
The definition of privilege is changing, and this changes everything.
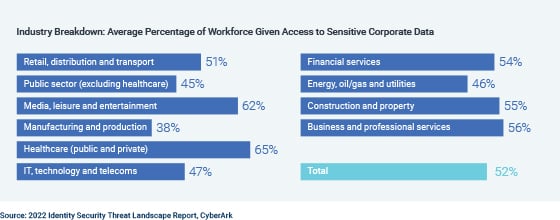
Identities of all types — not just IT team members, but any employees — are gaining access to sensitive data, infrastructure and systems that today’s attackers can easily exploit. On average, more than 1,500 IT and security decision-makers say over half of their employees have access to sensitive corporate data.
Managing digital identities — from granting, adjusting and revoking authorizations to complying with audits — is essential. But it’s not easy. The number of identities requiring your protection is surging, as your organization’s digital and cloud initiatives grow in scope and scale.
Meanwhile, you’re under pressure to manage and protect your identities at a time when:
- Many enterprises are bogged down with time-consuming manual processes, outdated technologies and silos across apps, directory stores and data repositories.
- As risks increase, so do workloads, hours and stress levels. Meanwhile, economic pressures exacerbate ongoing resource and skills gaps.
To truly enforce least privilege, IT and security teams need controls that cover all types of identities with powerful access — from the IT admins of the world to workforce users with heightened privileges. This means enterprises need to rethink what Identity Management is, and needs to be, from its purpose to its execution.
Securing Identities for the Entire Lifecycle Using Automation and Orchestration
As you know, enforcing least privilege involves not just limiting access overall, but giving users the minimum level of authorizations needed to perform only job-relevant actions – for example in SaaS applications where a risky action could compromise sensitive data.
The problem is that manual, error-prone processes can hinder many organizations from securely managing employees’ identity lifecycles.
Looking at the beginning of the lifecycle, new employees often wait days or weeks to be provisioned with access to the applications, services and IT systems they need. At some point, impatience may encourage workers seek other ways to gain access, including the adoption of shadow IT.
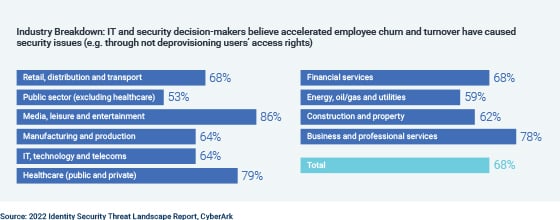
But consider what could happen if an IT or security team member forgets a critical step in a manually executed workflow. For example, if an employee leaves the company, the IT team may need to run through a checklist of applications where they must remove access one at a time by hand.
What’s the risk?
One missed step leaves the door open for threat actors to exploit misprovisioned, overprivileged or orphaned accounts — and attackers do this routinely.
Employees’ start and end dates, while important, are only the bookends for continuous identity lifecycle management. Ensuring least privilege for employees across their entire tenures at your organization requires:
- Months, years and even decades of tracking and re-assigning privileges per user.
- Provisioning and deprovisioning access as job roles and systems change — and as applications grow in number.
- Ensuring the wide range of target applications involved remain in sync.
In an era when privilege is everywhere — including in employees’ ability to take risky actions in business apps containing sensitive data — these Identity Management mainstays call for a new approach.
The reason: most enterprises are stuck in a pattern of manually connecting the dots and scripting integrations between data, applications, events and services. And many companies lack formal procedures or consistent workflows for reassessing, adjusting or revoking users’ access and privileges.
Here are some steps you can take to bring a security-first approach to managing identities from a user’s start date to their last day:
1. Centralize your lifecycle management policies, controls and capabilities, using automated workflows for:
- Onboarding and offboarding employees.
- Defining and enforcing each user’s unique roles, responsibilities, access rights and permissions.
This approach can free your team from repetitive, error-prone tasks. Integrating these processes with your trusted HR software enables you to maintain consistency and accuracy between platforms.
2. Federate identities across cloud and on-premises applications and systems, so your team can:
- Quickly provide access when users need it.
- Adjust it when roles or risks evolve.
- Remove it when users leave the enterprise.
Automated workflows can help you prevent privilege creep and orphaned accounts that attackers often exploit to launch attacks, steal data and more.
3. Gain real-time insight into potential risks — and the ability to act on them — based on automated tools that track areas such as:
- Application usage.
- Failed login attempts.
- Unused accounts.
- External threat data.
This three-part approach gives you a scalable form of visibility and control through automated workflows designed to prevent risky actions by users and breach attempts.
Next Steps: Best Practices for Ensuring Compliance and Extending Privilege Controls to All Identities
In a new Executive POV piece published by CyberArk, I discuss best practices for bolstering your team’s Identity Management capabilities in two additional areas:
- Applying a security-first approach to compliance, from managing access-related reviews and certifications to meeting regulators’ auditing requirements
- Extending the controls you use for securing privileged users to all identities – for example, protecting employee passwords with vault storage and secure sharing
You can read the full piece here: Reinforce Least Privilege by Rethinking Identity Management
Gil Rapaport is the general manager for Identity and Access at CyberArk






















