It’s been a staple of horror movies and espionage thrillers for years — the idea that something innocuous or trusted could suddenly turn against you. Unfortunately, what’s fodder for great fiction can also easily become cybersecurity reality.
In the digital realm, among the lurking sources of angst are living off the land (LotL) ransomware attacks — of course, their folksy name belies their insidious danger. The recent Kaseya supply chain ransomware attack is just the latest example; threat actors used the organization’s own technology resources against them to scale their attack — a hallmark of LotL. By infiltrating an endpoint and then gaining access to tools that were supposed to be there, they were able to worm deeper into the multi-layered network environment without raising alarms. These kinds of attacks give hostile agents two things they covet: access and time. You don’t know they’re there — you don’t know what they’re doing — and you may not know what they take with them when they go.
While these LotL scenarios don’t always end with a ransomware attack, the two increasingly go hand in hand and are as difficult to assess as they are to prevent. An effective protection strategy begins with a solid grasp of what constitutes an LotL ransomware attack and how it can impact your organization.
Let’s first review a quick history and common LotL techniques and procedures before assuming an attacker’s role to best explain some of the many ways this could go down.
The Lay of the Malevolent Land
Around 2017, fileless malware attacks started to gain mainstream attention after reports of hostile infections of legitimate IT systems belonging to the Democratic National Committee and other large organizations emerged.
Fileless malware made LotL possible. By eliminating the need to store the malicious payload in a file or install it directly on a machine, attackers could slip past anti-virus and other traditional endpoint security tools and move laterally through the environment, escalating privileges and uncovering new levels of access, until they reached the ultimate prize: systems, applications and databases containing critical business assets such as customer data and intellectual property.
To linger in systems and “live off the land” without detection, fileless malware often poses as a trusted tool with high privileges and access — such as legitimate tools used by system administrators to automate tasks and manage configurations. This allows attackers to monitor the environment, dump credentials and essentially take their time poking around under the guise of whitelisted, or trusted, tools.
Identifying, let alone stopping, these attacks is extremely difficult — especially if you’re dealing with a sophisticated ransomware actor who’s specifically targeting your organization. This is when effective cybersecurity information sharing can make all the difference and why businesses around the world rely on MITRE ATT&CK, an open-source framework comprising a vast knowledgebase of real-world adversarial tactics, techniques and procedures (TTPs) with a corresponding database that tracks the activities of numerous threat actors and cyber-criminal syndicates.
Just as the MITRE ATT&CK framework’s name implies, the system mimics the behavior of real-world attackers, which helps IT, information security and compliance organizations more effectively assess risk, identify security gaps and patch up vulnerabilities. By using a common taxonomy, security professionals including SOC staff, red and blue teams, pen testers and security vendors, can easily exchange information and collaborate using the same language, ultimately strengthening cybersecurity strategies.
Know Thy Enemy
At the core of the ATT&CK system is the idea that cybersecurity experts need to think like attackers. Unlike other security frameworks that focus on the tools and malware used by malicious actors, ATT&CK focuses on how adversaries interact with systems during an attack — so that’s exactly what we’re going to do here. This will be an attempt at a kind of “how-to” guide, with the understanding that no two attacks are necessarily alike. The LotL path is not linear and has a bit of a “choose your own adventure” element to it. It’s about reading the environment and developing an approach based on what you find there.
Let’s start with the consistencies. Most LotL attacks follow a similar pattern: abuse identities to infiltrate an enterprise network, compromise systems, escalate privileges and move laterally until they gain access to the sensitive systems they need to execute their attack or push ransomware.
