
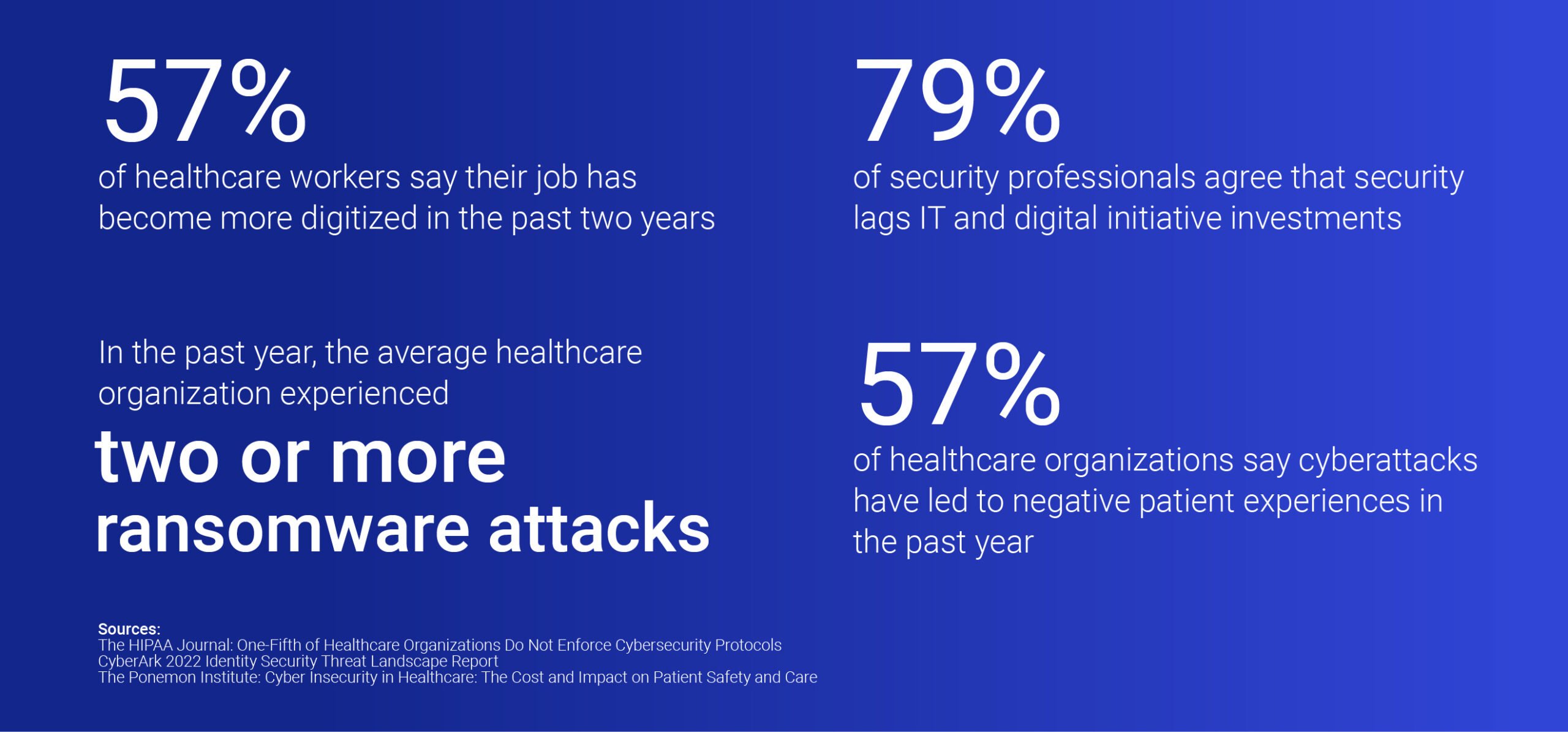
Healthcare cyberattacks are increasing in “frequency, severity and sophistication,” said Nitin Natarajan, U.S. Cybersecurity and Infrastructure Security Agency (CISA) deputy director, in his recent HIMSS23 Healthcare Cybersecurity Forum keynote. Attacks on hospitals have surged by 86% since 2021, with the average healthcare organization experiencing two or more ransomware attacks in the past year. “And this is going to continue to increase,” Natarajan warned.
