
Many cybersecurity concepts are complex and often difficult to explain to non-technical audiences. Kerberoasting? Golden SAML? Huh? This can make it challenging for security leaders to communicate urgency and gain stakeholder support for important projects.
Educating business stakeholders and consumers on the importance of securing personal and professional digital identities is precisely why Identity Management Day (#IDMgmtDay2022 ) was established by the Identity Defined Security Alliance (IDSA) and National Cybersecurity Alliance. As you embark in awareness-building initiatives this April 12, consider framing the growing digital identity problem in terms of “debt” — a concept that’s as universally understood as it is dreaded.
Based on findings from The CyberArk 2022 Identity Security Threat Landscape Report,* which was released today, many organizations are heading deeper into cybersecurity debt by prioritizing digital initiatives, such as accelerating cloud migration, developing new digital services and supporting work from anywhere models, while putting off identity-focused security protections.
Rising Cybersecurity Debt Can Hamstring Innovation and Future Success
Whether it’s splurging on a big vacation, buying a new home or launching a new interactive app for your customers, you take on debt to get something you need (or want) today by deferring “payment” until tomorrow. But, as the saying goes, “Debt is like any other trap: easy enough to get into but hard enough to get out of.”
Cybersecurity debt is a type of technical debt — a term first introduced by computer programmer Ward Cunningham to explain the future cost of reworking a solution that wasn’t completely or properly designed from the start. Cybersecurity debt specifically refers to the unaddressed security vulnerabilities that accumulate in an organization’s IT environment as new systems and technologies are added over time. When cybersecurity debt isn’t paid off promptly (in other words, if security issues aren’t addressed right away), “interest” can quickly build, making it difficult and costly to repair those shortcuts down the road.
