
As enterprises increasingly migrate to the public cloud, identity and access management (IAM) inconsistencies across different cloud providers pose a significant hurdle. Effectively securing identities in this complex landscape has proven to be a challenge. Discussions with industry analysts and enterprise clients have highlighted a prevalent issue: the existing security tool suite often falls short in providing actionable measures to weave identity security into cloud operations.
Many enterprises use native cloud provider tools, third-party security solutions and custom-built strategies to meet their cloud security needs. However, most of these approaches are reactive, offering band-aid fixes rather than robust, scalable solutions. The challenge then lies in devising a sustainable identity strategy for the cloud environment and operationalizing it effectively.
From Concept to Execution: Operationalizing Cloud Identity Security
The CyberArk Cloud Security framework offers a systematic and phased approach to streamline identity security operations within the cloud. It converts the broader concept of “IAM in the public cloud” into a solid, ROI-focused initiative. And we begin with the right set of identity security capabilities, such as risk-based access controls, entitlements risk and visibility, identity automation and orchestration, secrets management and audit and compliance – all supported by the enforcement of cloud best practices.
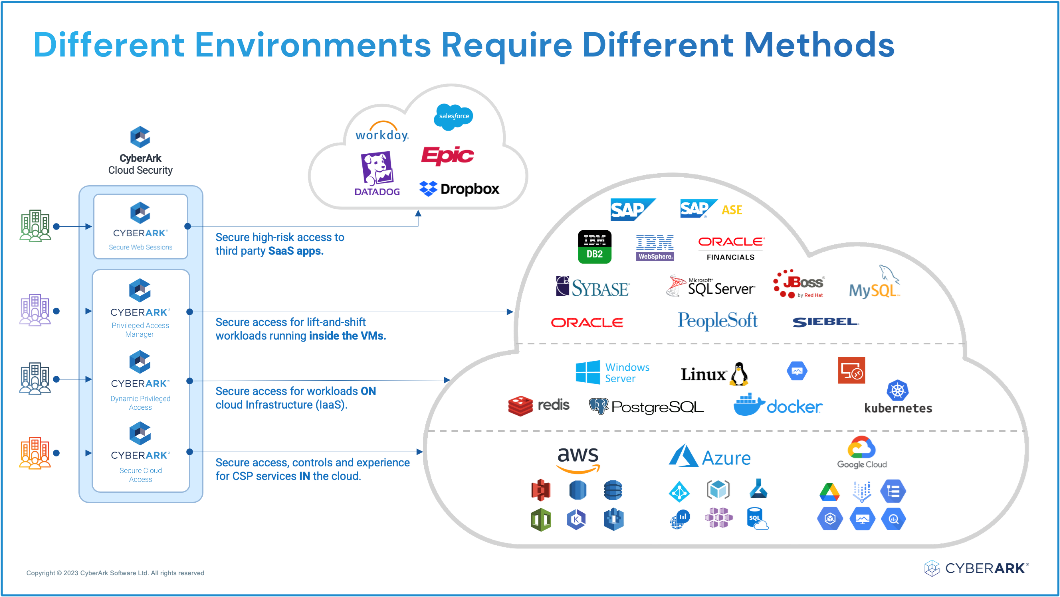
Prioritizing and Implementing the Proper Controls
Cloud identity and its associated challenges are constantly evolving, given the continuous innovation from cloud providers. At last count, there are over 1,400 native services spread across AWS, GCP and Azure, bringing in more than 40,000 entitlements and controls – and it’s an ever-growing list.
Standardizing roles or entitlements in this constantly changing environment becomes extremely challenging. This dynamic landscape often leaves IAM teams juggling multiple priorities. The initial focus is often on “discovery” and “right-sizing entitlements,” which fall within the domain of CIEM (Cloud Infrastructure Entitlements Management). While insightful, identifying and removing unused entitlements linked to cloud resources can be complex, particularly when unused permissions are tied to specific cloud project roles or identities.
As a result, resolving these issues necessitates a dialogue with the application teams, proof of non-utilization and a timeline for resolution. This can be lengthy, raising the question: while entitlement visibility and right-sizing is important, is it the first control to prioritize?
Meanwhile, during these debates about appropriate entitlements, standing access and associated risk persist in your cloud environments. Developers and apps often enjoy unrestrained, always-on access to your cloud environments. Especially in the case of lift-and-shift applications, developers often have standing access to the underlying compute workloads powering their applications. All these scenarios present a significant risk if these identities are compromised.
The Three Steps to Operationalizing Identity Security
To tackle this risk and streamline identity security operations, consider the following key steps:
1. Transition to a zero standing privilege model and eliminate standing access.
The road to least privilege is long and windy and comes with many operational challenges. To reduce your attack surface immediately, begin by transitioning all your privileged and non-privileged standing access to a just-in-time (JIT) based zero standing privilege (ZSP) model. The challenge lies in identifying your riskiest identities – admins, shadow admins, identities with sensitive privileges, identities with misconfigurations – and seamlessly shifting them to a JIT model.
CyberArk Cloud Security offers comprehensive visibility into your entire cloud identity estate’s risk and compliance posture. It enables the automatic and seamless migration of risky identities – or all cloud access – to a centralized platform: CyberArk Secure Cloud Access. By consolidating access policies, you can effectively manage and regulate access to resources across various cloud platforms, enhancing security and reducing complexity.
You can also stop the bleeding for new environments by utilizing a ZSP model when setting up new cloud environments, which ensures they start with a clean slate and no standing access. This can allow organizations to stop the bleeding of standing privileges. Nobody prefers revisiting and fixing issues.
