
This article is part of a series of blog posts on cryptomining from the CyberArk Red Team. It explores the evolution of cryptocurrency – from the birth of Bitcoin and the utility of blockchain to the rise of Monero and the hacker economy – and what organizations need to know about the connection between cryptocurrency and cyber security.
For an in-depth look at the technology behind Monero, download the Red Team report, “Behind the Hidden Conversion of Electricity to Money: An In-Depth Analysis of XMR Cryptominer Malware.”
The Birth of Bitcoin
In the aftermath of the 2008 financial crisis, an anonymous programmer calling himself Satoshi Nakamoto authored the first truly decentralized cryptographic – or cryptocurrency, which he called Bitcoin. His creation combined the concepts of decentralized peer-to-peer networking, which had been perfected over the prior decade through file sharing and torrenting networks (such as Napster, Limewire and Pirate Bay) along with elliptic curve cryptography to create a revolutionary new technology we now call blockchain.
Blockchain is an ingenious mechanism that was the first to solve the problem of “double spending.” In essence, the key difficulty in creating a decentralized ledger such as the one Bitcoin uses, is that the entire network must be in agreement about who owns which Bitcoins at any given time.
Nakamoto split this hypothetical ledger into millions of “blocks” and linked these blocks together with the one-way cryptographic hashes to ensure that past transactions in its distributed ledger were tamper resistant. Keep in mind that a block is simply a fragment of the total Bitcoin ledger, and this block must be linked to every other block in the history of the Bitcoin network in order to be accepted as genuine.
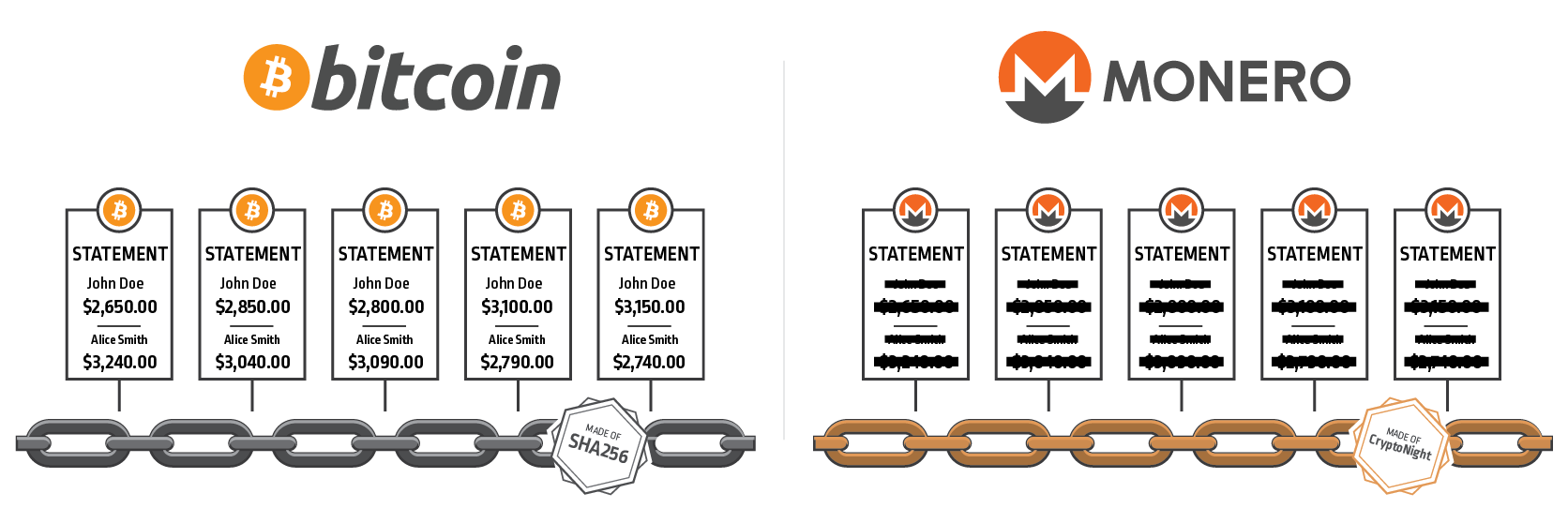
You can imagine the blockchain as millions of paper bank statements “chained” together with invisible cryptographic chains, and new sheets of paper are constantly added as new people spend money.
Innovation, Invention and the Hacker Economy
The real genius of Bitcoin is in the way it took concepts from physical gold mining and combined them with cryptography to create a virtual “mining” system. The system ensured a limited supply of Bitcoins, which required a set amount of effort/resources to acquire, much in the same way that there is a limited amount of gold on earth, the extraction of which requires the input of effort and resources.