But within each step exist divergent paths that make tracking and anticipating such attacks so challenging. Using ATT&CK analysis, we can break down behaviors and red flags to look for within critical stages of an LotL ransomware attack to help speed detection and reduce exposure and damage:
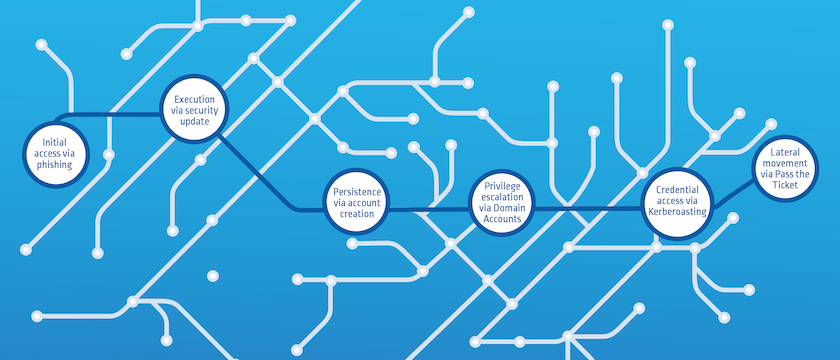
Stage 1 — Make First Contact
After pre-attack preparations — from reconnaissance to resource development — are complete, the attacker has myriad ways to establish an initial entry point into the network. Many rely on tried-and-true phishing techniques, while some gain access by injecting malicious code or cross-site scripting into an otherwise normal online browsing experience to open vulnerabilities — known as a “drive-by compromise.” Or, as seen frequently in recent months, attackers could manipulate software before it reaches their targeted final consumer in a supply chain attack. Any one of these techniques — or a combination of more than one — will open the door.
Stage 2 — Run Your Executables
Once inside, the ransomware attacker’s goal is to run the malicious code through a variety of options, from abusing popular IT admin tools to manipulate commands and execute processes, or even create uniform environments for remote and local access to corporate systems, which can open attack pathways. Additionally, as seen in the SolarWinds supply chain attack, adversaries can modify source code and push a seemingly innocuous security update, which is actually the malware in disguise.
Stage 3 — Maintain the Foothold
This is the stage when LotL truly becomes LotL — when the attacker sets up shop and takes full advantage of the time and anonymity their techniques afford them. At this stage, the attacker may create their own accounts to maintain access to victim systems or use Logon AutoStart to execute programs automatically during system boots, maintain persistence or gain access to more powerful privileges on compromised systems while they go about their slow and deliberate work.
Stage 4 — Take it Up a Notch
Now that the attacker is settled in, it’s time to gain higher-level permissions. Many attackers go for domain account credentials — particularly those of domain administrators who have far-reaching access to Tier0 systems like Active Directory and prefer service accounts linked to non-human identities, as these account passwords are infrequently changed. Through techniques like OS credential dumping, attackers obtain and discard login information as they creep closer to the keys for the most powerful systems. Again, this is all conducted under the guise of “legit” accounts and tools to evade defenses.
Stage 5 — Forge an All-Access Pass
With domain admin privileges in hand, the attacker can stealthily manipulate domain controllers, pulling password data from Active Directory by running DCSync, which may yield current and historical hashes of potentially useful accounts or attempt to access Local Security Authority (LSA) secrets for service account information. One technique called “Kerberoasting” can be used to crack passwords offline. Attackers can also try to perform a Kerberos authentication “Golden Ticket” attack, which can lead to a complete network takeover and massive business disruption.
Stage 6 — Move with Ease to Accomplish Goal
Now free to move without resistance or fear of detection, the attacker focuses on lateral movement to leave no digital stone unturned. Their forged Kerberos keys allow them to “pass the ticket,” circumventing security and access controls while they search for data to mine and wait for the perfect moment — often when the victim organization is most vulnerable — to exfiltrate sensitive data and then encrypt files and demand a ransom. In other instances, the attacker may use valid accounts to interact with a remote network share using Server Message Block (SMB), allowing them to perform actions, purportedly as the logged-on user, to accomplish their goals.
So now that we’ve seen a few pages of the opponent’s playbook, what can we do about it? With so many proven techniques at attackers’ disposal, it can be challenging to figure out how to address areas of vulnerability or where to begin. Devising an effective ransomware protection strategy mapped to the MITRE ATT&CK framework requires organizations to investigate areas across the attack chain that present the highest levels of risk and prioritize them accordingly. But when it comes to mitigating the damage done by LotL attacks, stage one is typically the place to start.
A multi-layered endpoint security approach combining least privilege defense, strong authentication for identities, credential theft protection, application control and ransomware blocking will make it significantly harder for attackers to gain entry and maintain persistence. For once they get a foothold, it becomes increasingly easy for them to cover their tracks and scale their efforts.
As recent history shows, it may be impossible to completely wall off your “land,” but you can make it a lot more inhospitable to those seeking to plunder it.























