
In 2019, I founded and served as the CEO of a cloud security company (C3M), a journey that eventually led to our acquisition by CyberArk in 2022. Back then, the cloud security scene was budding, filled with migration buzz and a shifting urgency around securing the cloud. Acronyms like CSPM (cloud security posture management) were emerging, and enterprise security leaders grappled with where to begin.
Jump to 2023, and cloud security has transformed. And those then-burgeoning acronyms are now part of our security vocabulary; CSPM is now the vital CNAPP (cloud-native application protection platforms). In this space, Cloud Identity and Entitlement Management (CIEM) steps up, fixing identity misconfigurations and taming permissions.
Yet, a clear pattern emerges in conversations with leaders from some of the world’s largest organizations. While detection platforms provide excellent insights into their cloud posture, addressing the identified issues isn’t straightforward. In fact, most security teams struggle to take the right risk-reduction measures for their environments. Effective cloud security goes beyond fixing configurations or permissions; it’s fundamentally about controlling “access” to your cloud—your consoles, data and infrastructure.
CyberArk’s Insight to Action framework helps address this gap between detection and remediation and offers a deep dive into six pivotal areas recognized as substantial threats in the cloud environment. Addressing these challenges provides a secure cloud experience and ensures smooth operations, eliminating potential loopholes and vulnerabilities.
The Insight to Action framework builds on CyberArk’s history of risk-focused best practices and identity security framework, the CyberArk Blueprint for Identity Security Success. Enterprises can achieve a proactive and resilient identity security posture by focusing on six “insights” across major cloud platforms like AWS, GCP and Azure.
In my previous blog, “Operationalizing Identity Security in the Public Cloud,” I discussed the significance of a comprehensive framework that transforms risk insights into actionable remediation measures. Taking it a step further, I’m now excited to share the following critical insights that can significantly help your organization reduce risk in the cloud.
Six Insights to Drive Actions to Reduce Cloud Risk
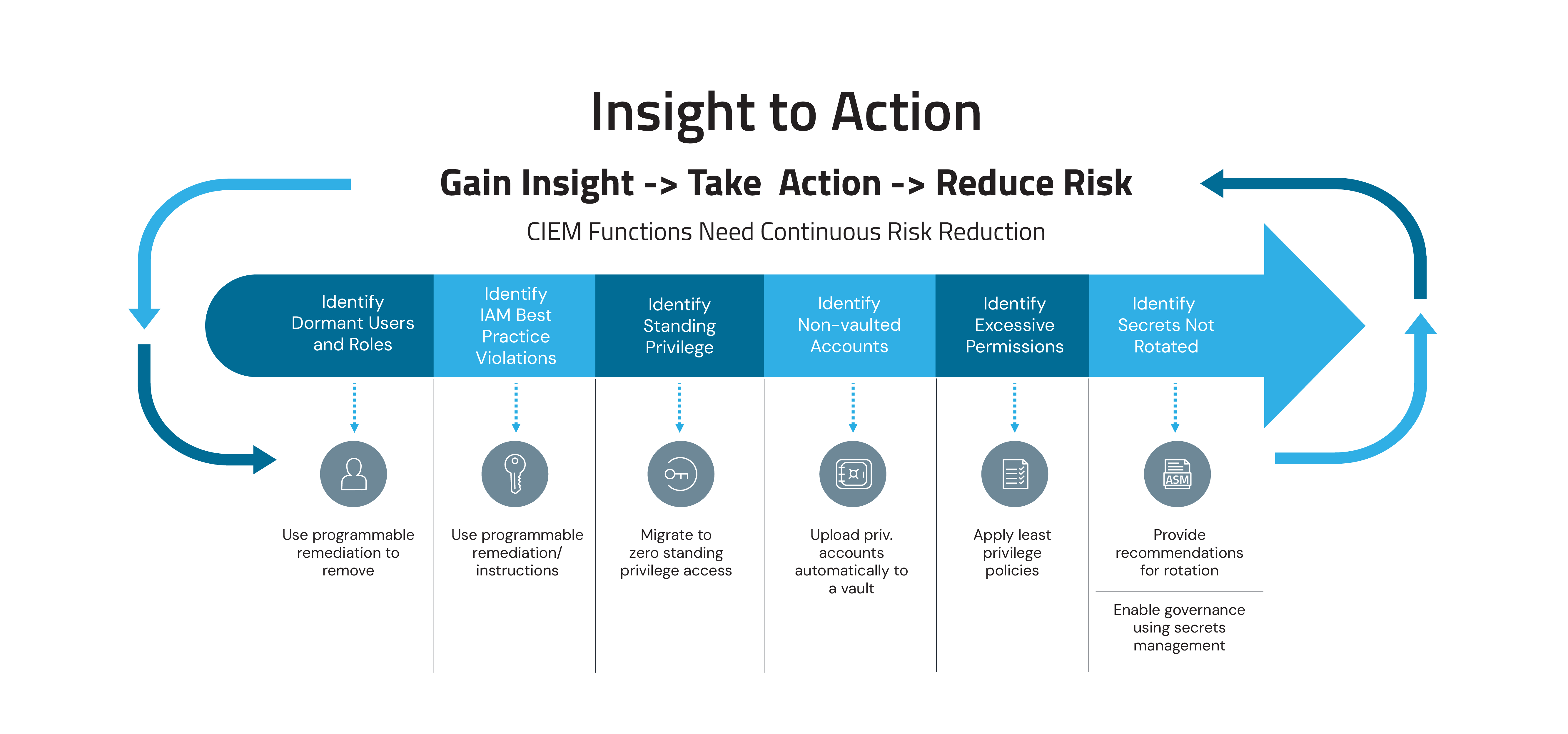
Insight 1: Dormant Users in the Cloud – The Hidden Threat
Dormant users or inactive accounts with retained access privileges pose a significant risk. They often go unnoticed in expansive cloud environments, offering backdoor entries for malicious actors. To mitigate this threat, you can:
- Use automation to revoke access or deactivate accounts after a certain period of inactivity. Removing the dormant account eliminates the risk associated with that account being exploited. Fewer inactive accounts mean fewer entry points for attackers.
