
Application whitelisting has been an advantageous technique to harden an organization’s endpoints against malware, unlicensed software, and other unknown or unauthorized software. When properly configured, whitelisting certainly has its benefits as it controls which applications and scripts can run and execute. However, traditional whitelisting technologies will limit the user to a binary ‘allow/deny’ mode. This approach may work just fine for smaller organizations that have only a handful of applications, but in large enterprises, this can be extremely challenging to support. The organization would need to either ‘allow the unknown’ and open themselves up to unnecessary risk – or – ‘deny the unknown’ and deal with disgruntled users and operational issues.
Attackers increasingly have sophisticated techniques. If an organization has something of significant value to attackers, then you can certainly expect that they’ll find ways to circumvent application whitelisting policies. Heuristic-based detection and scanning methods can help supplement a risk mitigation strategy against attacks initiated by these bypassing techniques – but – is that really enough to keep up with the very skilled and sophisticated cyber attackers that we see today? A defense in depth strategy at the endpoint with multiple layers of security controls is needed.
Misplaced Trust
When an organization leverages only the free and rudimentary tools for IT administrators to define which applications can and cannot be executed, they inadvertently become more susceptible to attacks that originate on the endpoint. Furthermore, trusting all the binaries that are signed off by the operating system comes with a certain level of risk. Over the years, researchers have come across many executable files that have the ability to very easily bypass some of these basic tools with relatively simple commands and run arbitrary scripts. Some of which were even able to fetch files and communicate over the internet – not good! These free tools can be a great foundational resource but additional security controls are needed to better improve an organization’s security posture.
Reality Meets Application Control
Expecting your IT administrator to be aware of all the applications that exist within a larger organization is unrealistic and nearly impossible in practice. Moreover, analyzing these applications and identifying which should be allowed to execute and which should be denied is equally as challenging. When an organization enables an application control solution, it often takes a whitelisting approach and therefore must specify exactly what is to be trusted. The most common tactic is to trust every binary that is signed off by the operating system vendor – but – not all processes (e.g. child processes) that originated from the trusted process are considered to be fully trustworthy. This is particularly important when you consider the techniques of modern malware that leverage tools like PowerShell to pull code (e.g. Mimikatz) from online source code repositories and execute in memory – thereby bypassing many Anti-Virus, malware detection or whitelisting solutions. Being limited to only ‘allowing’ or ‘denying’ within PowerShell is certainly not the ideal situation.
A more proactive approach is to provide application “greylisting” which allows lesser known applications to run in a restricted mode based on policy whereby they are allowed to run but are for example, denied access to the internet, unable to spawn processes and forced to run at a lower privilege. Operating in a restricted mode allows flexibility to the end user but prevents the applications from accessing corporate resources and system resources as part of a targeted attack.
CyberArk Provides Defense in Depth for Application Control
CyberArk Endpoint Privilege Manager delivers several layers of security beyond what some of the basic, UAC software restricting tools can provide and in so doing is aligned with guidance from NIST Special Publication 800-167, Guide to Application Whitelisting. With CyberArk Endpoint Privilege Manager, users can define whitelists and greylists with flexible rules based upon any combination of various file parameters and not just those based on the file hash, path or publisher (which can easily be sidestepped by a few simple actions). With Endpoint Privilege Manager, an IT organization can provide the level of granularity that allows for specific users on specific machines to run PowerShell, with a pre-defined level of privilege (e.g. standard user, specific privileges [i.e. custom token], etc.).
Additionally, Endpoint Privilege Manager also supports a full range of trusted sources, providing the ability to manage a very large number of the executables within larger-sized organizations (e.g. any file distributed by a corporate software distribution system like System Center Configuration Manager could be defined as a trusted source just by one simple rule). Lastly, this solution provides deep integrations with third-party file reputation systems to help IT administrators determine legitimate applications versus what’s considered to be potentially harmful. The image below shows Endpoint Privilege Manager blocking an unknown .vbs script from running on the endpoint, by using Bginfo.exe (a known executable file signed by the OS vendor that can bypass whitelisting) as the executable host:
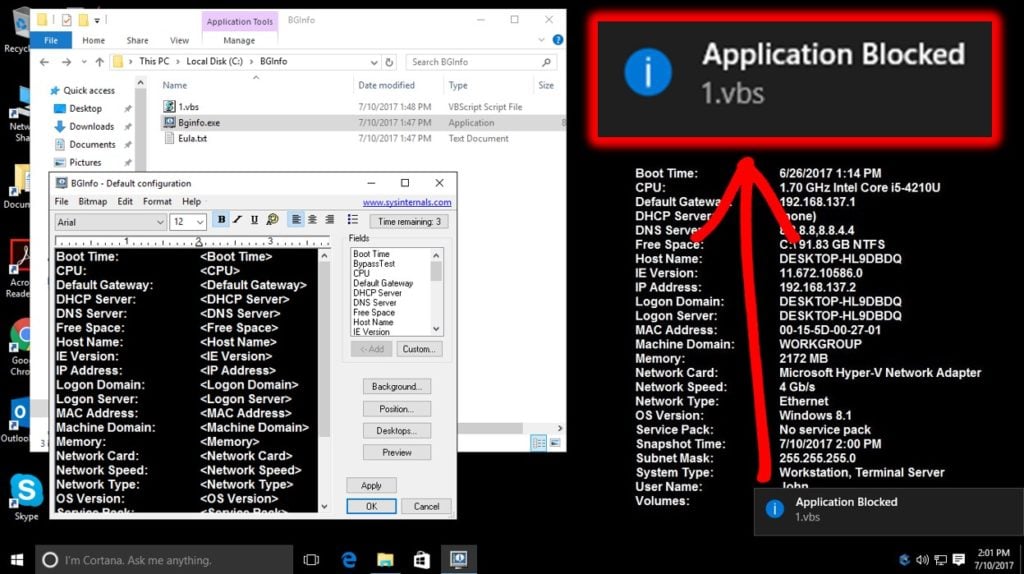
Minimizing the endpoint attack surface is top of mind for all IT Security teams and taking a layered approach in securing your endpoints by coupling both privilege management and application control is an essential step in stopping common endpoint attack vectors that organizations often fall victim to. Our CyberArk Labs Team has demonstrated that a combination of privilege management and application control is 100% effective in protecting against both ransomware and unknown malware.
To learn more about how CyberArk solutions can block and contain threats at the endpoint, download the Endpoint Privilege Manager Solution Brief or request a demo.























