
For years, separating day-to-day user activity from administrative tasks through secondary accounts was considered a security best practice. But as identity threats grow more sophisticated and cloud environments become more dynamic, this static model is showing its age. Today, modern identity security demands a shift—one that zero standing privileges (ZSP) are designed to deliver.
The secondary account approach, once considered best practice, is now challenged by modern identity security models like ZSP. This modern approach to performing administrative or privileged tasks effectively addresses security and compliance requirements to reduce the risk associated with persistent permissions.
Modern alternative to secondary accounts
Modern identity security demands agility, precision, and minimal exposure. ZSP exemplifies this shift by enabling time-bound access tailored to the task at hand. Instead of relying on persistent entitlements or static accounts, ZSP dynamically assembles the necessary permissions—whether accessing cloud services or infrastructure—and dissolves them once the task is complete.
Solutions like CyberArk Secure Cloud Access (SCA) and Secure Infrastructure Access (SIA) operationalize this model through dynamic privilege orchestration across diverse environments. This approach not only reduces the attack surface but also aligns with the principles of least privilege and just-in-time (JIT) access, offering a scalable framework for securing modern enterprises.
When organizations implement ZSP, even compromised credentials leave behind a zero-attack surface since no privileged standing access exists outside the established timeframe. As a result, the risk of privilege escalation or lateral movement is significantly reduced.
Security teams can log, record, and monitor every action with granular control and auditing capabilities, helping to support complete visibility into what users do with their elevated privileges. These auditing and monitoring capabilities can help organizations meet compliance requirements like GDPR, PCI-DSS, or HIPAA. It also offers a better experience, allowing users to select the specific role required to perform administrative tasks without the need to authenticate using a separate secondary account.

How zero standing privileges support modern security goals
Other ZSP benefits can include:
- Fewer accounts: A standard account can be configured to securely assume any roles required.
- On-demand access: Privileges are granted only when requested, reducing the risk of credential theft and lateral movement.
- Hybrid and multi-cloud scalability: No standing privileges across cloud service providers (CSPs).
- Reduced attack surface: Eliminating persistent privileges, minimizing the potential impact of compromised credentials.
- Enhanced security posture: Ensuring access is granted based on the current context and need.
- Operational efficiency: Streamlining access management by automating privilege assignment and revocation.
- Workflows for automation: Reducing the risk of human error and improving efficiency in granting access. Automated workflows can help ensure elevated privileges are used only for legitimate purposes, akin to JIT access.
How ZSP works in cloud environments
In the cloud, distinguishing between admin and non-admin accounts is difficult. Users may have access to multiple workspaces and a broad range of resources across numerous CSPs, assuming roles with varying entitlements (administrative or non-administrative). With ZSP, an account can assume or request any role, when required, for a specified time, with permissions automatically added and subsequently removed. ZSP effectively replaces the need for secondary accounts.
ZSP can be used for various scenarios beyond elevated access to administrative tasks. It can be applied to all users in the environment, since each user in a cloud environment is considered privileged. Cloud workspaces, like an Azure subscription or GCP Project, can remove standing access for any user involved. This results in a reduced attack surface, since no entitlements exist until a user logs in, selects a role or requests on-demand access, which requires approval.
Additional use cases include break-glass access for production workspaces and DevSecOps environments. In these contexts, roles are defined with explicit permissions per workspace, such as sandbox, development, testing, staging, and production.
Here’s a comparison of secondary accounts and ZSP:
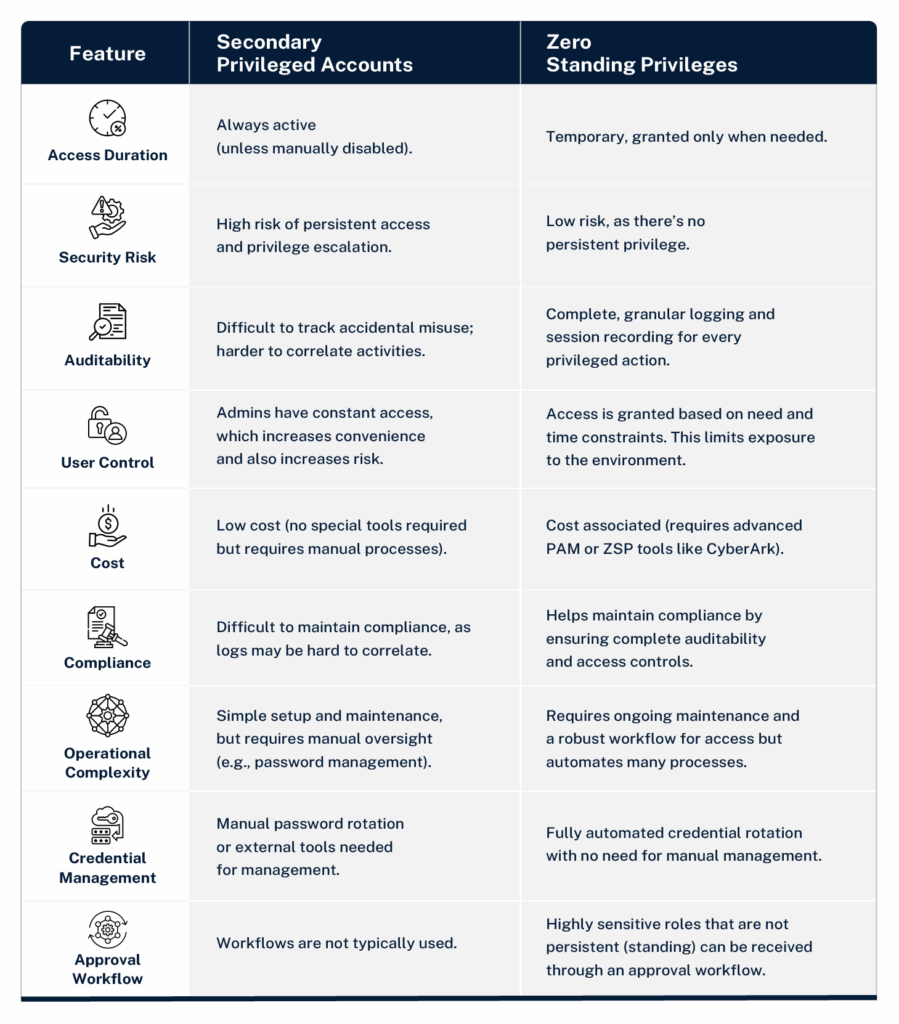
The creation of privileged accounts aimed to separate user identities from their associated privileges. However, modern organizations require dynamic, context-driven solutions to address privileges for each unique identity. ZSP provides this agility, assigning privileges when needed and revoking them immediately after.
As a result, using a privileged secondary account is no longer necessary in many scenarios—especially in cloud environments.
Putting ZSP into practice
Discover how enterprises are operationalizing zero standing privileges in alignment with CSPs’ well-architected frameworks—explore these CyberArk resources:
- Best Practices for Adopting and Implementing Secure Cloud Access (SCA) (Community Article)—foundational guidance for aligning teams and workflows around ZSP
- Best Practices for Adopting and Implementing SCA (Supplemental Guide)—deeper context on cloud workspace strategies and entitlement management
- CyberArk SCA Policy Best Practices—guidance for building access policies that support ZSP and least privilege
Mark Szalkiewicz is a cloud solution strategy architect, Mike Bykat is an IT and DEV solution architect director, and Prashant Tyagi is a cloud technical senior director at CyberArk.