- Audit user activity regularly. Implement monitoring tools to identify and report on accounts with prolonged inactivity.
- Conduct frequent access reviews of user roles, permissions and activity to ensure only necessary and active accounts exist. Keeping only necessary and active accounts helps maintain compliance with many regulatory frameworks that require minimization of access.
- Set up alerts for any activity on dormant accounts. Any sudden activity should be treated as suspicious.
Insight 2: Misconfigurations – The Identity Blindspot
Misconfigurations in a cloud environment refer to incorrectly set up assets or services that can expose an organization to risks of varying levels. With the complexity of modern cloud architectures, configuration settings can number in the thousands. Each setting provides a potential opportunity for error. Amid thousands of settings, a few incorrect ones can easily go unnoticed.
To address this threat, here are some steps you can take:
- Review and audit cloud configurations frequently to align with industry best practices.
- Review IAM policies regularly to ensure the principle of least privilege.
- Enforce multi-factor authentication (MFA) for all users.
- Implement a just-in-time (JIT) access model, removing standing permissions and aligning to zero standing privilege (ZSP). This one step alone can drastically reduce your risk surface by ensuring that access is given to the right people at the right time – no more and no less.
- Deploy automated scanners. Integrate advanced tools designed to scan for IAM misconfigurations systematically. This proactive approach enables a comprehensive understanding of the identities present in the cloud (and their configurations) and identifies potential discrepancies.
In the event of misconfigurations, automated scanners alone can pinpoint issues and provide actionable insights on rectifying them, ensuring a swift and effective resolution.
Insight 3: Persistent Access to the Cloud – The Overlooked Backdoor
Persistent access means that if an attacker compromises an account, they have indefinite access until detected. This extended time frame allows malicious entities to establish a stronger foothold, conduct reconnaissance, and even spread to other parts of the network.
To mitigate this threat, you can:
- Shift to JIT access, providing temporary access that auto-revokes after a certain period or post-task completion. This reduces the time window in which credentials can be misused.
- Conduct frequent access rights reviews to ensure that users have only the permissions necessary for their roles and that any excess permissions are promptly revoked.
- Enforce MFA for all users, especially those with elevated privileges. This adds an additional layer of security, ensuring that even if credentials are compromised, attackers have a harder time gaining access.
