afd1b4/*
This alone wouldn’t be enough, but some quick Googling resulted in a Reddit thread about how someone forked that repository from the PDB file and re-uploaded it after the original was deleted. The subreddit “r/robloxhackers” title suggests that the threat actors might be spreading StealC specifically through the “Roblox Executor” seen in Figure 2 on the right.
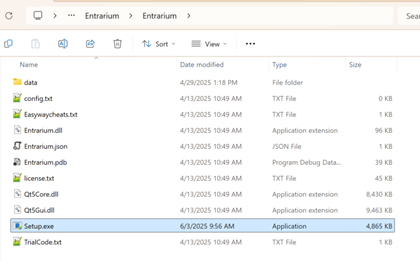
Figure 3 Unzipped Entrarium folder
As a quick side note, we assume this infection chain likely starts with the Entrarium website because of the name of the zip file, which is consistent with the names of zip files downloaded through Entrarium. Still, looking at other archives that contain samples of StealC using the same C2 server, we see things like Fortnite Hack.zip, Mod Menu V5.80.rar, and, in fact, even a Roblox Executor.zip. These file names are inconsistent with how Entrarium distributes their zips, which is why we believe there are also other infection chains.
Plenty of other researchers have analyzed the StealC malware itself, so we’ll skip the analysis. Basically, it’s an infostealer targeting various browsers and applications. The main thing to mention is that the C2 server used for exfiltrating the stolen data is:
45[.]141[.]233[.]187
This, for some reason, comes with two endpoints: /38a5d6b24dac26be.php, /7d1ca61c169b4862.php
The C2 is the original reason we looked at this campaign. Even by just looking at one of the endpoints, we already had more than 250 communicating files on VirusTotal (See Figure 4). By reviewing the behavior of some of the samples, we observe another unusual thing about the campaign: the loader capabilities. Once StealC finishes stealing data from the infected machines, it asks the C2 server if there’s any loader functionality; the server responds with a second C2 server and two new binaries:
66[.]63[.]187[.]190/work/addon[.]exe
66[.]63[.]187[.]190/work/addon2[.]exe
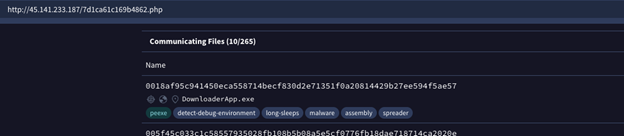
Figure 4 VirusTotal communicating files to C2
![]()
Figure 5 Decrypted C2 loader response
The first binary, addon, is packed with Themida, a popular packer used both legitimately and maliciously. The main functionality of the unpacked binary appears to be adding some exclusions to Windows Defender. Notably, excluded folders include Users, Windows, and ProgramData. These excluded folders cover a significant percentage of locations in Windows. Excluding them is not that different from disabling Defender without actually having to run a much more suspicious command to really disable Defender.
The second binary, addon2, is the cryptojacker. It’s a lightweight .NET binary likely obfuscated with some version of ConfuserEx. Luckily, using de4dot, we were able to quickly deobfuscate it.
The binary itself isn’t especially exciting. However, one thing of interest is that it copies itself to a secondary location where it masquerades as a Windows binary known as UserOOBEBroker.exe and places itself specifically into a folder called “oobe.{D20EA4E1-3957-11D2-A40B-0C5020524153}”. At first glance, this might seem like nothing special, but this specific GUID had an interesting impact. When opening the folder, we see the contents of the “Windows Tools” folder in the Control Panel. In contrast, when using the dir command from the cmd (or ls from PowerShell), we can see the UserOOBEBroker file (see Figure 6). This is rather unexpected behavior and a clever way to cause the system to hide the malicious file. As far as we can tell, this is a feature of Windows known as virtual folders or shell folders, where adding specific GUID extensions can hide the real folder and instead redirect to somewhere else. Another GUID with a similar effect seems to be {2227A280-3AEA-1069-A2DE-08002B30309D}, which redirects to the printer settings.
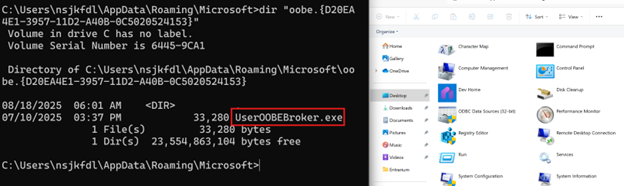
Figure 6 oobe.{D20EA4E1-3957-11D2-A40B-0C5020524153} contents in file explorer (right) compared with cmd (left)
That neat trick aside, once de4dot is used to deobfuscate the cryprojacker, it took us no time at all to find the cryptojacking abilities and the wallet addresses used. The threat actors don’t use too many addresses, but they seem to have a decent success rate. As of August 19, 2025, the wallets held around a value of US$139,405 (not quite as much as MassJacker but still significant). However, it should be noted that we couldn’t access all the wallets, so the amount may be more.
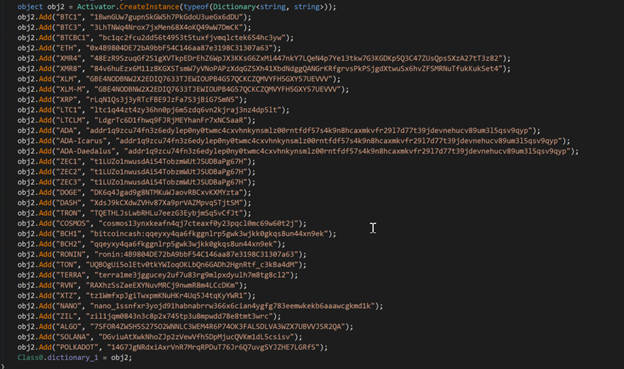
Figure 7 Cryptojacker wallets
Summary
This threat actor first caught our attention because of the large number of samples tied to a single C2, which also lasted an unusual amount of time. From there, just looking around on VirusTotal led to a lot of interesting stuff. Still, not everything here is new. Targeting gamers and, more specifically those who cheat, is a common practice of threat actors. It’s like the old saying, “Cheaters never win, and winners never cheat.”