Getting bogged down in cybersecurity debt ultimately leaves fewer dedicated resources for sustaining a productive and efficient business.
The Enterprise Digital Transformation Trade-Off
Though volatility remains a top business challenge, standing still is not an option. Nearly every surveyed organization (99%) accelerated a business or IT initiative within the past 12 months in the push for continued resiliency and competitive differentiation.
But transformative projects are rarely achieved without making waves, especially when it comes to large-scale technology initiatives. Each one creates a massive swath of new interconnected digital identities — the virtual ID cards of cyber space — each containing credentials of the human or machine linked to it. These digital identities are used to facilitate interactions and broker access, often to sensitive corporate data and assets required to perform a job or function.
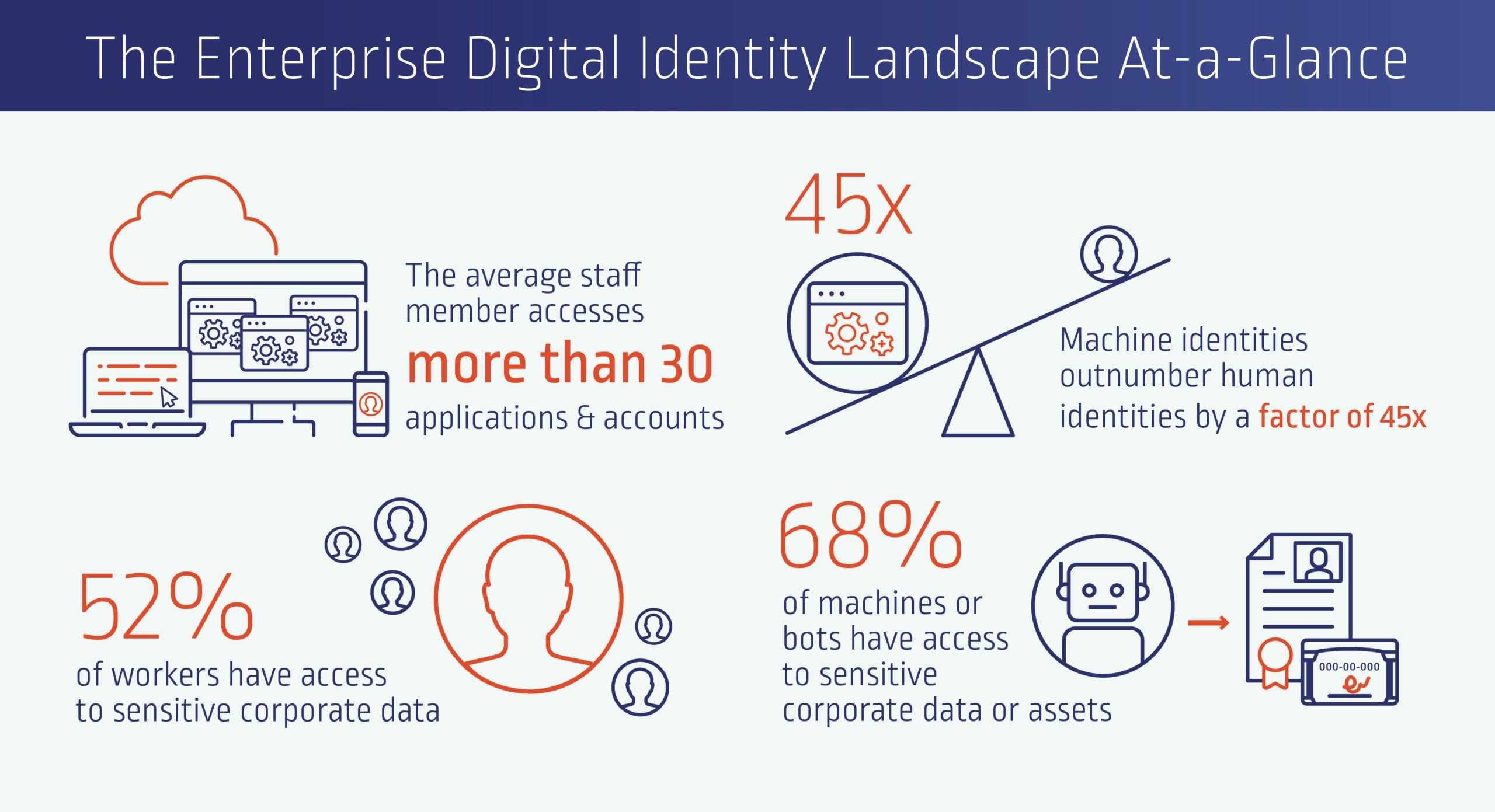
A High-Interest Digital Identity Debt Dilemma
It takes just one compromised identity for a threat actor or malicious insider to launch an attack and start escalating privileges to move deeper into an environment in search of valuable assets. This is likely why respondents ranked credential access as their No. 1 area of risk. Yet 79% said their organization hasn’t prioritized the protection of critical data and assets. Instead, they’re moving full steam ahead with initiatives respondents said could introduce significant risk.
This dissonance has created substantial cybersecurity debt that continues to mount as “interest” accumulates in the form of new unmanaged identities across every major IT infrastructure component.
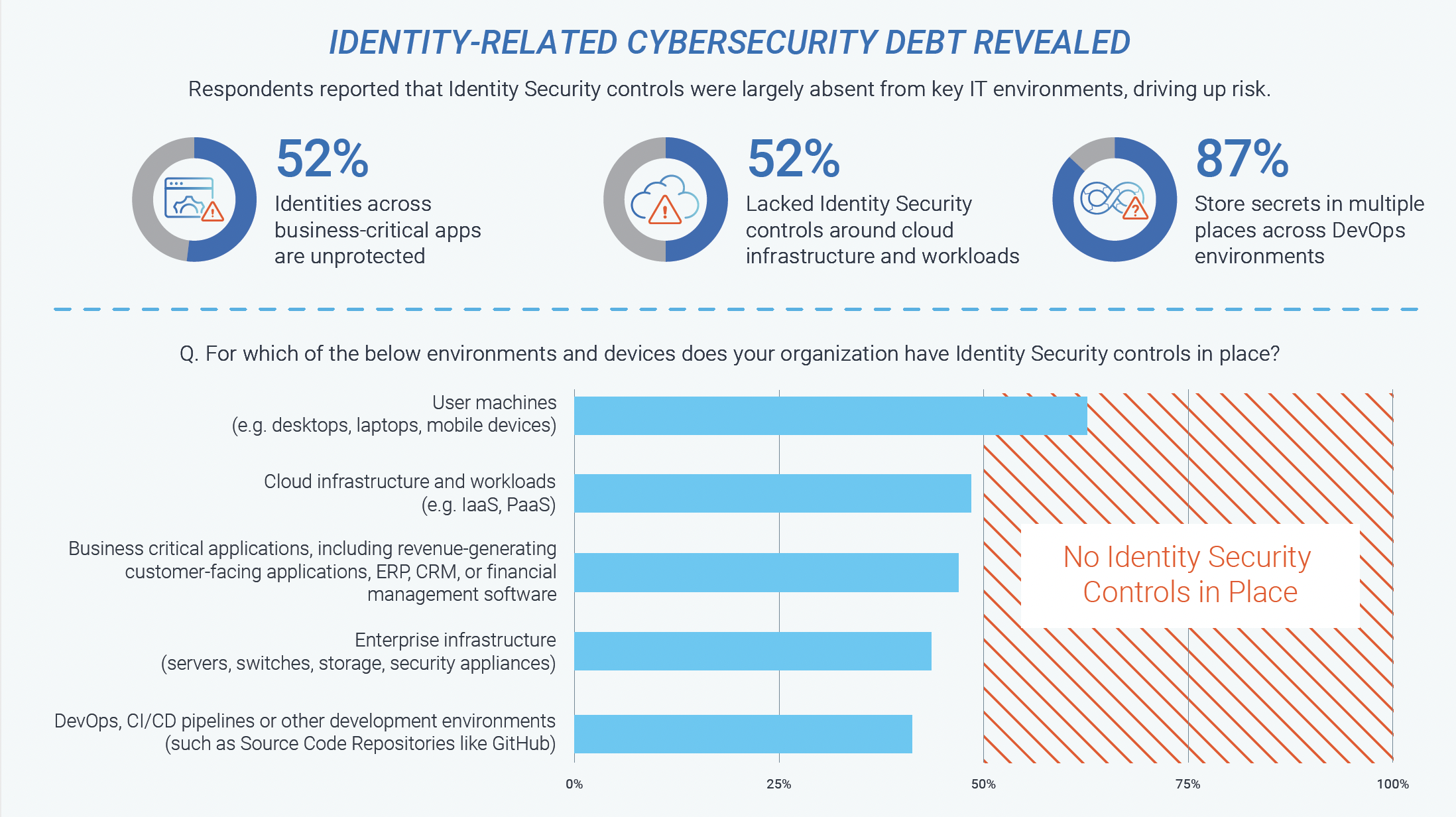
This Identity Management Day, Create a Feasible Pay-Off Plan to Tackle Cybersecurity Debt