- Adopt a ZSP model. Transition away from standing privileges where users have continuous elevated access. In a ZSP model, all privileges are revoked by default and users request elevation only when needed.
In the case of ZSP, it’s an approach gaining traction because it limits the time window for potential abuse of elevated privileges. This ensures users get only the access they need and only for as long as they need it. Coupling ZSP with JIT further reduces the exposure window, making it a powerful combination against potential threats.
Insight 4: Excessive Permissions – A Gate Wide Open
Excessive permissions in the cloud provide users, and potentially attackers, more access than required to perform their tasks, turning even a minor breach into a potential catastrophe. Excessive permissions in the cloud can lead to data leaks, privilege escalation and operational risks.
To address this threat, you’ll want to:
- Assign permissions based on organizational roles (aka role-based access control (RBAC)). Ensure that each role has only the permissions necessary to perform its tasks.
- Automate permission assignments. Use tools that automatically assign and adjust permissions based on roles, tasks and workflows.
- Adhere to the principle of least privilege (PoLP). Always provide the minimum necessary access. Regularly review and adjust permissions, ensuring they align with users’ current roles and tasks.
- Switch to a JIT access model. Instead of permanent high-level permissions, provide temporary access for specific tasks. Once the task is done, permissions revert to their normal levels. This great risk reduction measure buys you time to study and refine the permissions.
- Continuously monitor user activities and employ AI or machine learning-based tools to detect and alert anomalous behaviors.
- Implement permission boundaries. Set hard limits on what permissions can be granted, ensuring that even administrators cannot inadvertently grant excessive rights.
Insight 5: Unrotated Secrets – A Ticking Time Bomb
In the world of multi-cloud architecture secrets — be it API keys, tokens, public/private key pairs or passwords — act as vital access conduits to crucial data and services. AWS, GCP and Azure, three cloud giants, all offer their versions of secret management services. However, if these secrets remain static, the risk factor compounds. The threat is akin to leaving a backdoor unlocked indefinitely; it’s just a matter of time before someone or something exploits it.
Proactively managing these secrets across all cloud platforms is not a mere best practice — it’s a necessity.
To mitigate this threat, you can:
- Implement a mandatory policy to rotate secrets at regular intervals. The frequency might vary based on the sensitivity of the secret.
- Automate secrets rotation. Use cloud-native tools or third-party solutions to reduce manual errors. In multi-cloud environments, establishing a centralized management system for all secrets and enforcing consistent controls is crucial for maintaining robust security practices.
- Revoke and replace secrets instantly. Ensure you have mechanisms in place to do this in the case of suspected breaches.
Insight 6: Non-Vaulted Admin Accounts – The Exposed Crown Jewels
Admin accounts are the crown jewels of any IT infrastructure, granting privileged access to the heart of systems and data. In the realms of AWS, GCP and Azure, these accounts, when not vaulted, can be likened to leaving the keys to the kingdom unguarded. As businesses expand their cloud presence, securely managing these accounts, with their elevated permissions, is essential.
To mitigate this risk, you can:
- Implement and enforce MFA for all admin accounts. This ensures an extra layer of security even if credentials are somehow compromised.
- Audit and review access logs and trails across AWS, GCP and Azure. And do so regularly. This helps in the early detection of any anomalies or unauthorized access attempts.
- Create a mechanism and process to detect and vault new admins (and make sure to separate federated from local admins with actual credentials).
- Set up a solution for secure access using these sensitive secrets without exposing them to end users while keeping a full audit of all activity.
Taking Cloud Security Action
Where the Insight to Action framework is organized around substantial threats to your cloud environments, the CyberArk Blueprint is organized around target personas and privileges grouped into security control families. Every organization has unique prioritization needs and a different existing risk posture. By leveraging the CyberArk Blueprint for CIPS and the Insight to Action framework together, your organization can develop a tailor-made strategy and approach to securing your multi-cloud environments.
Stay tuned! The evolving cloud landscape promises more insights and innovations. We are excited to guide you through them in upcoming blogs.
Paddy Viswanathan is vice president of Cloud Solution Strategy at CyberArk.























