
The evolution of LockBit – one of the largest ransomware as a service (RaaS) operations in history – exemplifies continued attack commoditization and underground innovation. Since LockBit 3.0 (aka LockBit Black) launched in June 2022, the latest version continues to make headlines – recently for exploiting the Log4j vulnerability and abusing a popular anti-virus system to evade detection. As ransomware threats continue to morph, such reports highlight the importance of defense-in-depth security.
What is LockBit Ransomware?
Known as “ABCD” when it first appeared in September 2019, LockBit soon morphed into a RaaS affiliate program, a subscription-based business model that allows criminals of all skill levels to purchase off-the-shelf ransomware from developers who earn a percentage of each ransom payment.
Relaunched in mid-2021 with enhanced features, LockBit 2.0 was touted by its creators as the “fastest encryption software all over the world.” This was eventually put to the test by researchers who found the claim to be true. LockBit 2.0 quickly skyrocketed in popularity, used by threat actors to target both Windows PCs and Linux hosts (ESXi servers) in double-extortion attempts. As ZDNet put it, “LockBit’s operators use any method available to compromise a network, as long as it works.” In February 2022, the FBI warned organizations to bolster ransomware defenses against LockBit 2.0, which followed variations of this attack chain:
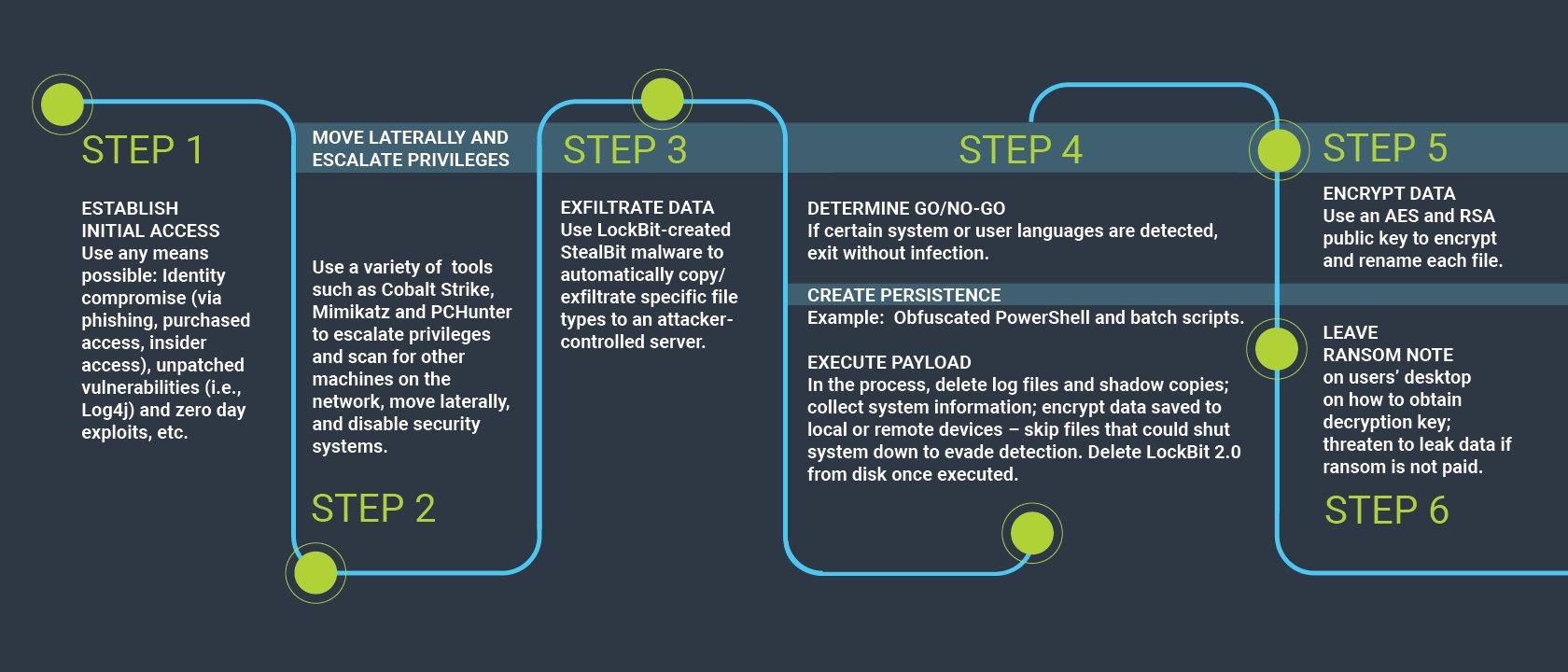
LockBit 2.0 attack chain example. (Sources: CyberArk Labs, FBI, CSO)
All the while, the highly organized LockBit group continued to innovate and uplevel its operations, joining forces with other ransomware gangs, promoting underground hackathons to attract new talent, and even recruiting corporate insiders to help establish initial access into their employers’ networks. Competitor Conti’s reported disbandment appears to have further strengthened LockBit’s market position. CSO reports that LockBit was responsible for 40% of all analyzed ransomware attacks in May 2022. After a product revamp and beta testing period, LockBit 3.0 was released in late June 2022 with a brazen “Make Ransomware Great Again” tagline and new rules of engagement for both affiliate members and victim organizations.