As in our personal lives, a certain level of debt is sometimes necessary. If your car dies and you need one to get to and from work, you may be forced to take out a loan. Likewise, many organizations had no choice but to fast-track projects that could keep operations running amid pandemic-driven challenges, making some security trade-offs along the way.
The key now is to tackle this debt responsibly before balances become too unwieldy, or worse, organizations face “bankruptcy” for failing to evolve at the rate of technology change due to poor security decisions.
To their credit, some respondents have committed to turning things around. Notably, almost all respondents are embracing Zero Trust cybersecurity models of “trust nothing; verify everything,” with half (50%) of them prioritizing Identity Security tool implementation as one of their top three initiatives to pave the way.
And in the face of continued ransomware attacks and other emerging threats, they’re approaching cybersecurity debt and risk reduction efforts more holistically — not only emphasizing important technical controls such as multi-factor authentication (MFA) and least privilege but also people-centric initiatives such as security awareness training to embed security-conscious behavior into their cultures. This defense-in-depth approach reflects a widespread “assume breach” mentality, which 82% of respondents say they’ve embraced.
Digging out of cybersecurity debt takes time and for many organizations, there’s much work to be done. Creating a risk-based plan can help them identify ways to make quick, high-return “payments” and then follow a feasible timeline for reducing the remaining cybersecurity debt. With a solid identity-centric risk plan in place, organizations can effectively strengthen defenses against emerging threats while advancing key initiatives to propel their business forward.
To learn more, download The CyberArk 2022 Identity Security Threat Landscape Report.
*The CyberArk 2022 Identity Security Threat Landscape Report surveyed 1,750 IT security decisions worldwide with organizations of at least 500 employees or more across all private and public sectors.























