
Why We Need Identity Security That Moves with Our Workforce
Imagine a typical morning at an enterprise: employees, remote workers, contractors and partners log in, browsing and accessing apps and files they need to do their jobs. All seems calm.
But behind the scenes, security teams face a different reality. They’re managing an explosion of high-risk identities and passwords across countless endpoints, dealing with unchecked admin rights, rising security costs and compliance pressures. They rely on critical first lines of defense like multi-factor authentication (MFA) and single sign-on (SSO).
But when stolen credentials are up for sale on the dark web for less than a cup of coffee, hackers don’t need to hack. They can log in as any one of us and navigate our enterprise networks undetected. This ushers in troubling post-authentication threats like session hijacking, data theft, cookie manipulation and other threats that can be leveraged at scale using AI. Given these post-authentication threats, there is an urgent need for second, third and fourth lines of defense. We need security that doesn’t introduce new solutions or overburden security teams.

Expanding Attack Surfaces Demand New Solutions
As remote work, SaaS applications and partner networks grow, so does our collective attack surface. Almost half of all breaches involve data across multiple environments. Security teams now manage thousands of accounts and entitlements across both managed and unmanaged endpoints. Issues like shared accounts, poor password management and unchecked admin rights make organizations vulnerable to ransomware, malware and data breaches. Add in temporary or external workers, and the burden grows. IT teams are inundated with tickets for onboarding, offboarding, lost passwords, locked-out users and misplaced authentication devices.
The scale is massive—organizations experience a cyberattack every 39 seconds and it takes an average of 270 days to detect and contain these attacks. Even organizations that have adopted identity-first security models often rely on disconnected solutions that don’t fully integrate and leave them with blind spots in user activity. Many still depend on spreadsheets to track passwords—a risky, outdated approach.
We need a modern approach to identity security that understands that every user can be privileged. We need intelligent privilege controls that cover the full lifecycle: onboarding, role changes, de-provisioning and beyond. Most importantly, we need controls that don’t frustrate workers or slow them down. From powering up their workstation to closing the last tab, the experience should be seamless.
Workforce Identity Security in Action
Now, imagine this same morning at work with a unified approach to security. An employee logs in from a remote location with a single set of credentials that unlocks everything they need. No more juggling multiple logins or trying to remember yet another password. Every user, whether they are in-house or remote, a contractor or a partner, has a single set of credentials that unlocks everything they need. No more juggling multiple logins or trying to remember yet another password. With SSO, users sign into a single portal with existing credentials, accessing all assigned apps in one click. They can update profiles and rest passwords as needed—all without compromising security.
Next, when they shift to web browsing, they have a choice of passwordless authentication methods. Since not all apps or sessions are the same, high-risk web sessions are secured with web session monitoring, recording and controls that catch anything out of the ordinary in real time, giving security teams insight into user actions, protecting sensitive data and creating a detailed audit trail that will come in very handy for compliance and response.
To balance access and security on unmanaged devices, external partners and vendors have a safe pathway with secure, controlled browsing that protects users from session hijacking and cookie theft without disrupting workflows. Strong endpoint identity security controls provide comprehensive visibility into attack paths, credential misuse and insider threats while seamlessly integrating with third-party solutions.
No matter where a worker is in their journey—joiner, mover or leaver—organizations need automated provisioning and de-provisioning of access, certification and governance to prevent bottlenecks. Centralized storage and management of identities and attributes should serve as the single source of truth for all identity data.
Building a Unified, End-to-End Defense that Scales with Threats
CyberArk Workforce Identity Security makes this vision a reality. By unifying MFA, SSO, lifecycle management and endpoint security with browser, session and password protection, we deliver a bold, comprehensive approach that safeguards every user, from endpoint to cloud and back. By breaking down silos and using controls similar to privileged access management (PAM), we enable seamless access across applications and resources for all users—without multiple logins or cumbersome authentication steps. This approach provides scalable, flexible protection that evolves with your business, freeing internal teams from the constant cycle of manually managing access privileges.
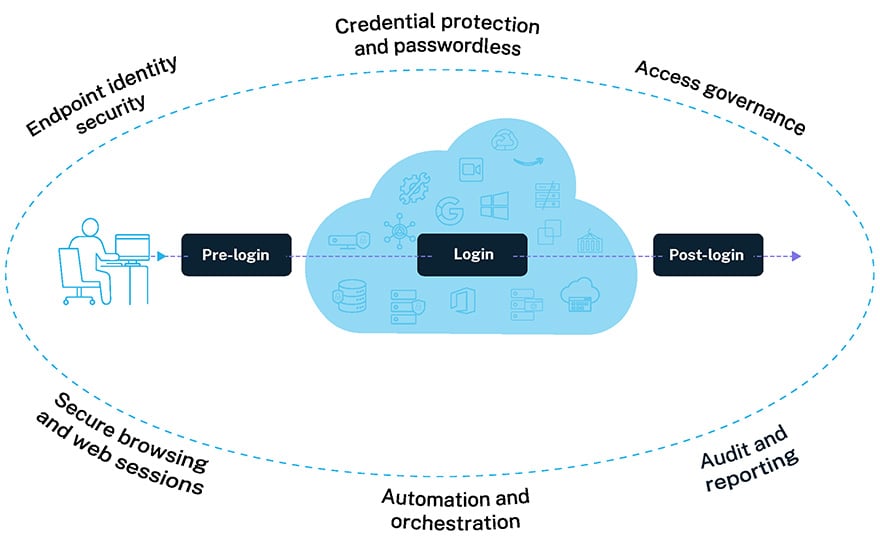
Effective identity security protections follow workforce users through their entire digital journey.
With intelligent privilege controls, we help extend Zero Trust principles to the endpoint, remove admin rights, enforce least privilege and defend against unknown attacks and ransomware. Using AI and real time threat detection, automated workflows and adaptive authentication and monitoring, we help ensure your workforce is secure from the first login to the last touchpoint. And, if your organization is facing strict audit and compliance standards, peace of mind is possible. With CyberArk, I’ve seen our customers transform operations. They’ve shifted from chaos to a:
- User-friendly experience that enables users to log in easily without disruptive prompts or clunky resets, enhancing compliance and minimizing frustration.
- Unified and layered defense that integrates traditional IAM tools, password management and web session controls to cover every touchpoint along the entire user journey.
- Continuous, adaptive security that scales to meet evolving risks, applying intelligent privilege controls to every endpoint for complete, risk-based protection that doesn’t disrupt the way people work.
When our credentials can be sold to the lowest bidder, the stakes are sky-high. The good news is, I’ve witnessed organizations that were once overwhelmed by sprawling endpoints, unsecured credentials and legacy systems—reshape their security postures. They shifted from fragmented identity and access management (IAM) processes to a cohesive identity security framework that’s required to navigate today’s complex threat landscape.
Security can’t stop at the login; we need a holistic, unified defense-in-depth strategy that can keep pace with today’s complex threats. A new, reimagined approach to workforce identity security starts not with sophisticated security solutions but with a security-first mindset. One that is focused on identities, functions in layers and is flexible enough to secure the complete user journey.
Dive into the workings of workforce identity security in our whitepaper, “What’s Your Login Worth? Less Than a Latte.”
Archit Lohokare is the general manager of Workforce Solutions at CyberArk.