What’s Most Notable About LockBit 3.0 and Recently Observed Activity?
Threat researchers from around the world continue to work to obtain and analyze LockBit 3.0 samples and share findings to help organizations strengthen ransomware defenses. Based on these collaborative efforts, media reports and CyberArk Labs’ analysis to date, here are three notable LockBit 3.0 characteristics:
- A first-of-its-kind bug bounty program and new leak site. In March 2022, Microsoft researchers published a report on critical bugs in LockBit 2.0 – a potential contributing factor to the 3.0 release and LockBit’s warning to affiliate program candidates that “we are constantly trying to be hacked and harmed in some way,” as reported by VentureBeat. With a bug bounty program, the LockBit gang is working to get a handle on their own malware vulnerabilities so they can address them, and also prevent researchers and responders from reversing the ransomware’s impact.
- Anti-analysis protections. One of the most interesting changes made was the introduction of a unique passcode for every LockBit 3.0 sample. Without the passcode, the sample won’t run. This means that researchers, competitors, or whomever cannot analyze the malware dynamically without a password. Such anti-analysis measures could soon be embraced by other ransomware groups, and it’s a potential ransomware trend worth tracking.
- Novel living off the land (LotL) techniques that weaponize critical security tools. Threat researchers have reportedly observed LockBit 3.0 actors obtaining initial access via the Log4j vulnerability, employing new tactics to weaponize legitimate security tools that often operate outside of installed security controls, and evade detection by EDR and traditional anti-virus tools.
These recent revelations emphasize the need for threat detection controls and policies that can help identify and block suspicious activities that may be linked to Log4j or other critical vulnerabilities right away. For instance, configuring policies to detect and block instances of java.exe being used as a parent process for cmd.exe or powershell.exe is one way to block potential Log4j and similar exploitation, as it is very unlikely that java.exe would initiate these processes in a legitimate scenario. Additionally, continuous control of all launched and running programs and their associated privileges will add significant friction for attackers if they attempt to launch a ransomware payload, tamper with security and recovery controls, or try to chain vulnerabilities.
Why Anti-Ransomware Protection Requires Defense in Depth
Ransomware actors will continue to evolve their approaches and, as evidenced by LockBit 3.0, every product version is an opportunity to change up the game.
That’s why effective anti-ransomware protection involves locking down the endpoint and working to prevent malware from being successful at every step of the cyber kill chain – but never at the end-user’s expense. Embracing the right set of multi-layered defenses, including privileged endpoint security controls, can help strike a balance between security and productivity – protecting endpoints while automating access elevations for end-users in a transparent manner to dismantle the cyber kill chain, forcing the attacker to look elsewhere.
Here’s what this looks like: Consistent least privilege enforcement (both for initial system access and continued operation on endpoints – workstations and servers alike), layered with foundational endpoint controls such as a credential theft blocking, targeted data-centric anti-ransomware policies, application control, MFA, continuous threat detection and response, consistent OS and software patching and network segmentation, will help position organizations to detect and defend against ransomware attacks of all varieties.






















