
Privileged access management (PAM) is a key pillar of an effective security program. We take our role as a trusted adviser to our customers very seriously and are constantly looking for new ways to help evolve existing privileged access management programs – or guide organizations that are getting started – to prioritize risk and identify opportunities to measure success and demonstrate quantifiable value to the business. CyberArk has interviewed hundreds of organizations, including customers and those who have not yet adopted a privileged access management solution, to determine the biggest hurdles companies face when it comes to privileged access management and what they need to overcome them. We found three key trends:
- Organizations, especially those with resource constraints (basically every company, everywhere), struggle to identify the security goals that provide the most security value to their business in terms of both cybersecurity risk reduction and ROI.
- Companies that adopted a PAM solution were able to accomplish the goals they originally set out to achieve, but they didn’t know where to go next to continue improving their security. They often spoke of “best practice” programs they wanted to follow, but had difficulty applying those programs in a way that provided tangible outcomes specific to their needs.
- Organizations are looking for cybersecurity tools that provide clear advice, backed by quantitative methods to help guide them along their security journey.
CyberArk is proud to introduce the CyberArk Privileged Access Security Assessment Tool to guide organizations across all three fronts.
During an assessment, a technical expert from CyberArk or one of our certified partners will sit with your team, walk you through the process with cybersecurity assessment tool and discuss how your organization is protecting privileged accounts and access today. We frame this conversation on the CyberArk Privileged Access Security Cyber Hygiene Program, which defines seven goals organizations should strive to accomplish to build a comprehensive program to secure privileged access. Based on our findings, the CyberArk Privileged Access Security Assessment Tool will deliver three outputs that will inform not only your technical teams, but also business and IT leaders who are becoming increasingly interested in what security teams are doing to protect the brand.
Output 1: Privileged Access Security Score
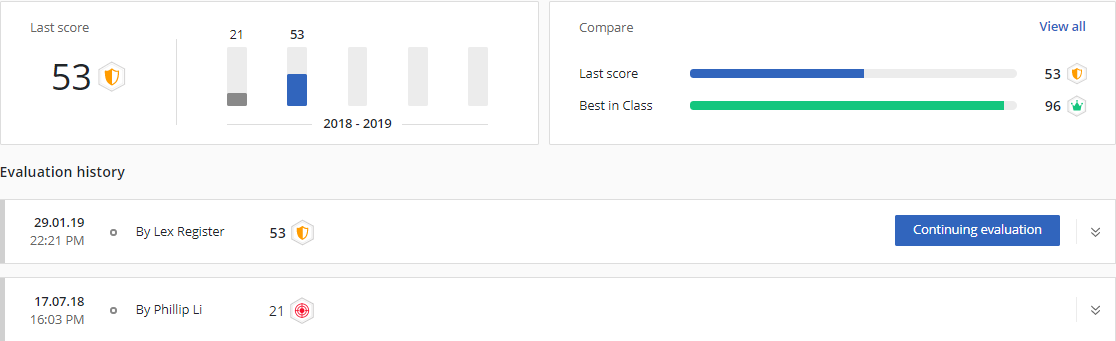
You can think of the privileged access security score as similar to a FICO or NPS score in that it reflects concrete metrics and can be tracked over time. The score is based on feedback provided to assessment and evaluation criteria developed by CyberArk. The Privileged Access Security Score is something tangible that organizations and security leaders can use to demonstrate the progress they’ve made in building a strong privileged access management program.
Output 2: Rich comparison data
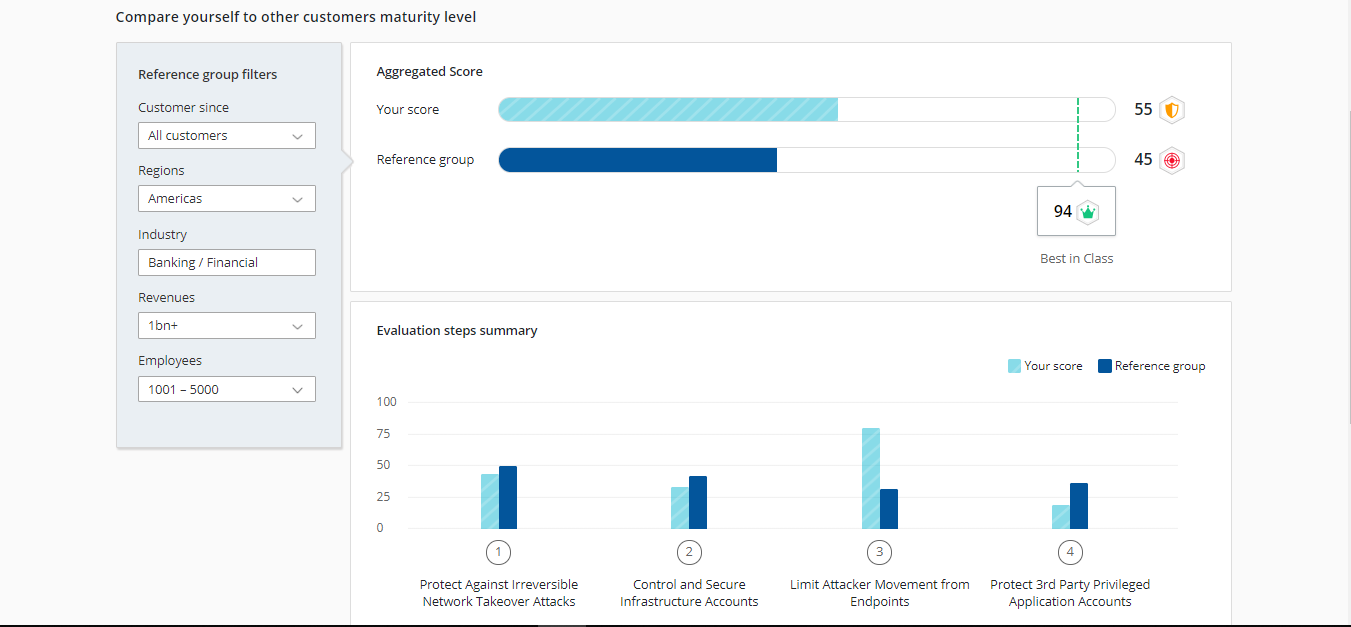
The rich comparison data provides a comparison against peers based on industry, company revenue, number of employees and a variety of other distinctions. We call this collection of attributes a reference group. This data is crucial for leaders interested in understanding how their investment compares to others in their reference group.
Output 3: Assessment report, complete with specific recommendations



For companies that have completed an assessment already, this output has been cited as the most significant in terms of direct value to the business. The assessment report provides companies with a recap of their most recent assessment, a visual history of their assessments, the comparison data from above and, most importantly, specific advice based on their individual feedback.
We give companies technical and process recommendations for the two of the seven goal of the assessment. These are the areas they should prioritize in the next 12-24 months and the assessment report clearly defines the actions to take to improve privileged access management and protect your organization’s business.
Read the press release to learn more about how the industry, including leading cyber security insurance firms, are leveraging Privileged Access Security Assessment Tool from CyberArk. Get started by filling out a request form or by reaching out to your CyberArk representative.























