
For many of us, the term “cloud security breach” conjures meticulous attack plans executed by sophisticated criminal syndicates.
But in reality, “attacks” can be far more mundane: maybe some forgotten credentials, a few default permissions, or a user whose cleanup to-do list never got done.
At the center of these incidents are standing privileges: long-lived access rights originally granted for legitimate tasks. Developers, data scientists, third parties, and other users frequently request elevated access to cloud resources across multi-cloud environments. But when the task is completed, those privileges often remain—and can become a welcome mat for bad actors.
Let’s look at a few real-world scenarios to understand why traditional defenses keep falling short, and how zero standing privileges (ZSP) flips the script on both external attackers and malicious insiders.
Standing privileges: The hidden gateway to credential theft
Imagine a DevOps engineer hardcoding cloud credentials into a CI/CD script during a last-minute push to production. The job ends, but the credentials remain.
A few weeks later, that repository is cloned onto a compromised endpoint, and a credential harvesting script pulls the secrets and uploads them straight to a public forum.
Static credentials, persistent roles, and overprovisioned access across major cloud service providers become low-effort entry points into high-value systems. This method of exploiting static credentials and overprovisioned access is how external attackers thrive in multi-cloud environments: not by cracking through firewalls, but by collecting leftovers.
Our “How to Hack a Cloud” video series explores how minor missteps in cloud configuration can lead to outsized consequences. In the access mismanagement-focused episode below, a long-lived access credential the user left behind after a one-time task becomes an attacker’s entry point into cloud infrastructure. The video walks through how the compromise unfolds, why static credentials are a persistent risk, and how modern access strategies can neutralize that risk by replacing long-lived secrets with short-lived, ephemeral credentials.