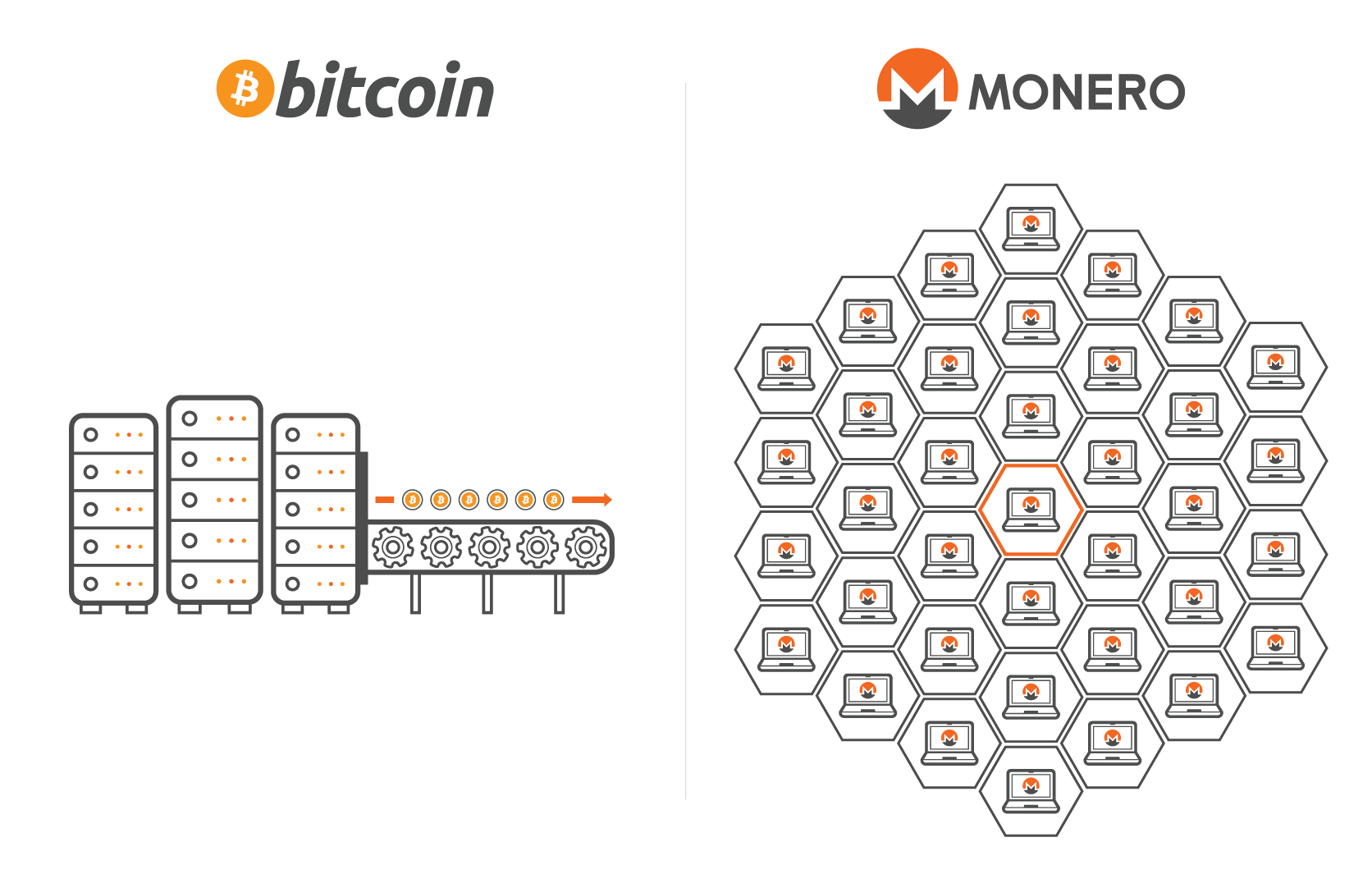
However, while Bitcoin kick-started the cryptocurrency era and flourished on the dark web, it lagged in innovation. Thousands of cryptocurrencies have expanded on the concepts behind Bitcoin – including Monero, which has evolved as the currency of choice for many – namely hackers. That’s partly because it offers sophisticated anonymity features, and perhaps most notably, an ASIC-resistant (Application Specific Integrated Circuit) proof-of-work (PoW) algorithm.

Nakamoto’s original vision for Bitcoin was for the process of “mining” to be as egalitarian and decentralized as possible, ideally a “one CPU one vote” type of system to ensure the integrity of the blockchain remained intact while still keeping it as decentralized as possible.
