
The cybersecurity and identity-focused professionals gathered at CyberArk Impact 2022 need little convincing that Zero Trust is a solid framework to follow. After all, they’re the ones grappling with a daunting identity dilemma: how to keep corporate resources safe and manage growing cybersecurity debt while more than half of workforce identities can access sensitive data, machine identities outnumber human identities 45:1, and any one of these identities can be used to launch an attack chain.
Instead, these dedicated pros have come to Boston (or tuned in virtually) for the Identity Security event of the year to share their stories, hear from fellow experts, and explore innovations that offer a practical path toward that “trust nothing, verify everything” standard.
The Digital World Is Complex — Securing Identities Shouldn’t Be
Many CyberArk customers and partners recognized long ago that protecting the heart of their enterprise meant protecting privileged access. As strategic digitization, remote work, increasing cyber threats, surging compliance and cybersecurity insurance demands, and straight-up necessity began driving sweeping change across their businesses, these forward-looking security leaders were already thinking outside of the box and beyond the crumbling perimeter.
They recognize that securing identities everywhere they exist – in data centers and operational technologies, as well as in hybrid, multi-cloud and SaaS environments – is an ever-growing, multi-faceted challenge that necessitates intelligent privilege controls at the core, along with strong access management and identity management – all encompassed by data analysis and intelligence capabilities. But that doesn’t mean it has to be complicated.
This is what our CyberArk Identity Security vision is all about – using our security-first approach and deep privilege security expertise to make it easier for organizations to secure all human and machine identities accessing all resources from every location. Empowered, they can achieve measurable cyber-risk reduction, accelerate to the implementation of Zero Trust frameworks, and meet their strategic business goals.
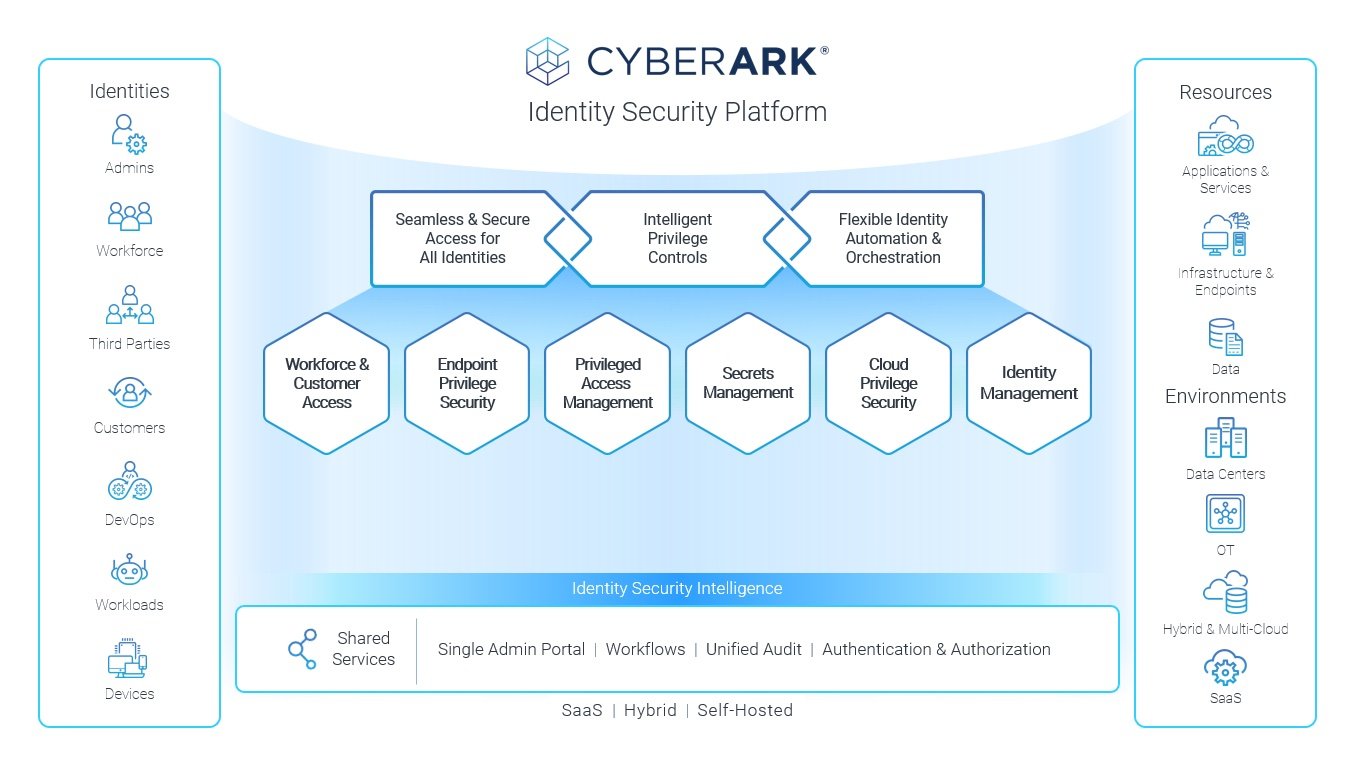
One Unified Identity Security Platform to Strengthen Cyber Resilience Across Six Key Areas
In today’s opening keynote, CyberArk Founder, Chairman and CEO Udi Mokady and members of the CyberArk executive leadership team outlined specific steps our company has taken over the past year to strengthen existing solutions and introduce new innovations to market that unify Identity Security across six key areas.
