
The No. 1 cybersecurity challenge across U.S. critical infrastructure is that many organizations haven’t adopted fundamental security controls. Not entirely unsurprising, the finding comes from the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) recently released Cross-Sector Cybersecurity Performance Goals (CPGs) report. Its intent is to establish a uniform baseline of fundamental cybersecurity practices for critical infrastructure entities, particularly small-to-midsize businesses (SMBs) seeking risk-prioritized guidance.
The clock started running on the drafting of the report in July 2021 when the Biden administration issued a National Security Memorandum (NSM) outlining steps to safeguard the country’s critical infrastructure. The memorandum called for CISA, along with the National Institute of Standards and Technology (NIST), to produce clear goals compatible across all critical infrastructure sectors.
CPGs and Adoption: Intended to be Accessible, Voluntary
The 37 individual CPGs are small steps that together have the potential to equate to one giant leap for cybersecurity maturity and consistency across the critical infrastructure sectors. The CISA report does note, “The CPGs do not reflect an all-encompassing cybersecurity program — rather, they are a minimum set of practices that organizations should implement and aim to help CI entities, particularly small and medium organizations, get started on their path towards a strong cybersecurity posture.”
In the report’s opening letter, CISA Director Jen Easterly writes, “Ultimately, our hope is that the CPGs will not only serve as a strong foundation for improving cybersecurity across our nation’s critical infrastructure sectors but also as a baseline of security outcomes that merit the trust of the American people.” That is a giant leap.
According to the report, the CPGs were developed by CISA along with hundreds of public and private sector partners, including federal agencies. Although adoption of the CPGs is voluntary, they serve as an affordable quick-start guide to rapidly improve cybersecurity hygiene.
Guidance for SMBs
The need to develop the CPGs is perhaps felt most by SMBs — organizations that are prone to be strapped by limited resources to prepare for and defend against cyber threats.
The conundrum for these businesses is, of course, which cybersecurity practices and initiatives to prioritize and put resources toward first. Where to start can be daunting and confusing, regardless of whether you’re working with a limited or large budget —and every size in between. Considering identity is the primary mechanism enabling IT operations — and a primary target for attackers — Identity Security controls are emerging as a quick win for organizations with limited resources. That’s why it’s not surprising that “account security” is the first category of the CISA CPGs. It’s like building a house —you’re going to need foundational support before trying to put the roof on. It comes down to fundamentals.
Combining Constructional Forces for Foundational Cybersecurity
The 37 foundational CPGs span eight risk categories, each of which includes four elements: TTP or risk addressed, scope, recommended actions and outcomes. Identity Security controls can help address many of the CPGs, especially in the report’s first category, account security, which includes the following seven CPGs:
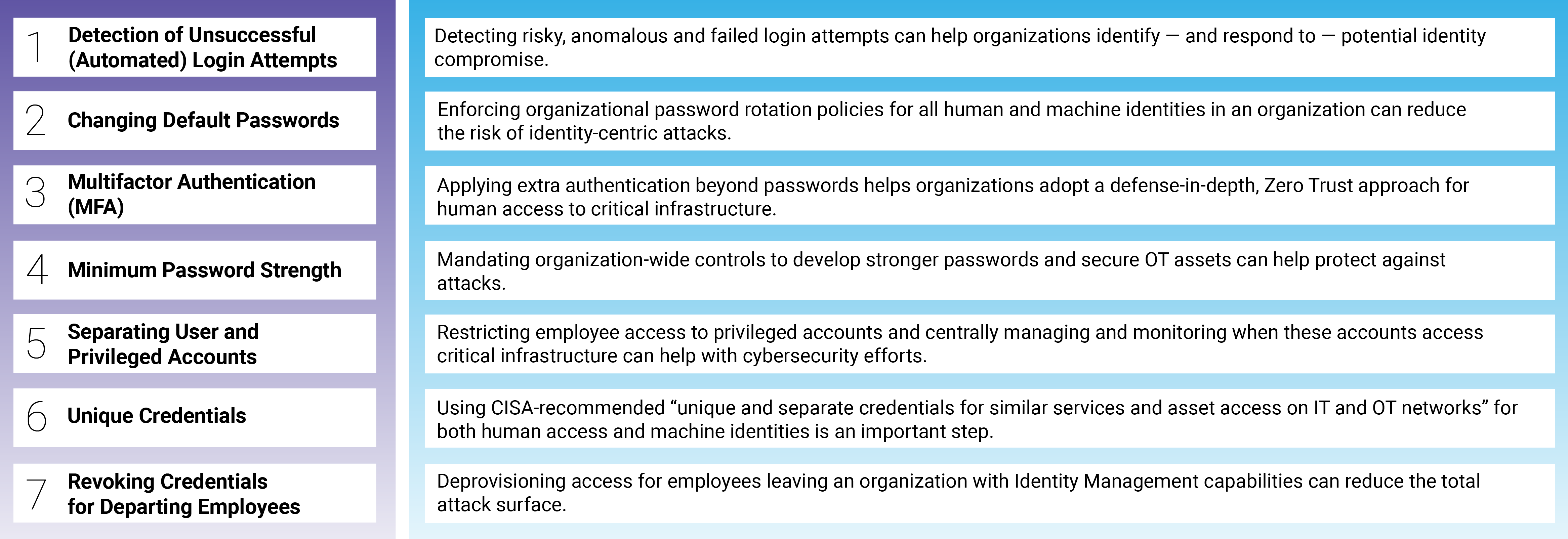
According to the report, the initial CPGs are just a start and are not considered to be comprehensive. They will be updated every six to 12 months. The next steps in 2022 include CISA and Sector Risk Management Agencies (SRMAs) combining forces to use the CPGs as a foundation for constructing “sector-specific goals.”
Interested in learning how Identity Security capabilities can help address the CPGs? Schedule a meeting or explore the CyberArk Blueprint, a vendor-agnostic framework for defining a roadmap for Identity Security success.
To learn more, register for our Dec. 7, 2022 webinar, “CyberArk’s Perspective: New CISA Cybersecurity Performance Goals for Critical Infrastructure.”