Insider threats in the cloud: How authorized users become silent saboteurs
Not all threats need to infiltrate. Some already have inside access.
Vindictive insiders can be dangerous because they have the power to exploit legitimate access not by bypassing controls, but by blending into them.
After all, they already possess authorized access to critical systems with sensitive information. They understand internal processes, know where essential data resides, and can maintain normal behavioral patterns to avoid detection.
Imagine a privileged user with a grudge—and administrative access. They can set up a scheduled job in a cloud environment designed to quietly modify or delete critical resources, weeks after they leave. The attacker disguises it to look like a maintenance task—but it’s not.
No brute force. No red flags. Just routine clicks in the S3 console and a policy tweak that eventually erases secret recipes and customer data. The access is valid, and the commands are standard. But the damage is permanent.
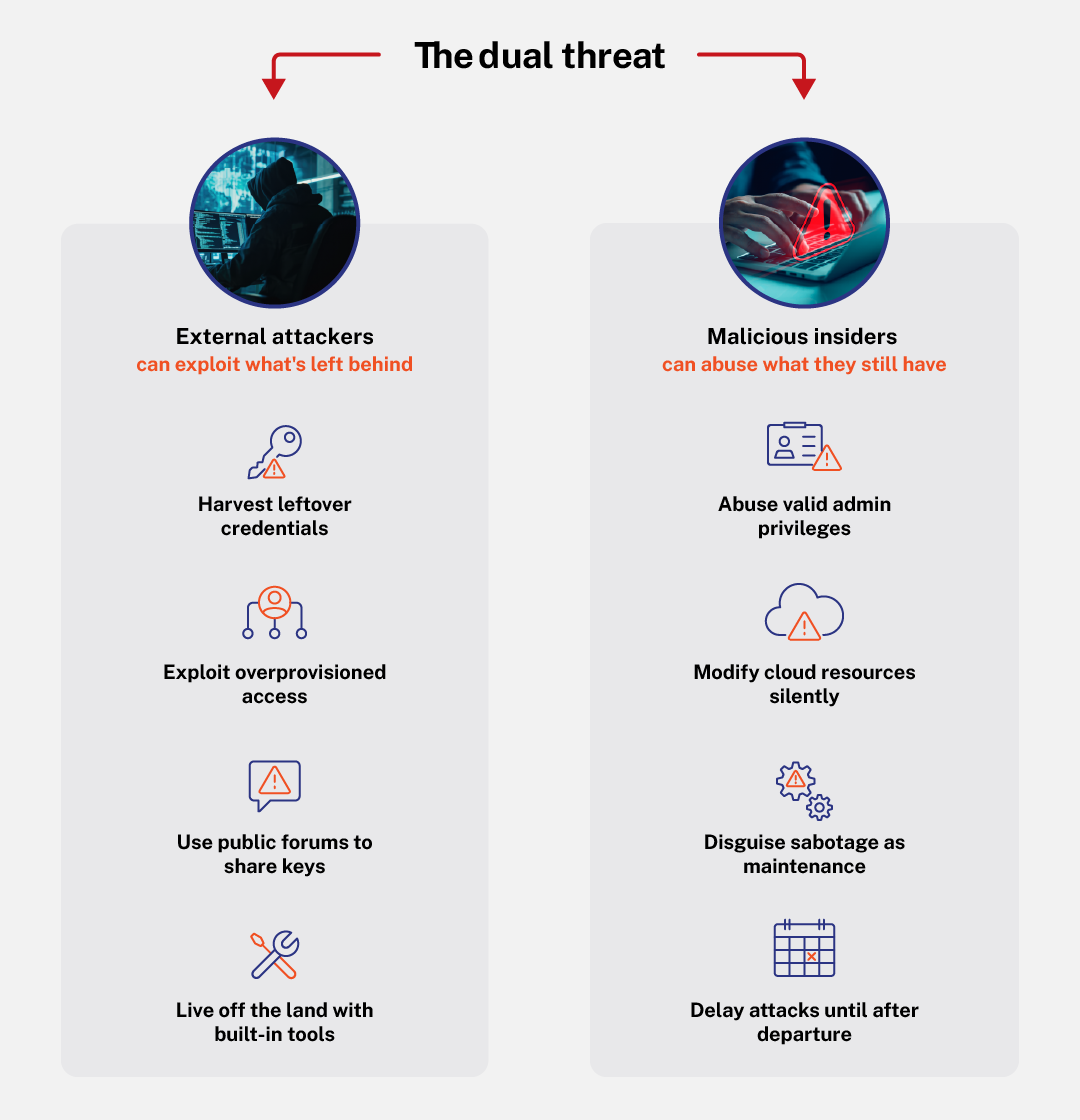
These scenarios and the dual threat they represent highlight a deeper issue: most cloud security tools don’t detect this kind of subtle, persistent sabotage because they weren’t designed for it.
In the following episode of the “How to Hack a Cloud” series, we examine a real-world insider threat scenario: a storage administrator, facing termination, covertly modifies data retention policies to delete sensitive information weeks after departure. It’s a stark reminder that malicious intent can weaponize legitimate access. The video highlights how enforcing ZSP can prevent such attacks—ensuring access is provisioned only when needed, and revoked before it can be misused.
Why legacy cloud security tools fail against modern threats
Most organizations still rely on legacy controls not built for this nuanced attack surface. They were built for a world with fewer cloud accounts, fewer apps, and fewer threats.