Moving to a ZSP model significantly reduces your cloud risk surface, helps you demonstrate ROI via risk reduction to leadership, and helps you comply with cloud access control requirements stipulated by leading industry standards like NIST and SOC2.
2. Address non-human use cases and standardize audit and compliance.
Along with the immediate human access risks we’ve just addressed, there are, of course, non-human threats. Application and API access pose notable risks – and getting complete visibility into the non-human elements is a key measure.
Here are steps you can take to reduce significant risks:
- Initiate centralizing non-human access and develop a unified system for managing secrets to secure access to your cloud environments.
- Fix excessive and risky entitlements and identity issues across clouds. As you start addressing these issues, it’s essential to use a framework that helps you gain the right set of insights and take meaningful risk-reduction actions. Our Insight to Action framework in CyberArk Cloud Security was designed to help administrators do exactly that. The framework links risk insights to remediation recommendations that can be applied programmatically, through click-and-remediate solutions or automation.
- Ensure that integrations are set up with the common tools used by the cloud security teams, cloud admins and infrastructure engineers. Integrations to ITSM and ChatOps tooling help seamlessly integrate access approval workflows and notifications.
3. Adopt proactive measures and embrace automation.
You’ve tackled the major risk factors related to human and non-human access and understand identity security nuances across the clouds used by your organization. Now embrace automation to enforce industry standards for both types of access.
There are over 100 out-of-the-box best practice rules in CyberArk Cloud Security, so you can extend the rule framework and build identity security rules based on your cloud environments’ internal guidelines and guardrails. This enables you to initiate the automation of fixes for common and recurring identity issues in the cloud.
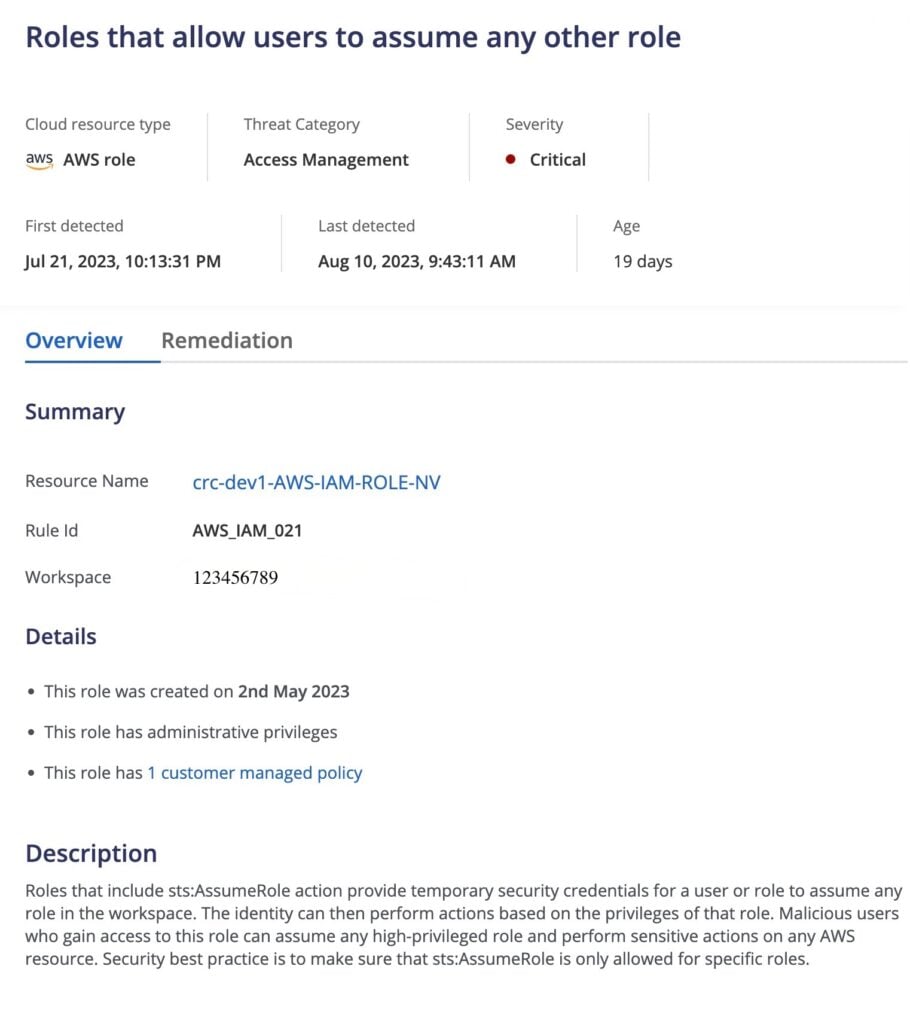
Again, nobody wants to go back and fix things. Ensure that new apps and cloud environments conform to the best practices you want to establish. Make it easy by automating these checks in the Infrastructure-as-Code (IaC) provisioning process.
The above steps will help you to standardize audit and compliance requirements and gain complete visibility to cloud identities (human and non-human) and secrets dispersed across different stores in the cloud.
Driving Value Through Standardized Cloud IAM Operations
Standardizing cloud IAM operations with CyberArk Cloud Security means establishing a consistent methodology for managing and enforcing best practices, securing access for humans and non-humans – and auditing and compliance across your cloud estate.
When effectively operationalized, a cloud identity security solution enhances your cybersecurity defenses, saves time, reduces risk and validates its cost by delivering rapid, measurable value. It’s a journey from abstract to concrete, making the intangible quantifiable in a robust and agile manner.
Read more about the various access cloud challenges in the CyberArk executive POV, “Why Cloud Identity Security and Why It Seems So Hard.”
Paddy Viswanathan is vice president of Cloud Solution Strategy at CyberArk.























