“Mr. Marks, by mandate of the District of Columbia Precrime Division, I’m placing you under arrest for the future murder of Sarah Marks and Donald Dubin that was to take place today, April 22 at 0800 hours and four minutes.”
– (Minority Report), 2002
While it sounds like something out of a movie, credential theft precognition is entirely possible and effective in identifying network weak spots that are likely to expose privileged credentials to compromise in the future.
We detail how in a new research report, “Predicting Risk: Credential Theft Foresight.”
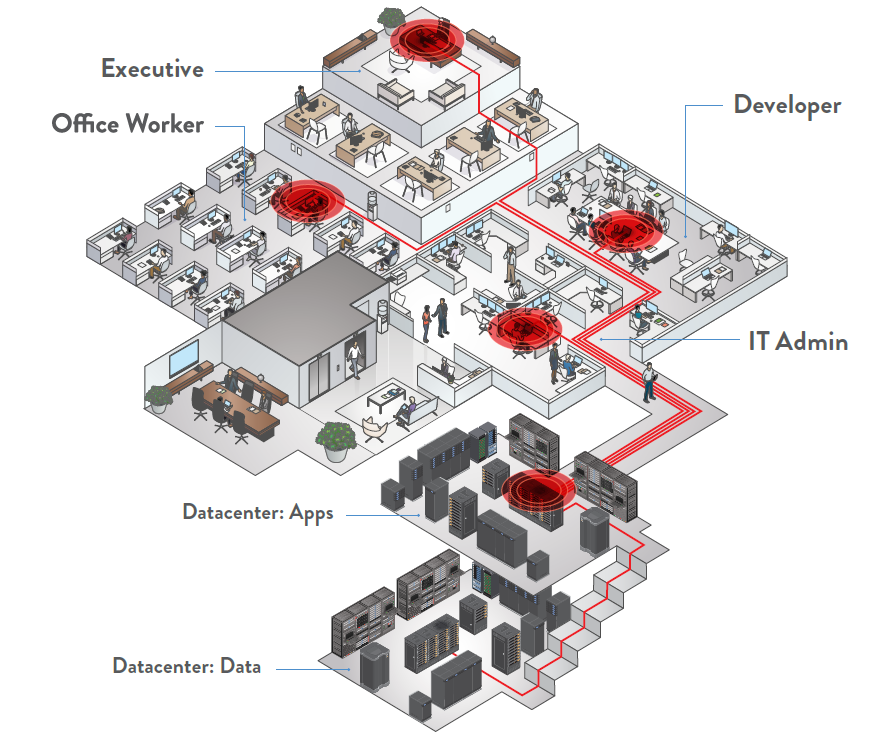
Additionally, we created a new free tool – PreCog – that helps organizations easily identify network HotSpots, which are areas predictably vulnerable to attack that act as bottlenecks for dozens of potential attack vectors. The tool is available now on GitHub: https://github.com/cyberark/PreCog.
Predictive Policing
While the oracle used in the Minority Report movie to see crimes before they happen doesn’t actually exist, law enforcement departments and intelligence agencies are using the next best thing – big data technologies.
Police departments in Santa Cruz and Chicago, for example, are already using precognition technology for predictive policing. The technology allows law enforcement departments to identify individuals most likely to commit crimes and locations that are at high risk.
It works in reducing criminal activity because it enables police to focus limited available resources on “HotSpots.”
Adapting the Technology for Credential Theft
CyberArk Labs has been working to adapt the concept for credential theft. Our vision was to develop an effective approach for identifying and neutralizing these HotSpots on an organizations network. By analyzing data reflecting login activity, security configurations and credentials exposure, we were able to pinpoint specific HotSpot machines and accounts that can be leveraged by malicious actors to escalate privileges and compromise the domain.
This predictive approach enables security teams to take action before credentials are compromised and prevent future privilege escalation and network compromise.
What it Looks Like
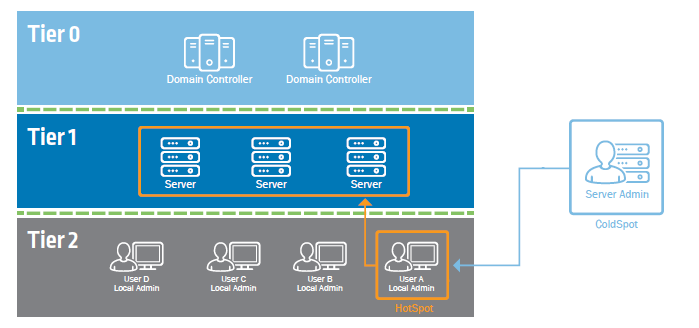
Here’s a scenario that demonstrates how credential theft precognition can prevent dynamic attack vectors. Comtoso is an organization where every user has a domain account with local admin privileges on their laptop. Tier 2, in the diagram below, represent all laptops and desktops used by Comtoso’s employees.
Comtoso’s IT team is security aware and has implemented a secure tiers architecture that restricts remote desktop connections of privileged users to less privileged tiers. However, at one point, the IT department deployed a patching service that connects to endpoints from time to time to patch cross enterprise installed software. This patching service utilizes a server admin account that has privileged access to both endpoints and servers.
As soon as the service connects to an endpoint where there is a live session of a user with local admin privileges, a new HotSpot is created. The service credentials are exposed and allow malicious actors to escalate privileges and move laterally and compromise tier 1 assets.
Looking at this scenario, there are several things to note:
- The remote desktop restriction deployed by IT does not prevent the service from connecting remotely to tier 2 endpoints, as the service utilizes WinRM and not the RDP protocol.
- The machine from which the service operates will be considered a ColdSpot, which are machines hosting privileged accounts that could be targeted by attackers in an attempt to escalate privileges. If that happens, the ColdSpot will be transformed into a HotSpot.
- The endpoint to which the service connects and exposes the service credentials on would also be considered a ColdSpot if the credentials are not at risk. In other words, if the user was not connected to the machine while the service had an open session on it then the machine would be considered a ColdSpot.
- The window of opportunity for a potential malicious actor is limited to the time the service is connected to the endpoint. Such scenarios of time limited escalation opportunity are very difficult for the SOC team to identify and neutralize as there are numerous services executing tasks on thousands of assets across the network. From the attacker perspective, it will only require patience to identify such credential exposure opportunities.
To help illustrate the concepts behind HotSpot detection, we created a new, free tool – PreCog – that helps organizations easily identify network HotSpots. The tool is available now on GitHub: https://github.com/cyberark/PreCog. The video below is a demonstration using PreCog.
Such opportunities, as demonstrated in the Comtoso case, represent only a fraction of the attack surface attackers could leverage. In real networks, there are high numbers of machines, assets and privileged accounts, and the scenario demonstrated above occurs very frequently.
Although malicious actors can choose when and where to strike, organizations can take a proactive, defensive approach to prevent privilege escalation by identifying HotSpots on their network.
Download the whitepaper Predicting Risk: Credential Theft Foresight