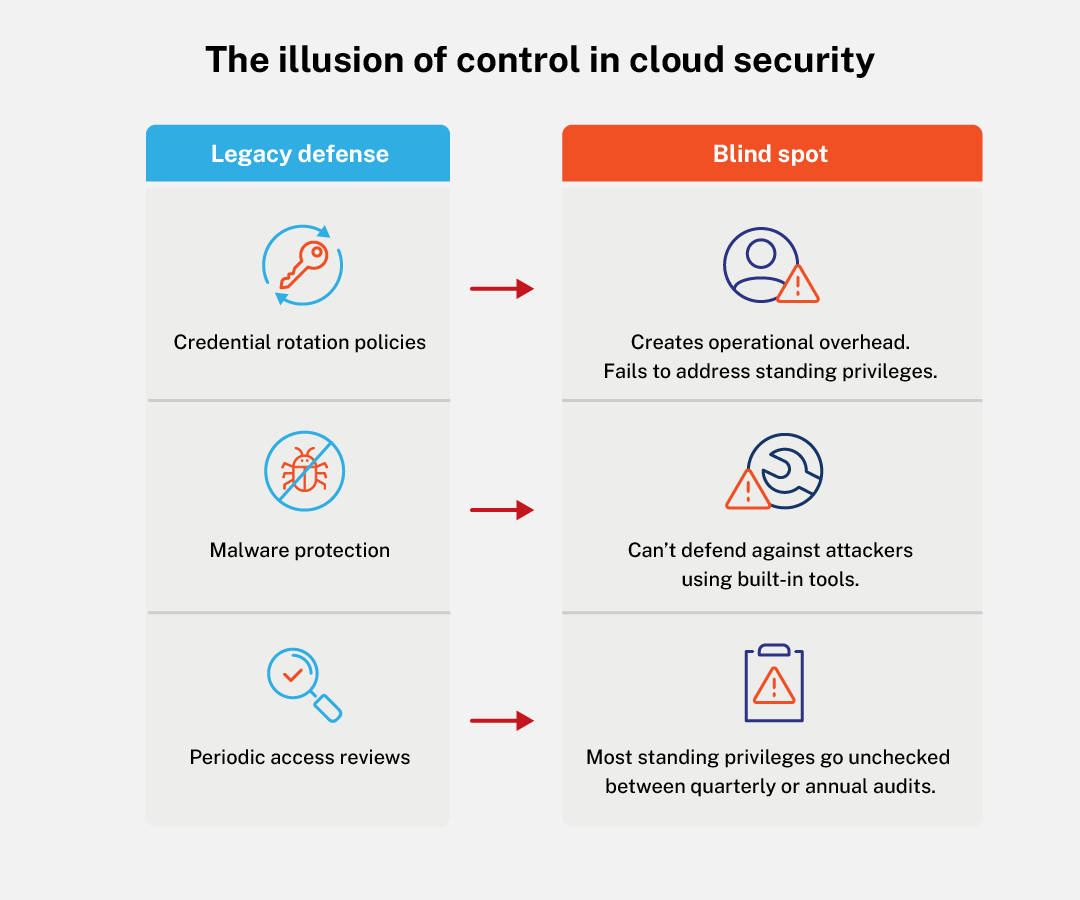
So what can organizations do?
Rather than granting long-term credentials or permanent administrative access that attackers (or insiders) can exploit, ZSP enforces ephemeral, policy-driven, just-in-time (JIT) permissions. The control of time, entitlements, and approvals (TEA) creates significant barriers for both internal and external threats. It’s the difference between “Here’s the spare key” and “Here’s a one-time code that disappears in an hour.”

With ZSP in place:
- Access expires automatically after a defined session, reducing long-term exposure and shrinking the attack surface.
- High-risk roles require approvals even if requested from familiar tools like Slack or Teams.
- Credential theft becomes far less effective since temporary tokens expire before attackers can weaponize them.
- Insider threats face tighter windows of opportunity, as time-bound, just-in-time privileges replace persistent admin access.
- Audit trails and policy enforcement are built in, simplifying compliance and regulatory reporting.
- Operational overhead drops with automated access orchestration across major cloud service providers.
- Developers and admins use their preferred tools, including CLI and cloud consoles—no extra portals, no added friction.
How zero standing privileges can help prevent cloud breaches
We’ve walked through the risks. Now explore the real-world solutions in action.
Check out our “How to Hack a Cloud” video series to see how missteps turn into breaches—and how identity-first defenses can help stop them. See how ZSP can help limit exposure, support accountability, and improve defender visibility and control.
Brooke Jameson is a senior product marketing manager at CyberArk.