1. Workforce and Customer Access: One-quarter of professionals are projected to be fully remote by the end of 2022, and 42% follow a hybrid schedule today. The ability to access corporate resources from anywhere is a given. We’re here to help make authentication for all identities seamless and secure – whether that happens at home, the office, a conference or anywhere else. CyberArk Secure Web Sessions delivers advanced privileged access protection (think IT admin-level security) as employees access — and store their credentials for — sensitive business web and SaaS applications.
2. Endpoint Privilege Security: Our fastest-growing product line reflects heightened awareness and urgency to combat ransomware attacks at the endpoint, with layers of least privilege enforcement, application control, credential theft protection and strong multi-factor authentication for every escalation attempt. In addition to continued solution enhancements, we recently extended endpoint privilege security controls to support Linux – the platform of choice for 83.1% of developers today.
3. Privileged Access Management: Since CyberArk came to be, privileged access management (PAM) has addressed a major security challenge, and building a strong PAM foundation is how many organizations begin their Identity Security journey. We’ve continued to invest heavily in both our Self-Hosted and SaaS-based PAM solutions, and today organizations can comprehensively protect any type of privileged access with CyberArk – including Just-in-Time (JIT) vendor access to SaaS applications and JIT access to ephemeral VMs in cloud environments.
4. Secrets Management: The more organizations digitally transform, the more application secrets exist, and the more critical it becomes to simplify processes and scale protections. Our two new SaaS-based solutions were built for this. The just-announced CyberArk Secrets Hub is an integration with leading cloud-native secrets managers that gives organizations a way to centrally view, control and audit secrets without disrupting the developer experience. This means developers can keep using the cloud-native solutions they prefer, while security managers retain centralized control and can enforce unified policies over secrets using existing processes and infrastructure. (See “CyberArk Launches Secrets Hub for AWS Secrets Manager” for more details).
5. Identity Management: There are millions of identity-related events within any enterprise ecosystem – weeding through all of them (let alone prioritizing and responding to them) is a massive hurdle, and all the while, regulatory and compliance demands are mounting. To help enterprises overcome these challenges, we today introduced CyberArk Identity Flows, a single-pane identity orchestration solution that helps organizations automate identity management tasks and accelerate threat response through no-code app integrations and workflows. We also launched CyberArk Identity Compliance, a new standalone service that automates the access provisioning lifecycle and enforces strong controls – from discovery, to review, to certification – helping IT and security teams satisfy compliance, streamline audits and reduce risk.
6. Cloud Privilege Security: Our Identity Security vision extends to the cloud – an area in which 52% of organizations lack critical identity-centric security controls – and “Cloud Privilege Security” is our term for intelligent controls that help analyze, secure and monitor privileged access to the public cloud. Today, we announced CyberArk Secure Cloud Access, a new service that provisions Just-in-Time, least privilege access to cloud consoles, command lines and services, helping implement Zero Trust initiatives by reducing the risk of compromised privileged sessions and browser hijacking for DevOps and cloud operations teams.
The CyberArk platform is based on a set of foundational shared services, including the new Identity Security Intelligence service that provides continuous identity threat detection and prevention by automatically detecting anomalous user behavior and privileged access misuse for both workforce and privileged users. To learn more about how CyberArk continues to define and advance the Identity Security market, read today’s press releases.
We’re Firing on All Cylinders
The digital world is experiencing landmark changes – and landmark challenges, which are forcing organizations to rethink siloed approaches to privileged access management, access management and identity management. But we can harness these challenges and build a more secure world.
By embracing a unified Identity Security approach centered on intelligent privilege controls, organizations can better defend against their greatest source of risk and support Zero Trust adoption…
By consistently validating all access attempts.
By enforcing least privilege across the enterprise.
And by providing continuous identity threat detection and protection.
“We are firing on all cylinders at CyberArk,” said Mokady this morning. “We are investing heavily in strengthening our existing technologies. We are accelerating with new innovations. And we are just getting started.”
Thank you to all our customers and partners for being with us on this Identity Security journey, and welcome to those who have joined us this week at Impact 2022 as we prepare for cybersecurity’s next era.
For more details, read CyberArk Impact 2022 Delivers Big News and Innovation and That’s a Wrap for CyberArk Impact 2022 on Techspective.