Staying one step ahead of “well-funded” and “capable” adversaries requires vigilance and collaboration – as well as a close look at electronic health record systems (EHRs), the heart of modern healthcare IT. Because EHRs contain electronic medical records (EMRs) – essentially, digitized patient medical charts – EHRs are top targets for healthcare cyberattacks.
Healthcare Transformation, the Electronic Health Record Era and Rising Cybersecurity Risk
Many organizations adopted EHR systems as part of digital transformation pushes to curb inefficiencies and facilitate data sharing. According to HIPPA Journal, 57% of healthcare workers say their job has become more digitized over the past two years. While digitization improves many processes and experiences, it also tends to complicate IT systems. When system A won’t “talk” to system B, clinicians can waste valuable time piecing together patient medical history, medication allergies, comorbidities and more.
Transformation projects can also create security gaps, driving up risk and cybersecurity debt. Security professionals across industries overwhelmingly (79%) agree that security lags behind IT and digital initiative investments, according to the CyberArk 2022 Identity Security Threat Landscape Report. Meanwhile, a 2022 Ponemon Institute study revealed that 89% of healthcare organizations experienced a cyberattack in the past year, negatively impacting patient outcomes for 57% of surveyed organizations.
The same CyberArk report identified privilege escalation as the number one attack vector of risk for healthcare organizations. By stealing credentials via phishing, social engineering or other techniques, threat actors can compromise or abuse identities, assess a healthcare IT environment and escalate privileges to reach their goal: stealing EMRs or holding them for ransom. According to the U.S. Department of Health and Human Services, protected health information (PHI) found within EMRs gives criminals more details than any other record, making healthcare data the most valuable on the dark web.
Simplifying EHR Authentication Workflows to Improve Healthcare Outcomes
On the flip side, for defenders, healthcare data confidentiality, integrity and availability are more important than ever. To achieve these goals, multi-factor authentication (MFA) is a crucial security layer.
Most healthcare organizations already have a two- or multi-factor authentication method in place due to regulatory compliance requirements. For example, U.S.-based clinicians must go through MFA before prescribing or approving prescriptions for opioids and other controlled substances. Yet not all MFA is created equal, and many organizations use insecure methods that put EHR systems and patient data at risk. A newly released HIMSS Cybersecurity Study reveals that 57.23% of healthcare organizations still use basic usernames and passwords and 58.49% use traditional SMS-based authentication (notorious for facilitating SIM-swapping attacks), while just 9.43% use phishing-resistant (or passwordless) MFA factors, such as a FIDO, QR codes, biometrics or physical tokens.
HIMSS survey authors call for more robust authentication measures, writing, “Healthcare needs to adopt passwordless multi-factor authentication as too many compromises happen nowadays involving passwords with as many as 921 passwords compromised each second.”
Security isn’t the only factor in play. Usability is just as important for hard-working healthcare workers. Constantly re-authenticating into EHR systems to access patients’ EMRs, enter health information and complete prescriptions is not only time-consuming, it’s distracting. In fact, many clinicians report negative EHR-related experiences. According to a recent Annals of Family Medicine study, 79% of clinicians say they maintain less eye contact when using an EHR system, 53% say they listen less carefully and 62% say EHR use makes patient visits less personal. Back-to-back patient visits leave clinicians little time for follow-up, yet many can’t securely access patient records outside the hospital network or from outside devices.
Also of particular interest, the same study found that most patients view EHR systems positively (91%). This suggests that many EHR challenges could be solved by making clinicians’ lives easier — for instance, by giving clinicians access to everything they need within an EHR with single sign-on (SSO). U.S. Surgeon General Vivek Murthy agrees. In a recent advisory, he urged organizations to “optimize technology to increase time spent between health workers and patients.” He outlined specific examples such as “simplifying EHR-based workflows and addressing patient and health worker usability issues with virtual care.”
Healthcare professionals shoulder an enormous burden. Suffering from severe workforce shortages and burnout, they are leaving the industry in droves. The World Health Organization estimates a global shortfall of 10 million health workers by 2030. Lightening clinicians’ workloads in every way possible is imperative. Our health — and the future of our healthcare systems — depends on it.
Lee Godby is a director of business development at CyberArk.





