IoCs:
URLs:
45[.]141[.]233[.]187/38a5d6b24dac26be.php
45[.]141[.]233[.]187/7d1ca61c169b4862.php
66[.]63[.]187[.]190/work/addon[.]exe
66[.]63[.]187[.]190/work/addon2[.]exe
Hashes:
Entrarium.zip: D5C5D400B35DB2351856143ED7A1900E797F7037
Setup.exe:1DED712E0BEA7AC58C8A7C27EFA88B443A165033
Addon.exe: D8C48A3206A61A1FDEAE9E2DA4306A4B94460C88
Addon2.exe: E23197A43C6C765882ABFDA0087464C7CE2223BC
StealC build IDs (partial list):
kenkaneki, fltlzt, pohuy, fuckluck, tigar, Banned, fuxwdx, witted, LJAGYX, MAMANKUNE, work13, porsche, MacTraxer, Alexxxx, bestworker7520654805, nootropum, temp_7745454979_1747924890
Wallets:
BTC1 – 1BwnGUw7gupnSkGW5h7PkGdoU3ueGx6dDU
BTC3 – 3LhTNWq4Nrox7jxMen68X4oKQ49wW7DmCK
BTCBC1 – bc1qc2fcu2dd56t4953t5tuxfjvmqlctek654hc3yw
ETH – 0x4B9804DE72bA9bbF54C146aa87e3198C31307a63
XMR4 – 48EzR9SzuqGf2S1gXVTkpEDrEhZ6WpJX3KKsG6ZxMi447nkY7LQeN4p7Ye13tkw7G3KGDKp5Q3C47ZUsQpsSXzA27tT3z82
XMR8 – 84v6huEzx6M11z8KGXSTsmW7yVNoPAPzXdqGZSXh41XbdNdggQANGrKRfgrvsPkPSjgdXtwuSx6hvZFSMRNuTfukKukSet4
XLM – GBE4NODBNW2X2EDIQ7633TJEWIOUPB4G57QCKCZQMVYFH5GXY57UEVVV
XLM-M – GBE4NODBNW2X2EDIQ7633TJEWIOUPB4G57QCKCZQMVYFH5GXY57UEVVV
XRP – rLqN1Qs3j3yRTcFBE9JzFa7S3jBiG7SmN5
LTC1 – ltc1q44zt4zy36hn0pj6m5zdq6vn2kjraj3nz4dp5lt
LTCLM – LdgrTc6D1fhwq9FJRjMEYhanFr7xNCSaaR
ADA – addr1q9zcu74fn3z6edylep0ny0twmc4cxvhnkynsmlz00rntfdf57s4k9n8hcaxmkvfr29l7d77t39jdevnehucv89um3l5qsv9qyp
ADA-Icarus – addr1q9zcu74fn3z6edylep0ny0twmc4cxvhnkynsmlz00rntfdf57s4k9n8hcaxmkvfr29l7d77t39jdevnehucv89um3l5qsv9qyp
ADA-Daedalus – addr1q9zcu74fn3z6edylep0ny0twmc4cxvhnkynsmlz00rntfdf57s4k9n8hcaxmkvfr29l7d77t39jdevnehucv89um3l5qsv9qyp
ZEC1 – t1LUZo1nwusdAiS4TobzmWUtJSUDBaPg67H
ZEC2 – t1LUZo1nwusdAiS4TobzmWUtJSUDBaPg67H
ZEC3 – t1LUZo1nwusdAiS4TobzmWUtJSUDBaPg67H
DOGE – DK6q4Jgad9g8NTMKuWJaovRBCxvKXMYzta
DASH – XdsJ9kCXdwZVHv87Xa9prVAZMpvq5TjtSM
TRON – TQETHLJsLwbRHLu7eezG3EybjmSq5vCfJt
COSMOS – cosmos13ynxkeafn4qj7cteaxf0y23pqcl0mc69w60t2j
BCH1 – bitcoincash:qqeyxy4qa6fkggnlrp5gwk3wjkk0gkqs8un44xn9ek
BCH2 – qqeyxy4qa6fkggnlrp5gwk3wjkk0gkqs8un44xn9ek
RONIN – ronin:4B9804DE72bA9bbF54C146aa87e3198C31307a63
TON – UQBOgUi5olEtv0tkYWIoqOKLbQn6GADh2HgnRtf_c3kBa4dM
TERRA – terra1me3jggucey2uf7u83rg9mlpxdyulh7m8tg8cl2
RVN – RAXhzSsZaeEXYNuvMRCj9nwmR8m4LCcDKm
XTZ – tz1WmfxpJgiTwxpmKNuHKr4Uq5J4tqKyYWR1
NANO – nano_1ssnfxr3yojd91habnabrrw366x6cian4ygfg783eemwkekb6aaawcgkmd1k
ZIL – zil1jqm0843n3c8p2x745tp3u8mpwdd78e8tmt3wrc
ALGO – 7SFOR4ZW5H5S275O2WNNLC3WEM4R6P74OK3FALSDLVA3WZX7UBVVJSR2QA
SOLANA – DGviuAtXwkNhoZJp2zVewVfh5DpMjucQVKm1dL5csisv
POLKADOT – 14G7JgNRdxiAxrVnR7MrqRPDuT76Jr6Q7uvgSYJZHE7LGRfS
– Ari Novick is a malware researcher at CyberArk Labs.





