With a current Bitcoin price of about $6,373 as of 7/10/2018 and a reward of 12.5 Bitcoin for whichever miner succeeds in forging the next chain before anyone else, the financial incentives to win this race are significant. This competition has resulted in the rise of ASIC devices, which are essentially small, specialized computers whose sole purpose is to mine Bitcoin.
The rise of these devices has made it nearly impossible for the average individual to contribute to the mining process of Bitcoin, thus putting a large amount of power into a small, centralized group of individuals who control massive mining operations. The implications should not be overlooked. This small group of people now have the ability to essentially dictate which transaction records will be added to the blockchain and which will not.
Monero: The Successor to Bitcoin?
Monero is an innovative and principled “privacy coin” – a cryptocurrency that boasts anonymity of its users and transactions as one of its primary goals/features. It has gained widespread adoption in recent years, both among legitimate businesses and hackers. In fact, it is on its way to (and already has in many respects) replaced Bitcoin among the original demographic of users who first adopted Bitcoin on the dark web.
In our exploration of the concepts behind Bitcoin and blockchain, Monero should be thought of as Bitcoin – with two key differences:
- On each of the public bank statement papers (all chained together), the names of the sender, receiver and amount being transferred are redacted.
- The chains used to link each of these papers together are made out of a different type of metal.
Monero is one of the only existing cryptocurrencies that is truly fungible. This inherent interchangeability is achieved by Monero’s requirement that all transactions on its network be anonymous by default (as opposed to other privacy coins such as ZCash, where anonymity is an optional feature).
These characteristics of anonymity and fungibility make Monero an absolutely perfect cryptocurrency for dark web markets, where the public nature of Bitcoin proved to be highly damaging to several of the individuals behind Silk Road. With Monero, individuals buying or selling illegal goods and/or services don’t need to worry about their funds being blacklisted and devalued. They can know with confidence that any unit of Monero is interchangeable, and that it can be spent with both legitimate and illegal businesses.
That said, the most significant attraction of Monero for malicious cryptominers is the algorithm Monero uses to implement its PoW blockchain system. This algorithm is called CryptoNight, and it has some unique qualities making it perfect for malicious cryptomining.
Over the past year, a wave of innovative new Monero mining botnet malware began to surface, achieving anonymous profits of hundreds of thousands to millions of dollars, culminating in one of the latest commercial botnet malware families netting approximately $7 million in 6 months.
As noted in a recent Fortinet post,“According to a Coinhive FAQ, they (the malware writers) chose Monero (XMR) because the algorithm used to compute the hashes is heavy, but better suitable to CPU limits, especially when compared to other cryptocurrencies where using GPUs (graphical processing units) would make a big huge difference. They mentioned that the benefit of using a GPU for Monero is about 2x, where it’s 10,000x for BitCoin/Ethereum.” With this attribute, in conjunction with the anonymity and tremendous potential profits involved in illicit Monero mining, is it any wonder malware authors are flocking to it in droves, abandoning old methods of botnet monetization such as ransomware, spam or credit card theft?
Essentially, the Monero blockchain can be thought of in the same way as the Bitcoin blockchain, with the fundamental difference that the invisible chains between the blocks are made out of a different material. In Bitcoin, these chains are forged from a cryptographic algorithm called “SHA256,” which is easily manufactured by specialized ASIC devices, whereas in Monero the chains are made of “CryptoNight,” a metal that can only be worked with by hand, and thus super factories cannot mass produce it.
Cryptomining and the Evolving Threat Landscape
The rise of ASIC-resistant cryptocurrencies is creating a huge demand for access to the computing power of the average workstation computer. Throughout 2017, the malware threat landscape began to undergo a significant shift away from cyber crime monetization tactics such as ransomware and credit card theft and toward a new breed of malware called cryptominers. Moving into 2018, malicious cryptominers are increasingly prolific and have already been the cause of several multi-million dollar heists through the use of Monero.
The ability to easily convert electricity and access to computer hardware into money is something new in the world of cyber crime. It significantly lowers the bar to entry for less skilled attackers and creates a brand new set of problems for defenders to solve. In stark contrast to ransomware, malicious cryptominers can run silently in the background without any user interaction indefinitely. Furthermore, the incentive for the attackers shifts decisively towards making their malware as silent and low-impact as possible, so as to maximize the duration of their mining operations on compromised systems for maximum profit.
The Monero cryptocurrency and the technology behind it are likely to become ubiquitous features of the malicious threat landscape in years to come and will create new challenges for security vendors attempting to secure endpoints and organizations against this stealthy threat.
For a deeper dive into the technology behind Monero, download the CyberArk Red Team report, “Behind the Hidden Conversion of Electricity to Money: An In-Depth Analysis of XMR Cryptominer Malware.”
























